Tag-based Fine-Grained Authorization
Scenarios
After creating a custom policy for the SWR Enterprise Edition on the IAM console, you can add tags for namespaces and repositories. Use policies and tags together can implement fine-grained authorization on resources of the SWR Enterprise Edition, ensuring controllable and secure resource permissions.
Prerequisites
You have created namespace tags.
Procedure
- Create one or more policies on the IAM console.
For example, you can create a policy named policy77r463. Table 1 describes the parameters.
Table 1 Example policy configuration Parameter
Description
Example Value
Policy type
You can select Allow or Deny.
Allow
Cloud services
Cloud services that the current policy will be applied to
SWR
Action
Actions that the current policy will be applied to. You can select one or more actions.
swr:repository:downloadArtifact
Resource type
- You can select Specific or All.
- For details about specific resources, see Resource Type.
If you select Specific, click Specify resource path and configure the resource path SWR:*:*:repository:*/{namespace-name}.
Request condition
- Tag of the current policy. A tag is a key-value pair.
- For details about request conditions, see Request Conditions.
This policy is created for SWR, so select Service-level condition keys for Condition Key. Configure the parameters as follows:
TagKey: test
Operator: StringEquals
Value: aaa
The following policy is in JSON format:{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "swr:repository:downloadArtifact" ], "Resource": [ "SWR:*:*:repository:*/{namespace-name}" ], "Condition": { "StringEquals": { "g:ResourceTag/test": [ "aaa" ] } } } ] }Figure 1 Creating a policy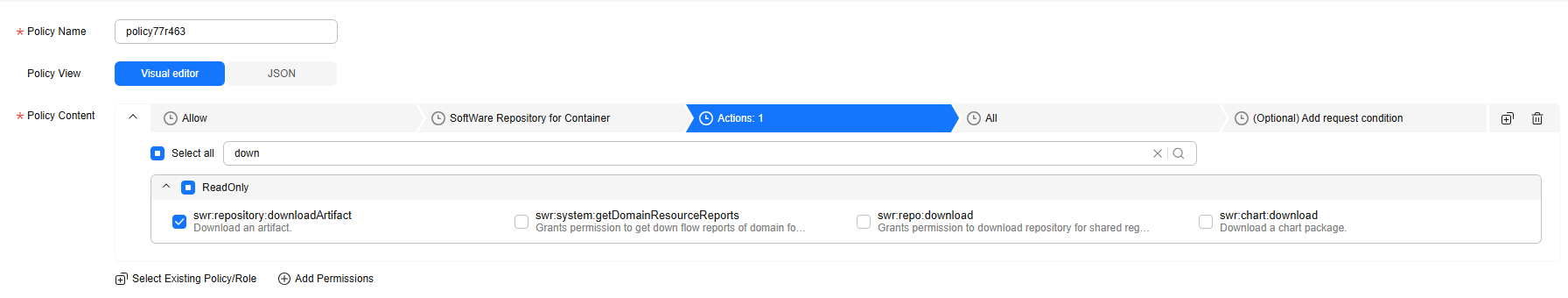
This policy applies to SWR. You can attach this policy to a user or user group of this service. After the policy is applied, the user or user group can download the artifacts from a repository in the namespace-name namespace with the test=aaa tag.
If a user or user group wants to download an image from the image repository, SWR Enterprise Edition will extract the tag of the user or user group and verifies it with test=aaa. If the tag matches, the user or user group is allowed to perform the operation. Otherwise, the operation will fail.
- Attach policy77r463 generated in 1 to a user or user group. For details, see Creating a User Group and Granting Permissions. Add the test=aaa tag to a namespace, for example, the {namespace-name} namespace. For details, see Adding a Tag to a Namespace.
- Verify that the user or user group in 2 can download artifacts in the {namespace-name} namespace.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





