Getting Started with HSS
Host Security Service (HSS) is designed to improve the overall security for hosts. It reduces intrusion risks for hosts with asset management, vulnerability management, intrusion detection, and baseline inspection functions.
This document describes how to get started with HSS.
Step 1: Set the Environment
1. Log in to the management console. Choose Service List > Security > Host Security Service.
2. On the Dashboard page, click Purchase HSS. Refer to Purchasing an HSS Quota.
3. In the navigation pane, choose Installation and Configuration to install the Windows or Linux agent.

Note
HSS provides three editions: basic edition, enterprise edition, flagship edition and web tamper protection edition.
1
Choose Security > Host Security Service.
2
Purchase HSS.
3
Installation and Configuration page

View Image
Step 2: Enable Alarm Notification
1. In the navigation pane, choose Servers. In the upper right corner of the page, click Configure Alarm Notification.
2. Select the alarm notification items and SMN topic.

Note
1. Alarm notification settings are effective only for the current region. To receive notification messages from another region, switch to that region and configure notification.
2. The confirmation message about topic subscription may be regarded as spam. If you do not receive the message, check whether it is intercepted as spam.
1
Servers
2
Configure alarm notification
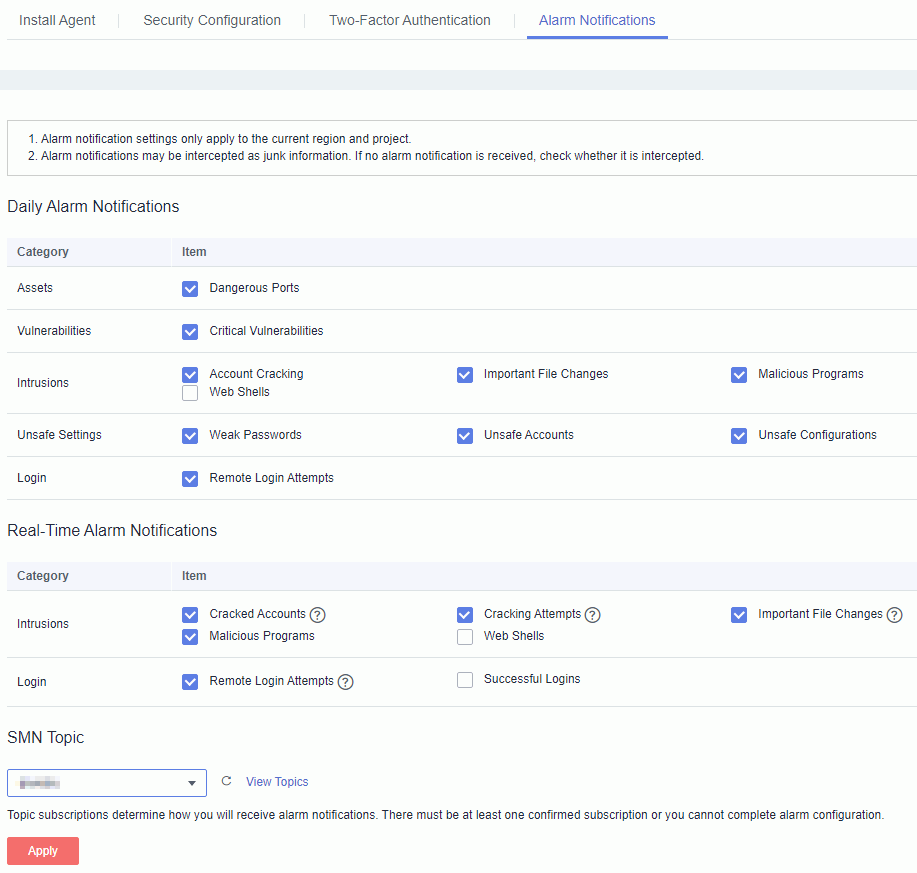

View Image
Step 3: Enable HSS
1. In the navigation pane, choose Servers. On the displayed page, select desired ECSs, and click Enable in the upper left corner.
2. In the Enable dialog box, select Basic edition, Enterprise or Flagship. Read the Host Security Service Disclaimer . If you agree with the disclaimer, select I have read and agree to the Host Security Service Disclaimer and click OK.

Note
To enable HSS for one ECS, click Enable in the Operation column.
1
Servers
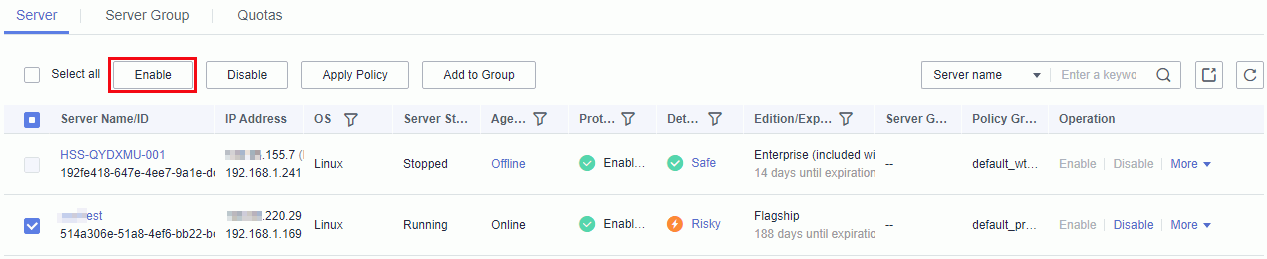
2
Enable HSS.
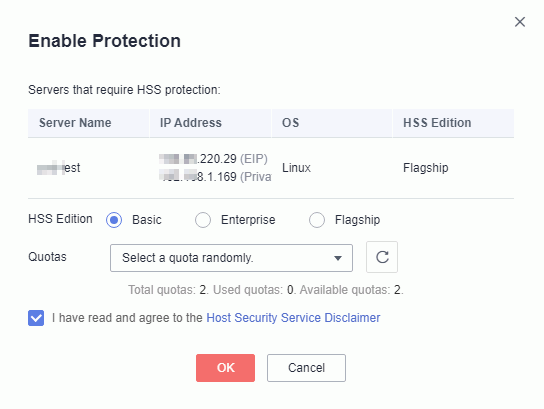

View Image
Step 4: View the Detection Results
1. Choose Security > Host Security Service > Dashboard. On the displayed Dashboard page, view risk statistics on protected ECS over the past 24 hours.
2. View the risk statistics of last week.
3. View the top 5 vulnerable ECSs last week.

Note
1. To view detailed detection results of one ECS, locate the desired ECS and click the result in the Detection Result column.
2. You can also choose Asset Management, Vulnerability Management, Intrusion Detection, or Baseline Detection in the navigation pane to view the detection result of each category and recommended mitigations.
1
Risk statistics on protected ECSs (last 24 hours)
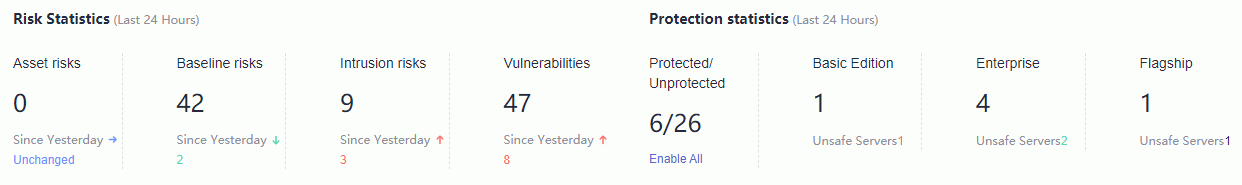
2
Risk statistics (last 7 days)
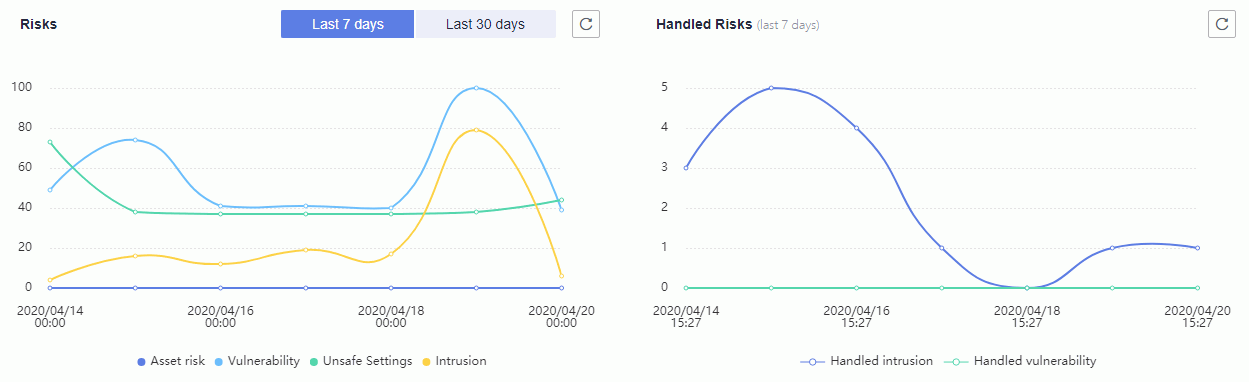
3
Top 5 vulnerable ECSs (last 7 days)


View Image
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot








