Peer Authentication
ASM enables communication between service instances using a Policy Enforcement Point (PEP) tunnel. Peer authentication defines how traffic will be tunneled (or not) to a service instance. By default, service instances that have sidecars injected communicate with each other through the PEP tunnel. Traffic is automatically encrypted using TLS. Peer authentication controls the mode of two-way authentication on the target workload.
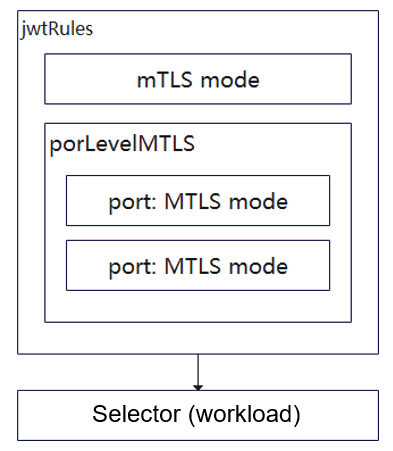
Creating a Peer Authentication Policy
Create a peer authentication policy using YAML.
- Log in to the UCS console. In the navigation pane, choose Service Meshes. Click the name of the target service mesh to go to its details page.
- In the navigation pane, choose Service Security > Peer Authentication.
- Click Create from YAML in the upper right corner.
- Enable two-way authentication for the service. The service will allow access from the invoker and only process requests encrypted using TLS.
apiVersion: security.istio.io/v1beta1 kind: PeerAuthentication # Set the service security type to peer authentication. metadata: name: peer-policy # Name the peer authentication policy. namespace: weather # Set the namespace to weather. spec: selector: matchLabels: app: forecast # Add a label key-value pair. mtls: mode: STRICTTo complete the unified authentication policy, configure the parameters as follows:
apiVersion: security.istio.io/v1beta1 kind: PeerAuthentication metadata: name: mesh_tls namespace: istio-system spec: mtls: mode: STRICT
Updating a Peer Authentication Policy
- Log in to the UCS console. In the navigation pane, choose Service Meshes.
- Click the name of the target service mesh to go to its details page.
- In the navigation pane, choose Service Security > Peer Authentication.
- Locate the authentication policy to be updated and click Edit YAML in the Operation column.
- Update the peer authentication policy based on the site requirements. For example, to update the unified authentication policy to the unified namespace authentication policy, configure the parameters as follows:
apiVersion: security.istio.io/v1beta1 kind: PeerAuthentication metadata: name: ns_weather_tls namespace: weather spec: mtls: mode: STRICT
Deleting a Peer Authentication Policy
Deleted peer authentication policies cannot be recovered. Deleting a peer authentication policy will not affect the running of associated services.
- Log in to the UCS console. In the navigation pane, choose Service Meshes.
- Click the name of the target service mesh to go to its details page.
- In the navigation pane, choose Service Security > Peer Authentication.
- Locate the authorization policy to be deleted and click Delete in the Operation column.
- In the dialog box displayed, click Yes.
Case
Update the unified authentication policy to the unified namespace authentication policy.
apiVersion: security.istio.io/v1beta1
kind: PeerAuthentication
metadata:
name: ns_weather_tls
namespace: weather
spec:
mtls:
mode: STRICT
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





