Por que "Error from server (Forbidden)" é exibido quando uso o kubectl?
Sintoma
Quando você usa o kubectl para criar ou consultar recursos do Kubernetes, a seguinte saída é retornada:
# kubectl get deploy Error from server (Forbidden): deployments.apps is forbidden: User "0c97ac3cb280f4d91fa7c0096739e1f8" cannot list resource "deployments" in API group "apps" in the namespace "default"
Possível causa
Este usuário não tem permissões para operar recursos do Kubernetes.
Solução
Atribua permissões ao usuário.
- Efetue logon no console do CCE. No painel de navegação, escolha Permissions.
- Selecione um cluster para o qual você deseja adicionar permissões na lista suspensa à direita.
- Clique em Add Permissions no canto superior direito.
- Confirme o nome do cluster e selecione o namespace para o qual atribuir permissões. Por exemplo, selecione All namespaces, o usuário de destino ou grupo de usuários e selecione as permissões.
Se você não tiver permissões do IAM, não poderá selecionar usuários ou grupos de usuários ao configurar permissões para outros usuários ou grupos de usuários. Nesse caso, você pode inserir um ID de usuário ou um ID de grupo de usuários.
Figura 1 Configurar permissões de namespace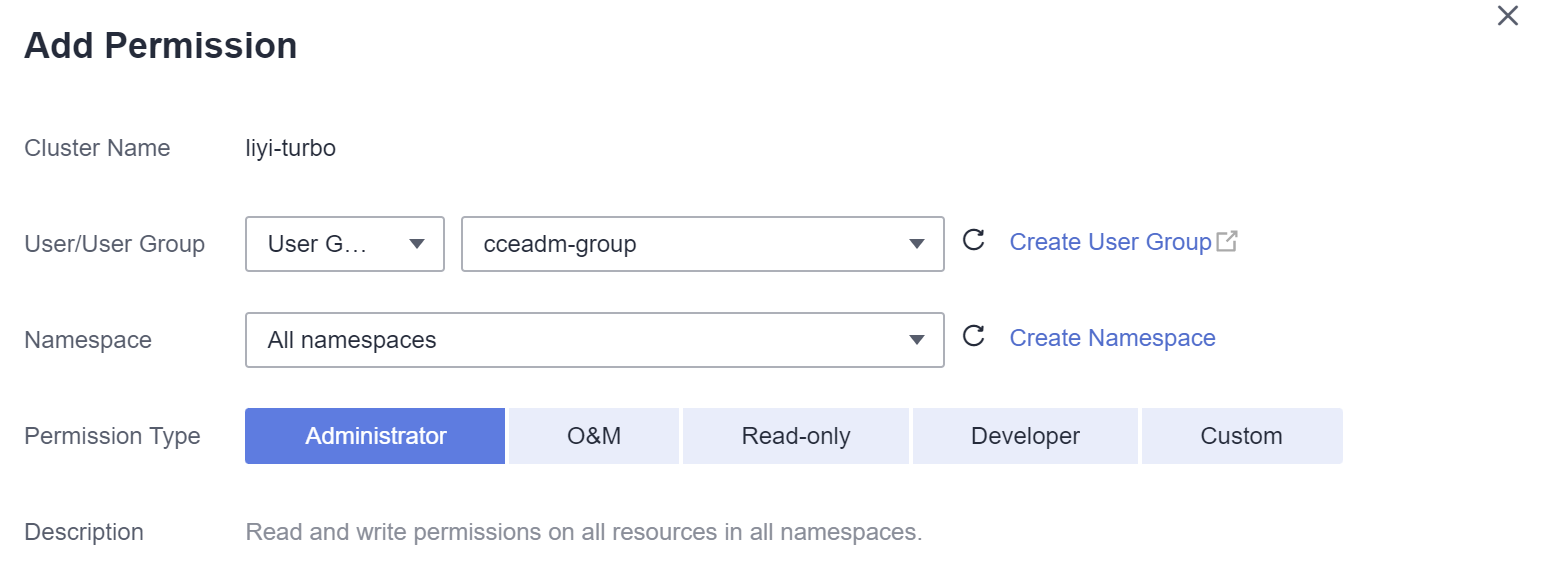
As permissões podem ser personalizadas conforme necessário. Depois de selecionar Custom para Permission Type, clique em Add Custom Role à direita do parâmetro Custom. Na caixa de diálogo exibida, insira um nome e selecione uma regra. Depois que a regra personalizada for criada, você poderá selecionar um valor na caixa de listagem suspensa Custom.
Figura 2 Permissão personalizada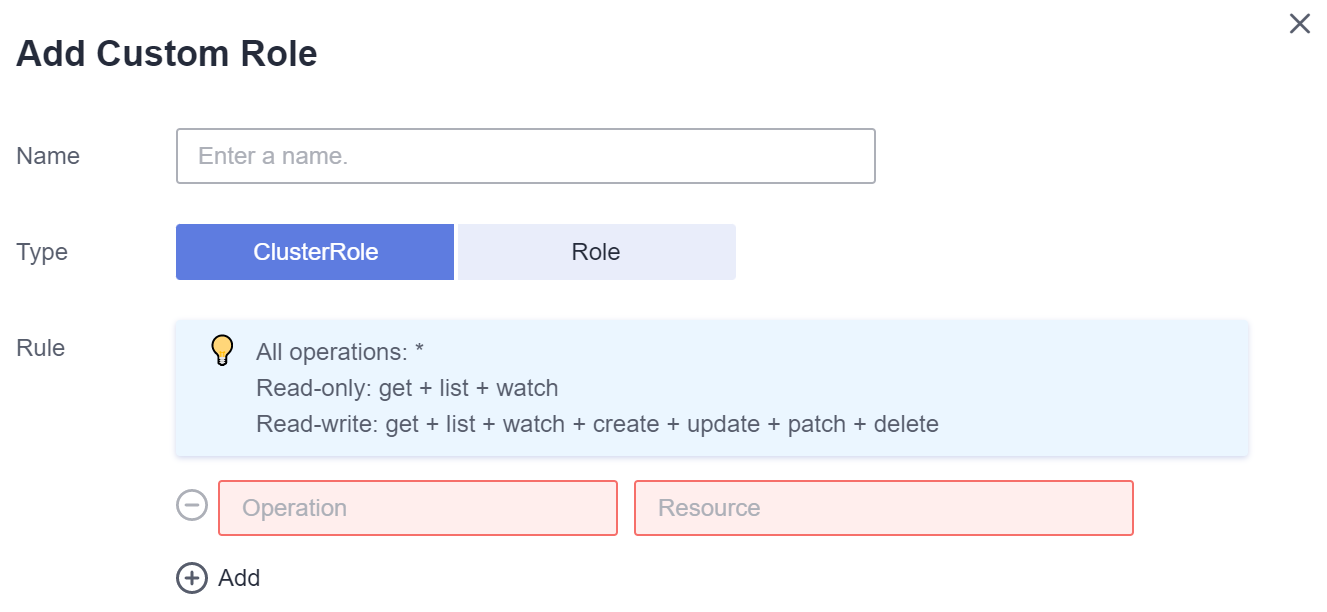
- Clique em OK.






