หน้านี้ยังไม่พร้อมใช้งานในภาษาท้องถิ่นของคุณ เรากำลังพยายามอย่างหนักเพื่อเพิ่มเวอร์ชันภาษาอื่น ๆ เพิ่มเติม ขอบคุณสำหรับการสนับสนุนเสมอมา
Planning
Before deploying SAP S/4HANA, you need to plan required resources.
ECS Specifications
Table 1 describes the specifications of SAP-certified ECSs.
|
ECS Type |
Flavor |
vCPUs |
Memory (GB) |
|---|---|---|---|
|
Memory-optimized |
m6.large.8 |
2 |
16 |
|
m6.xlarge.8 |
4 |
32 |
|
|
m6.2xlarge.8 |
8 |
64 |
|
|
m6.4xlarge.8 |
16 |
128 |
|
|
m6.8xlarge.8 |
32 |
256 |
|
|
General Computing-plus |
c6.large.4 |
2 |
8 |
|
c6.xlarge.4 |
4 |
16 |
|
|
c6.2xlarge.4 |
8 |
32 |
|
|
c6.3xlarge.4 |
12 |
48 |
|
|
c6.4xlarge.4 |
16 |
64 |
|
|
c6.6xlarge.4 |
24 |
96 |
|
|
c6.8xlarge.4 |
32 |
128 |
Requirements on OSs and Disks
Table 2 and Table 3 lists the requirements on OSs and disks.
|
Item |
Specifications |
|---|---|
|
OS |
|
|
Disk |
Type |
Sharing Mode |
Format |
Size |
|---|---|---|---|---|
|
OS disk |
High I/O |
Non-shared disk |
ext3 |
The size must be greater than or equal to that required by the image. |
|
Sapmnt disk |
High I/O |
Non-shared disk |
xfs |
> 100 GB |
|
Usrsap disk |
High I/O |
Non-shared disk |
xfs |
50 GB |
|
Swap disk |
High I/O |
Non-shared disk |
xfs |
64 GB |
 NOTE:
NOTE:
SAS hard disks have high I/O while SSD hard disks have ultra-high I/O.
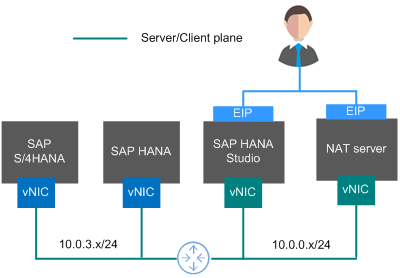
Network Plane Planning
Figure 1 shows the network plane.
 NOTE:
NOTE:
The network segments and IP addresses are for reference only.
In this scenario, only one NIC is used by each ECS for network communication.
Table 4 shows the planned network information.
Security Group Planning
Table 5, Table 6, Table 7 and Table 8 show the security group rules of SAP HANA, SAP S/4HANA, SAP HANA Studio, and NAT Server, respectively.
 NOTE:
NOTE:
- The network segments and IP addresses are for reference only. The following security group rules are recommended practices. You can configure your own security group rules as needed.
- In the following table, ## stands for the SAP HANA instance ID, such as 00. Ensure that this ID is the same as the instance ID specified when you install the SAP HANA software.
- For more information about specific ports and security group rules to be accessed by SAP, see SAP official documents.
|
Source/Destination |
Protocol |
Port Range |
Description |
|---|---|---|---|
|
Inbound |
|||
|
10.0.0.0/24 |
TCP |
3##13 |
Allows SAP HANA Studio to access SAP HANA. |
|
10.0.0.0/24 |
TCP |
3##15 |
Provides ports for the service plane. |
|
10.0.0.0/24 |
TCP |
3##17 |
Provides ports for the service plane. |
|
10.0.0.0/24 |
TCP |
5##13 |
Allows SAP HANA Studio to access sapstartsrv. |
|
10.0.0.0/24 |
TCP |
22 |
Allows SAP HANA to be accessed using SSH. |
|
10.0.0.0/24 |
TCP |
43## |
Allows access to XS Engine from the 10.0.0.0/24 subnet using HTTPS. |
|
10.0.0.0/24 |
TCP |
80## |
Allows access to XS Engine from the 10.0.0.0/24 subnet using HTTP. |
|
10.0.0.0/24 |
TCP |
8080 (HTTP) |
Allows Software Update Manager (SUM) to access SAP HANA using HTTP. |
|
10.0.0.0/24 |
TCP |
8443 (HTTPS) |
Allows Software Update Manager (SUM) to access SAP HANA using HTTPS. |
|
10.0.0.0/24 |
TCP |
1128-1129 |
Allows access to SAP Host Agent using SOAP/HTTP. |
|
Automatically specified by the system |
All |
All |
Security group rule created by the system by default Allows ECSs in the same security group to communicate with each other. |
|
Outbound |
|||
|
All |
All |
All |
Security group rule created by the system by default Allows SAP HANA to access all peers. |
|
Source/Destination |
Protocol |
Port Range |
Description |
|---|---|---|---|
|
Inbound |
|||
|
10.0.0.0/24 |
TCP |
32## |
Allows SAP GUI to access SAP S/4HANA. |
|
10.0.0.0/24 |
TCP |
3##13 |
Allows SAP HANA Studio to access SAP S/4HANA. |
|
10.0.0.0/24 |
TCP |
3##15 |
Provides ports for the service plane. |
|
10.0.3.0/24 |
TCP |
5##13 to 5##14 |
Allows ASCS to access SAP application server. |
|
10.0.3.0/24 |
TCP |
33## and 48## |
Ports used by CPIC and RFC |
|
10.0.0.0/24 |
TCP |
22 |
Allows SAP S/4HANA to be accessed using SSH. |
|
10.0.3.0/24 |
UDP |
123 |
Allows other servers to synchronize time with SAP S/4HANA ECSs. |
|
Determined by the public cloud |
All |
All |
Security group rule created by the system by default Allows ECSs in the same security group to communicate with each other. |
|
Outbound |
|||
|
All |
All |
All |
Security group rule created by the system by default Allows SAP S/4HANA ECSs to access all peers. |
|
Source/Destination |
Protocol |
Port Range |
Description |
|---|---|---|---|
|
Inbound |
|||
|
0.0.0.0/0 |
TCP |
3389 |
Allows users to access SAP HANA Studio using RDP. This rule is required only when SAP HANA Studio is deployed on a Windows ECS. |
|
0.0.0.0/0 |
TCP |
22 |
Allows users to access SAP HANA Studio using SSH. This rule is required only when SAP HANA Studio is deployed on a Linux ECS. |
|
Automatically specified by the system |
All |
All |
Security group rule created by the system by default Allows ECSs in the same security group to communicate with each other. |
|
Outbound |
|||
|
All |
All |
All |
Security group rule created by the system by default Allows all peers to access SAP HANA Studio. |
|
Source/Destination |
Protocol |
Port Range |
Description |
|---|---|---|---|
|
Inbound |
|||
|
0.0.0.0/0 |
TCP |
22 |
Allows users to access the NAT server using SSH. |
|
10.0.3.0/24 |
TCP |
80 (HTTP) |
Allows access to instances in the same VPC using HTTP. |
|
10.0.3.0/24 |
TCP |
443 (HTTPS) |
Allows access to instances in the same VPC using HTTPS. |
|
Automatically specified by the system |
All |
All |
Security group rule created by the system by default Allows ECSs in the same security group to communicate with each other. |
|
Outbound |
|||
|
10.0.3.0/24 |
TCP |
22 (SSH) |
Allows the NAT server to access the 10.0.3.0 subnet using SSH. |
|
0.0.0.0/0 |
TCP |
80 (HTTP) |
Allows instances in a VPC to access any network. |
|
0.0.0.0/0 |
TCP |
443 (HTTPS) |
Allows instances in a VPC to access any network. |
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot