Viewing an Application
The Application List tab displays all applications of the current ServiceComb engine. You can search for the target application by application name, or filter applications by environment.
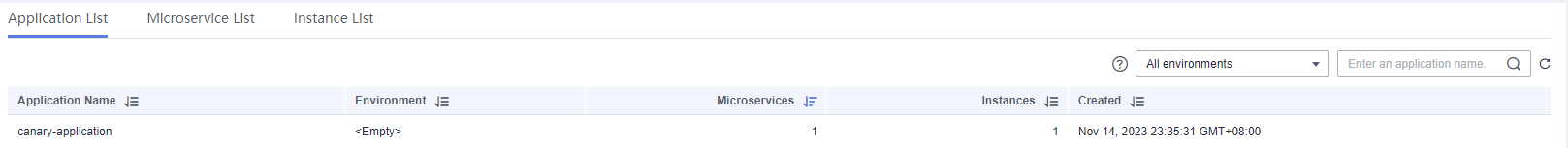
Viewing the Application List
- Log in to CSE.
- Choose Exclusive ServiceComb Engines.
- Click the target engine.
- Choose Microservice Catalog.
- For engines with security authentication disabled, go to 6.
- For engines with security authentication enabled, if the login user is the user imported in Importing an IAM Account, go to 6. For other users, go to 5.
- In the displayed Security Authentication dialog box, enter the account name and password, and click OK.
- If you connect to the ServiceComb engine for the first time, enter the account name root and the password entered when Creating a ServiceComb Engine.
- For details about how to create an account, see Adding an Account.
- Click Application List to view details about all applications of the current account under the engine.
You can search for the target application by application name, or filter applications by environment.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





