SEC01-05 Performing Threat Modeling Analysis
Threat modeling helps to systematically identify and evaluate potential threat sources, attack vectors, and attack methods that may pose threats to systems or organizations. In this way, you can understand system security risks, identify security issues in system design, and develop mitigation measures to reduce the risks and to improve system security and resilience.
- Risk level
High
- Key strategies
The following figure shows the model for analyzing the threats during system running.
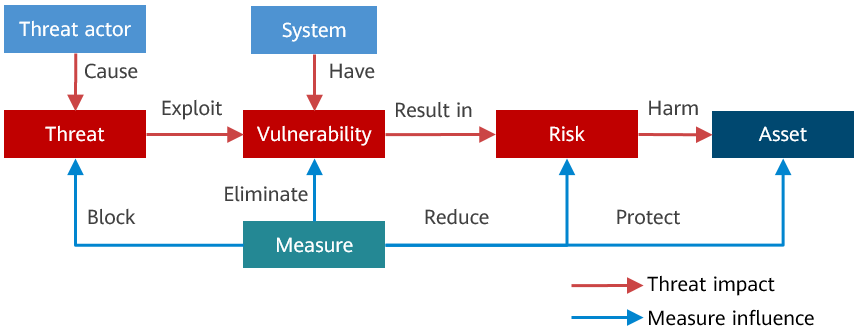
The concepts involved in this model are as follows:
- Threat actor: An entity that intentionally exploits vulnerabilities. A threat actor can be a person, program, hardware, or system.
- Vulnerability: A flaw in a system that allows its security to be compromised, including software, hardware, processes, or human-made defects. The existence of vulnerability indicates the lack of security measures or the defects in security measures.
- Threat: Any potential hazards caused by exploiting vulnerabilities.
- Risk: The possibility of vulnerability exploit by attackers and its business impact. Risks relate vulnerabilities, threats, and the possibility of exploits to the business impact.
- Asset: Any information or resource that is valuable to an organization. It should be protected by security policies.
- Measure: Measures include the mitigation measures for security purposes and the hardening measures for resilience purposes. They help to eliminate vulnerabilities, prevent threats, reduce the impact of risks, and protect assets.
To implement threat modeling, you need to think like an attacker to discover potential exposed surfaces, attack targets, and available attack methods, so as to discover potential security threats in the system and develop corresponding mitigation measures.
The general procedure for threat modeling is as follows:
- Determine the scope: Specify the cloud system scope for threat modeling, including cloud services, data storage, and network architecture.
- Collect information: Collect information about the cloud system, including the system architecture diagram, data flow, and access control policies.
- Identify assets: Determine the critical assets in the cloud system, including data, applications, VMs, and storage.
- Identify threat sources and attack vectors: Determine the threat sources and attack paths that may pose threats to the cloud system, and consider the attack methods that different attackers may take.
- Assess threat probability and impact: Assess the probability and possible impact of each threat, including data leakage and service interruption.
- Develop security countermeasures: Develop security countermeasures and control measures based on identified threats, including access control, encryption, and monitoring.
- Continuous improvement: Periodically review and update threat models to reflect new threats and security risks, continuous improving cloud system security.
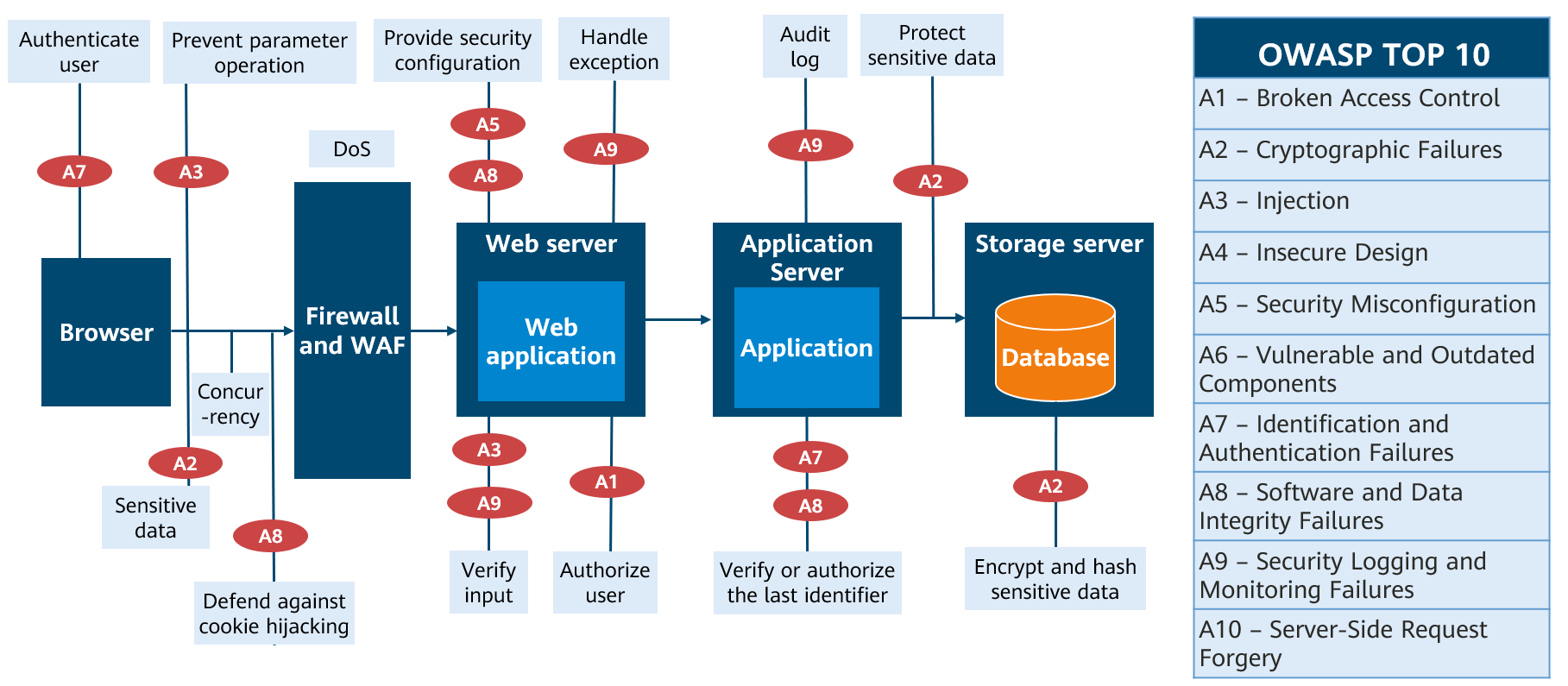
The following table lists the top 10 web application system threats summarized by OWASP and their countermeasures.
- Related cloud services and tools
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





