Checking Security Reports
Prerequisites
You have bound an email address through the subscription management. For details, see section "Subscription Management" in Tenant Operation Guide.
Context
Huawei Qiankun provides the function of checking security reports to help tenants learn about the trend of network security status in a certain period.
Tenants can view security reports on the security report page. Huawei Qiankun generates security reports of the last week or month on Monday or the first day of each month. After subscribing to the border protection security report on the page, tenants can link email addresses to their accounts to receive weekly or monthly security reports.
Currently, common reports and customized reports are supported. Huawei Qiankun retains the reports of the last three calendar months (including the current month) only.
- Common reports: They are classified into weekly reports and monthly reports. Top-level tenants can check individual reports of each tenant in the current workgroup and summary reports of all tenants. None-top-level tenants can only check individual reports.
- Customized reports: security operations experts or MSPs can configure the periodic report generation. The customized reports cannot be subscribed to. They can be pushed only by security operations experts or MSPs.
Procedure
- Log in to the Huawei Qiankun console, and choose .
- Click Security Reports in the menu bar.
- Select a report and click Preview.
Figure 1 Security report list
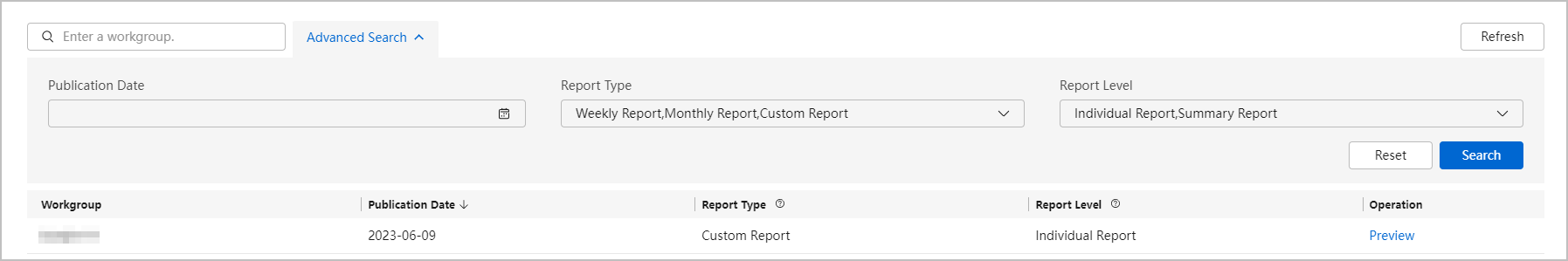
- Check security reports.
Table 1 Introduction to security reports Module
Description
Cyber Security Report Overview
Displays statistics about original alarms, threat events, and specific risks.
Threat Events
Threat events are real security attack events automatically identified by the system based on original security alarms and automatic analysis technologies such as association analysis, expert models, and artificial intelligence.
This module displays information, including the trend of threat events, threat types, destination addresses, details, as well as statistics on severity and response status.
Special Risk | External Attack Source
External attack sources are the addresses of external attackers identified by the system after automatic analysis and determination of threat events. Handling external attack sources promptly can reduce external intrusion threats.
This module displays the quantity trend, attack source locations, attack types, details, as well as statistics on severity and threat status.
Special Risk | Compromised Host
Compromised hosts are internal risky asset addresses identified by the system after automatic analysis and determination of threat events. The compromised hosts include the following types: mining, remote control, ransomware, and internal attack threats.
This module displays the trend of compromised hosts, malicious actions, compromised types, details, as well as statistics on severity and threat status.
Special Risk | Malicious File
Malicious files are malicious program files identified by the system after automatic analysis and determination of threat events. The files include Trojan horses, worms, mining, ransomware, and advertisements. The system automatically detects and blocks high-risk malicious files.
This module displays the quantity trend, file types, risky hosts, details as well as statistics on severity and threat status.
Follow-up Procedure
- You can click Export to PDF on the preview pages of security reports to download the security reports in the PDF format to the local PC.
- After learning about the trend of security status, you can handle the issues by referring to Handling Threat Events.
If you do not know how to handle the problem or the problem persists after you handle it, contact the corresponding Managed Security Service Provider (MSSP) or channel partner.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






