Failed to Build an Image or Import a File During Model Creation
Symptom
- When a user creates a model, an image fails to be built, and the failure log indicates that the OBS file fails to be downloaded ("Get object size from OBS failed!").
Figure 1 Failed to download the OBS file

- When a user creates a model, error message "Failed to copy model file due to obs exception. Please Check your obs access right." or "User %s does not have obs:object:PutObjectAcl permission." is displayed.
Possible Causes
Using ModelArts requires OBS authorization. ModelArts users require OBS system permissions. The IAM permissions of an IAM user are configured by their tenants. If a tenant does not grant the OBS putObjectAcl permission to their IAM users, this issue occurs.
Solution
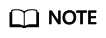
For details about how to create a custom policy for OBS permissions on which ModelArts depends, see Example Custom Policies of OBS.
Assign custom policy permissions to the target user on the IAM console. For details, see Creating a Custom Policy.
- Log in to the IAM console, choose Permissions > Policies/Roles, and click Create Custom Policy in the upper right corner to create a custom policy.
Figure 2 Adding permissions on IAM
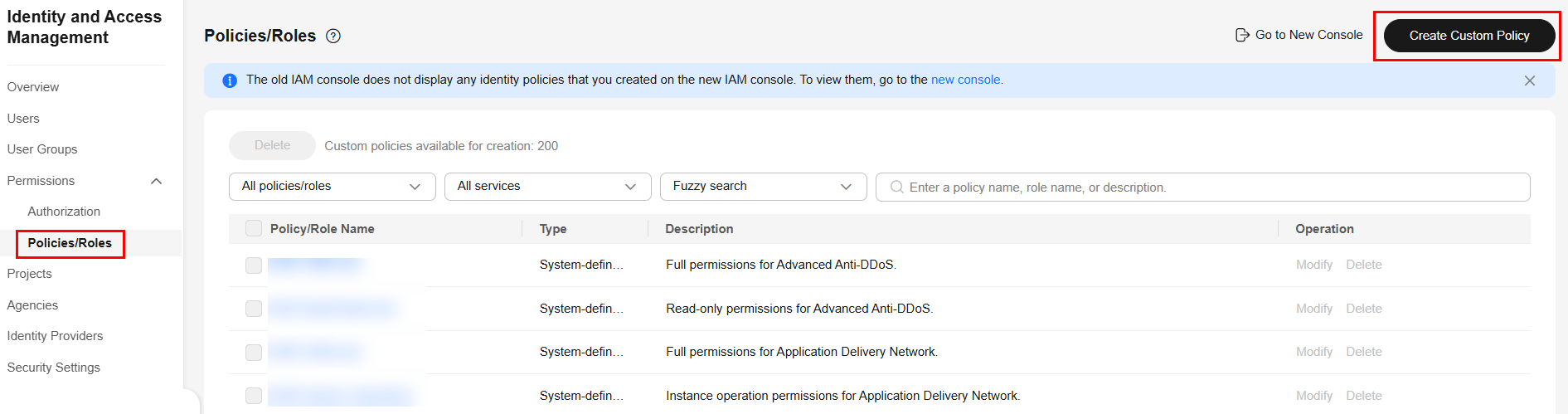 Figure 3 Creating a custom policy
Figure 3 Creating a custom policy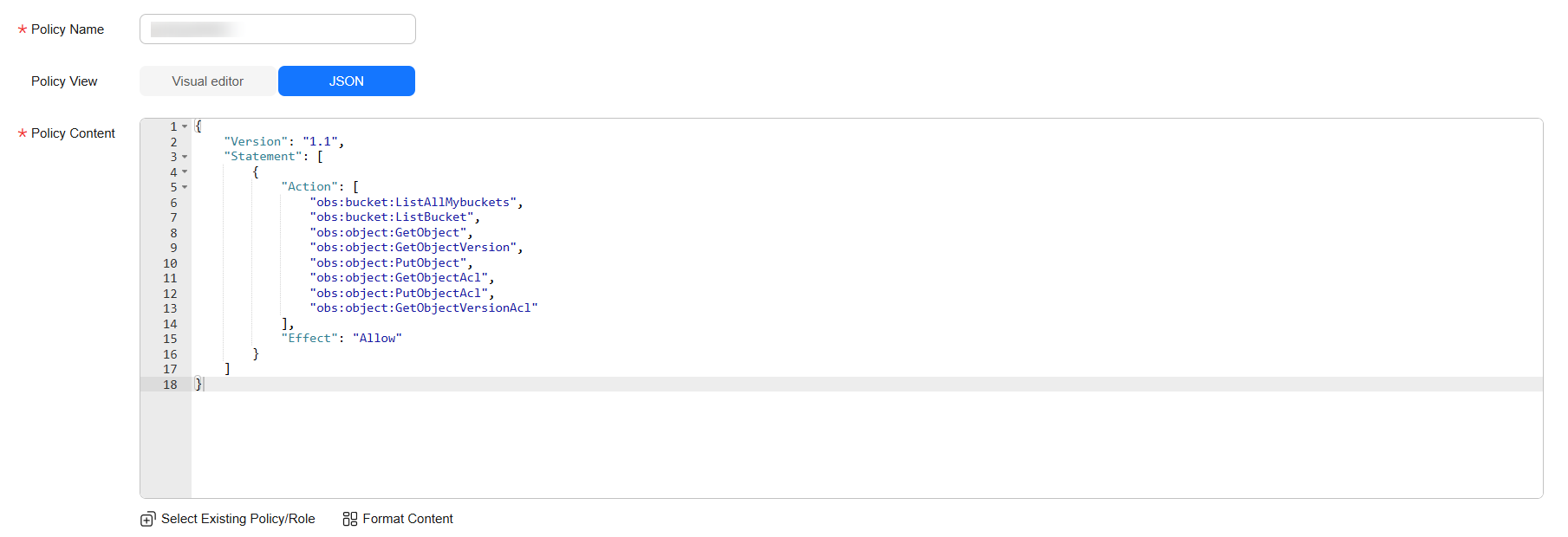
An example custom policy is as follows:
{ "Version": "1.1", "Statement": [ { "Action": [ "obs:bucket:ListAllMybuckets", "obs:bucket:ListBucket", "obs:object:GetObject", "obs:object:GetObjectVersion", "obs:object:PutObject", "obs:object:GetObjectAcl", "obs:object:PutObjectAcl", "obs:object:GetObjectVersionAcl" ], "Effect": "Allow" } ] } - Assign custom policy permissions to the user group to which the IAM user belongs.
Choose User Groups and click the user group to which the IAM user belongs to access the user group details page.
Figure 4 User Groups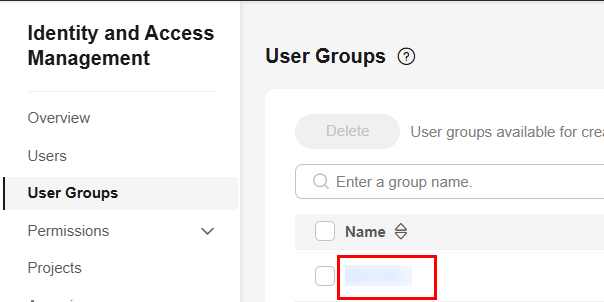
On the Permissions tab page, click Authorize and select the custom policy and authorization scope.
OBS is a global service and cannot be authorized by region. If you need to manage permissions by project, click Enterprise projects in Select Scope.
After the authorization is successful, you can view the permission and authorization scope in By Enterprise Project.Figure 5 Assigning permissions to an IAM user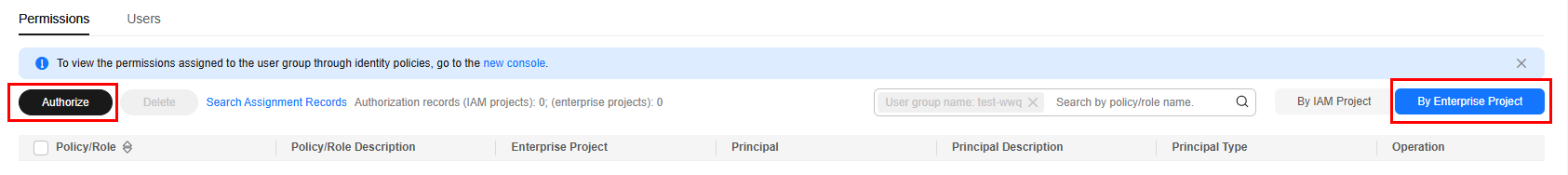
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





