Configuring Public Access for a RocketMQ Instance
To access a RocketMQ instance over a public network, enable public access and configure EIPs for the instance. If you no longer need public access to the instance, disable it.
Notes and Constraints
Only IPv4 EIPs can be bound to RocketMQ instances.
Prerequisite
You can change the public access setting only when the RocketMQ instance is in the Running state.
Enabling Public Access
- Log in to the console.
- Click
 in the upper left corner to select a region.
in the upper left corner to select a region.
DMS for RocketMQ instances in different regions cannot communicate with each other over an intranet. Select a nearest location for low latency and fast access.
- Click
 and choose Middleware > Distributed Message Service for RocketMQ to open the console of DMS for RocketMQ.
and choose Middleware > Distributed Message Service for RocketMQ to open the console of DMS for RocketMQ. - Click a RocketMQ instance to go to the instance details page.
- Click
 next to Public Access in the Connection area.
next to Public Access in the Connection area. - Click
 , in the Elastic IP Address area, select IP addresses as prompted, and click
, in the Elastic IP Address area, select IP addresses as prompted, and click  .
.
If no EIP exists in the Elastic IP Address drop-down list box, or the EIPs are insufficient, click Create Elastic IP to create an EIP on the page that is displayed. After the EIP is created, return to the RocketMQ console, click
 next to Elastic IP Address, and select the new EIP from the drop-down list.Figure 1 Enabling public access
next to Elastic IP Address, and select the new EIP from the drop-down list.Figure 1 Enabling public access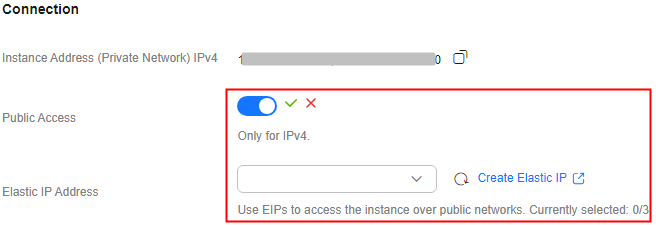
After public access is enabled, Instance Address (Public Network) is displayed for a v4.8.0 RocketMQ instance , and Instance Address (Public Network) (TCP) and gRPC Connection Address (Public Network) (gRPC) are displayed for a v5.x RocketMQ instance.
Figure 2 Public network connection addresses (RocketMQ 4.8.0) Figure 3 Public network connection addresses (RocketMQ 5.x)
Figure 3 Public network connection addresses (RocketMQ 5.x)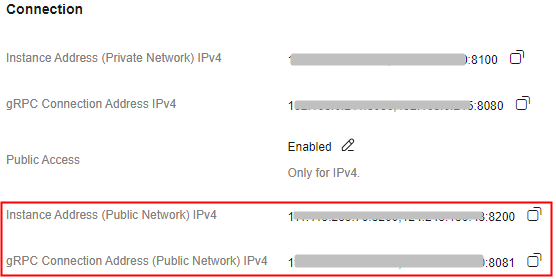
After public access is enabled, modify security group rules before attempting to access the RocketMQ instance.
Table 1 Security group rules (RocketMQ 4.8.0) Direction
Protocol
Port
Source
Description
Inbound
TCP
8200
IP address or IP address group of the RocketMQ client
The port is used for public network access to metadata nodes using TCP.
Inbound
TCP
10101-10199
The port is used for public access to service nodes using TCP.
Table 2 Security group rules (RocketMQ 5.x) Direction
Protocol
Port
Source
Description
Inbound
TCP
8200
IP address or IP address group of the RocketMQ client
The port is used for public network access to instances using TCP.
Inbound
TCP
8081
The port is used for public network access to instances using gRPC.
Inbound
TCP
10101
The port is used for public access to service nodes using TCP.
Disabling Public Access
- Log in to the console.
- Click
 in the upper left corner to select a region.
in the upper left corner to select a region.
DMS for RocketMQ instances in different regions cannot communicate with each other over an intranet. Select a nearest location for low latency and fast access.
- Click
 and choose Middleware > Distributed Message Service for RocketMQ to open the console of DMS for RocketMQ.
and choose Middleware > Distributed Message Service for RocketMQ to open the console of DMS for RocketMQ. - Click a RocketMQ instance to go to the instance details page.
- Click
 next to Public Access in the Connection area.
next to Public Access in the Connection area. - Click
 and then
and then  to disable public access.
After public access is disabled, modify security group rules before attempting to access the RocketMQ instance over a private network.
to disable public access.
After public access is disabled, modify security group rules before attempting to access the RocketMQ instance over a private network.Table 3 Security group rules (RocketMQ 4.8.0) Direction
Protocol
Port
Source
Description
Inbound
TCP
8100
IP address or IP address group of the RocketMQ client
The port is used for private network access to metadata nodes using TCP.
Inbound
TCP
10100–10199
The port is used for private access to service nodes using TCP.
Table 4 Security group rules (RocketMQ 5.x) Direction
Protocol
Port
Source
Description
Inbound
TCP
8100
IP address or IP address group of the RocketMQ client
The port is used for private network access to instances using TCP.
Inbound
TCP
8080
The port is used for private network access to instances using gRPC.
Inbound
TCP
10100
The port is used for private access to service nodes using TCP.
Related Documents
- To configure public access by calling an API, see Modifying Instance Information.
- A public IP address is required to enable public access. If no IP address is available from the drop-down list, create an EIP first. For details, see Assigning an EIP.
- To learn about EIP charging, see Billing Items.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





