Network Planning
Network Plane in the Single-Node Scenario Where HA Is Not Required
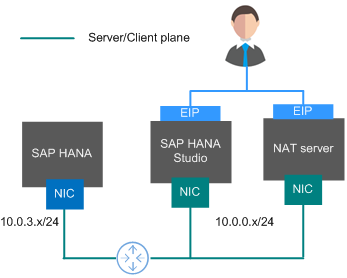
Figure 1 shows the network plane planning in the single-node scenario where HA is not required.
The network segments and IP addresses are for reference only.
Planning description
- In this scenario, each node uses only one NIC to form the network communication plane.
- Table 1 shows the planned network.
Table 1 Network planning in the single-node scenario where HA is not required Parameter
Description
Example Value
IP address of the server/client plane
Allows an SAP HANA node to communicate with service software (such as SFS and ERP) or SAP HANA Studio client software.
SAP HANA node: 10.0.3.2
SAP HANA Studio: 10.0.0.102
NAT server: 10.0.0.202
Elastic IP address
Allows you to access SAP HANA Studio and NAT server.
Automatically allocated
Network Plane in the Single-Node Scenario Where HA Is Required
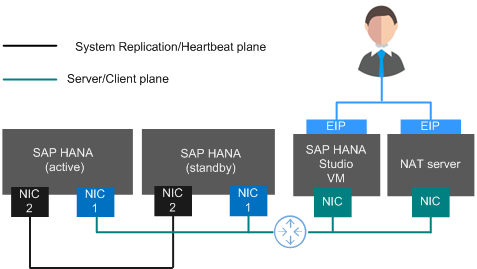
Figure 2 shows the network plane planning in the single-node scenario where HA is required.
- The network segments and IP addresses are for reference only.
- Figure 2 applies to performing active/standby switchovers using scripts. If active/standby switchovers are manually performed, no heartbeat plane NIC is required.
- IP addresses of the server plane (server/client plane IP address) and the active/standby internal communication plane (System Replication communication plane IP address and heartbeat plane IP address) must belong to different subnets.
Planning description
- The active and standby SAP HANA nodes both have an NIC1 and an NIC2 card. The two NIC1 cards are in the same network segment and belong to the service/client plane. The two NIC2 cards are in another network segment and belong to the system replication/heartbeat plane.
- Table 2 shows the planned network.
Table 2 Network planning in the single-node scenario where HA is required Parameter
Description
Example Value
IP address of the server/client plane
Specifies the IP address of the primary NIC plane. Allows an SAP HANA node to communicate with service software (such as SFS and ERP) or SAP HANA Studio client software.
SAP HANA node: 10.0.3.2 to 10.0.3.3
SAP HANA node floating IP address: 10.0.3.103
SAP HANA Studio: 10.0.0.102
NAT server: 10.0.0.202
IP address of the System Replication communication plane
Specifies the IP address of the plane that SAP HANA nodes use to implement System Replication.
SAP HANA node: 10.0.4.2 to 10.0.4.3
IP address of the heartbeat plane
Specifies the IP address of the plane that SAP HANA nodes use to transmit heartbeat signals to perform automatic active/standby switchovers when a node is faulty.
Elastic IP address
Allows you to access SAP HANA Studio and NAT server.
Automatically allocated
Security Group Rules
- The network segments and IP addresses are for reference only. The following security group rules are recommended practices. You can configure your own security group rules as you need.
- In the following table, ## stands for the SAP HANA instance ID, such as 00. Ensure that this ID is the same as the instance ID specified when you install the SAP HANA software.
- For more information about specific ports and security group rules to be accessed by SAP, see SAP official documents.
|
Source/Destination |
Protocol |
Port Range |
Description |
|---|---|---|---|
|
Inbound |
|||
|
10.0.0.0/24 |
TCP |
3##13 |
Allows SAP HANA Studio to access SAP HANA. |
|
10.0.0.0/24 |
TCP |
3##15 |
Provides ports for the service plane. |
|
10.0.0.0/24 |
TCP |
3##17 |
Provides ports for the service plane. |
|
10.0.0.0/24 |
TCP |
5##13 |
Allows SAP HANA Studio to access sapstartsrv. |
|
10.0.0.0/24 |
TCP |
22 |
Allows SAP HANA to be accessed using SSH. |
|
10.0.0.0/24 |
TCP |
43## |
Allows access to XS Engine from the 10.0.0.0/24 subnet using HTTPS. |
|
10.0.0.0/24 |
TCP |
80## |
Allows access to XS Engine from the 10.0.0.0/24 subnet using HTTP. |
|
10.0.0.0/24 |
TCP |
8080 (HTTP) |
Allows Software Update Manager (SUM) to access SAP HANA using HTTP. |
|
10.0.0.0/24 |
TCP |
8443 (HTTPS) |
Allows Software Update Manager (SUM) to access SAP HANA using HTTPS. |
|
10.0.0.0/24 |
TCP |
1128-1129 |
Allows access to SAP Host Agent using SOAP/HTTP. |
|
Automatically specified by the system |
All |
All |
Security group rule created by the system by default It enables ECSs in the same security group to communicate with each other. |
|
Outbound |
|||
|
All |
All |
All |
Security group rule created by the system by default Allows all peers to access SAP HANA. |
|
Source/Destination |
Protocol |
Port Range |
Description |
|---|---|---|---|
|
Inbound |
|||
|
0.0.0.0/0 |
TCP |
3389 |
Allows users to access SAP HANA Studio using RDP. This rule is required only when SAP HANA Studio is deployed on a Windows ECS. |
|
0.0.0.0/0 |
TCP |
22 |
Allows users to access SAP HANA Studio using SSH. This rule is required only when SAP HANA Studio is deployed on a Linux ECS. |
|
Automatically specified by the system |
All |
All |
Security group rule created by the system by default It enables ECSs in the same security group to communicate with each other. |
|
Outbound |
|||
|
All |
All |
All |
Security group rule created by the system by default Allows all peers to access SAP HANA Studio. |
|
Source/Destination |
Protocol |
Port Range |
Description |
|---|---|---|---|
|
Inbound |
|||
|
0.0.0.0/0 |
TCP |
22 |
Allows users to access the NAT server using SSH. |
|
10.0.3.0/24 |
TCP |
80 (HTTP) |
Allows users to access the NAT server using HTTP. |
|
10.0.3.0/24 |
TCP |
443 (HTTPS) |
Allows users to access the NAT server using HTTPS. |
|
Automatically specified by the system |
All |
All |
Security group rule created by the system by default It enables ECSs in the same security group to communicate with each other. |
|
Outbound |
|||
|
10.0.3.0/24 |
TCP |
22 (SSH) |
Allows the NAT server to access the 10.0.3.0 subnet using SSH. |
|
0.0.0.0/0 |
TCP |
80 (HTTP) |
Allows the NAT server to access any network where VPC instances reside using HTTPS. |
|
0.0.0.0/0 |
TCP |
443 (HTTPS) |
Allows the NAT server to access any network where VPC instances reside using HTTPS. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot