Event Overview
Context
After identifying alarm events, Huawei Qiankun performs further intelligent handling, identifies threat events, and classifies them into three types: external attack sources, compromised hosts, and malicious files.
By default, data of the last 30 days is displayed on the threat event page. Tenants can select a period in the upper right corner to view data. When a tenant clicks More, data of the last three months is displayed.
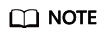
Service data of tenants will be retained for a maximum of three months.
Threat events in some special scenarios are labeled with different tags.
- The threat event of a successful attack is labeled with Successful Attack in the Event Name column.
- Threat events detected by devices that are onboarded in bypass mode are labeled with Bypass in the Attack Status column. A device working in bypass mode cannot block traffic.
You can view threat events by event type or site. The two modes display the same threat events in different ways. Unless otherwise specified, the following sections describe external attack sources, compromised hosts, and malicious files by event type.
High-level tenant accounts have the permission to check and handle their own and lower-level tenant accounts' threat events.
Procedure
- Log in to the Huawei Qiankun console, and choose .
- Click Threat Events in the menu bar.
- Check threat events by event type or site.
- By event type: Click By Event Type.
When you view threat events by event type, the threat event page displays four modules: Event Overview, External Attack Sources, Compromised Hosts, and Malicious Files.Figure 1 Checking threat events by event type
Table 1 Checking threat events by event type Module
Description
Event Overview
Displays information about threat events.
- On the left of the card: Click the corresponding number to view all alarm events and alarm events that have been automatically blocked.
- On the right of the card: The blue lines indicate the threat events that have been handled automatically or manually, and the gray lines indicate the threat events that have not been handled. You can move the cursor to the lines to view details data.
You can View More to go to the alarm event details page.
External Attack Sources
Displays information about external attack sources. You can click View More to view details of external attack sources.
Compromised Hosts
Displays information about compromised hosts. You can click View More to view the details of compromised hosts.
Malicious Files
Displays information about malicious files. You can click View More to view the details of malicious files.
- By site: Click By Site.
When you click By Site to check threat events, the threat event page displays threat events at each site. You can click Site Details corresponding to a site to view the site model.
A site is a collection of devices located in the same administrative domain, either physically or logically. Network quality and security evaluation is performed on a per-site basis, achieving unified device monitoring and management.
Huawei Qiankun aggregates threat logs reported by the Qiankun Shield devices that do not belong to any site into alarm events. The alarm events will be included in the unknown site.
Figure 2 Checking threat events by site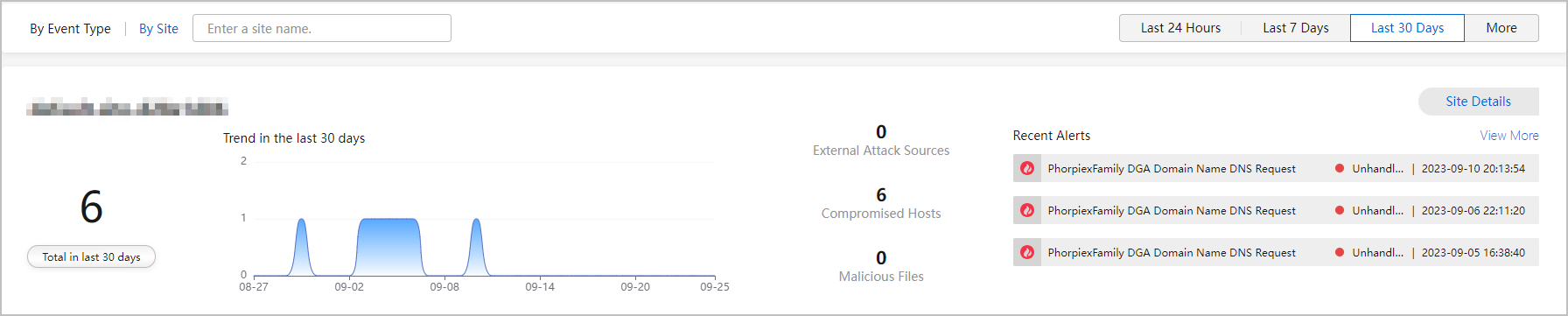
- By event type: Click By Event Type.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






