Uso de imagens de terceiros
Cenário
O CCE permite que você crie cargas de trabalho usando imagens extraídas de repositórios de imagens de terceiros.
Geralmente, um repositório de imagens de terceiros pode ser acessado somente após a autenticação (usando sua conta e senha). O CCE usa a autenticação baseada em segredo para extrair imagens. Portanto, crie um segredo para um repositório de imagens antes de extrair imagens do repositório.
Pré-requisitos
O nó onde a carga de trabalho está em execução é acessível a partir de redes públicas.
Usar o console
- Crie um segredo para acessar um repositório de imagens de terceiros.
Clique no nome do cluster para acessar o console do cluster. No painel de navegação, escolha ConfigMaps and Secrets. Na página Secrets, clique em Create Secret no canto superior direito. Defina Secret Type como kubernetes.io/dockerconfigjson. Para mais detalhes, consulte Criação de um segredo.
Digite o nome de usuário e a senha usados para acessar o repositório de imagens de terceiros.
Figura 1 Criar um segredo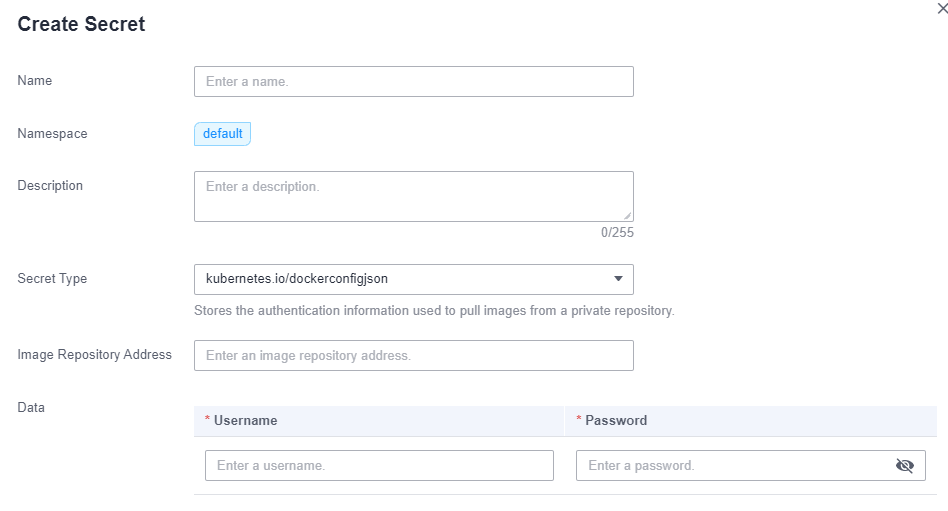
- Ao criar uma carga de trabalho, você pode inserir um caminho de imagem privado no formato de domainname/namespace/imagename:tag em Image Name e selecionar a chave criada em 1.

- Defina outros parâmetros e clique em Create Workload.
Usar o kubectl
- Use o kubectl para se conectar ao cluster. Para mais detalhes, consulte Conexão a um cluster usando o kubectl.
- Use o kubectl para criar um segredo do kubernetes.io/dockerconfigjson.
kubectl create secret docker-registry myregistrykey -n default --docker-server=DOCKER_REGISTRY_SERVER --docker-username=DOCKER_USER --docker-password=DOCKER_PASSWORD --docker-email=DOCKER_EMAIL
No comando anterior, myregistrykey indica o nome da chave, default indica o namespace onde a chave está localizada e outros parâmetros são os seguintes:
- DOCKER_REGISTRY_SERVER: endereço de um repositório de imagens de terceiros, por exemplo www.3rdregistry.com ou 10.10.10.10:443
- DOCKER_USER: conta usada para fazer logon em um repositório de imagens de terceiros
- DOCKER_PASSWORD: senha usada para fazer logon em um repositório de imagens de terceiros
- DOCKER_EMAIL: e-mail de um repositório de imagens de terceiros
- Use uma imagem de terceiros para criar uma carga de trabalho.
Um segredo de kubernetes.io/dockerconfigjson é usado para autenticação quando você obtém uma imagem privada. Segue-se um exemplo de utilização da myregistrykey para autenticação.
apiVersion: v1 kind: Pod metadata: name: foo namespace: default spec: containers: - name: foo image: www.3rdregistry.com/janedoe/awesomeapp:v1 imagePullSecrets: - name: myregistrykey #Use the created secret.






