Assigning SFS Turbo Folder-Level Access Permissions to an IAM User
Scenario
Grant access permission of specific SFS Turbo folders to IAM users.
Granting the IAM user the SFS Turbo folder-level access permission is a whitelist function. Submit a service ticket to apply for the permission as needed.
Constraints
- Ensure that you have enabled strict authorization. Log in to the ModelArts console. In the navigation pane on the left, choose Settings. On the Permission Management page, click Enable strict authorization.
- If the ModelArts permission for the IAM user were not configured prior to enabling strict authorization mode, the IAM user might lose access to ModelArts once that mode is activated. Configure ModelArts permissions based on the service requirements. For details, see Dependencies and Agencies.
Procedure
- Log in to the management console using the main account, hover the cursor over your username in the upper right corner, and choose Identity and Access Management from the drop-down list to switch to the IAM management console.
- On the IAM console, choose Permissions > Policies/Roles from the navigation pane on the left, click Create Custom Policy in the upper right corner, and configure the policy as follows:
- Policy Name: Enter a policy name, for example, ma_sfs_turbo.
- Policy View: Select JSON.
- Policy Content: Enter the following information:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "<modelarts_action>" ], "Condition": { "StringEqualsIfExists": { "modelarts:sfsId": [ "<your_ssf_id>" ], "modelarts:sfsPath": [ "<sfs_path>" ], "modelarts:sfsOption": [ "<sfs_option>" ] } } } ] }
- Before the preceding policies are created, all IAM users can mount to SFS Turbo by default. After you create the preceding SFS permission control policies, the IAM users who are not granted with the permission cannot mount to SFS Turbo when creating a training job on the ModelArts console, except the IAM users with the Tenant Administrator permission.
- Currently, you can configure only permit policies, that is, the Effect in the policy can only be set to Allow. Do not configure deny policies.
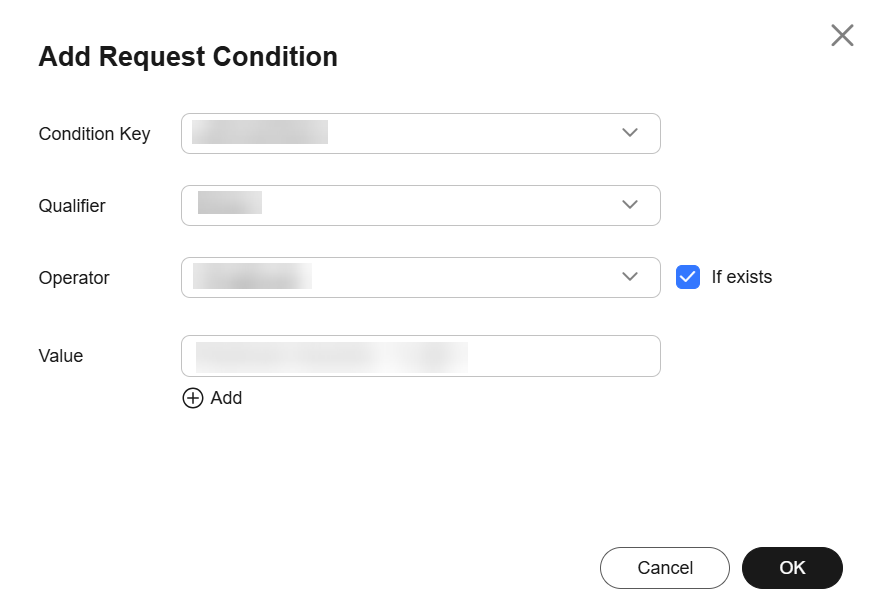
- The Condition parameter must use the StringEqualsIfExists field, and If exists must be enabled for the corresponding visualized view.
Figure 1 Enabling If exists
Replace <modelarts_action>, <your_ssf_id>, <sfs_path>, and <sfs_option> with actual parameters as you need. The following table describes the parameters.
Table 1 Parameter description Parameter
Description
Action
Scenario in which the SFS Turbo folder access permission is granted.
- modelarts:notebook:create: The permission is granted during development environment instance creation.
- modelarts:trainJob:create: The permission is granted during training job creation.
Multiple actions are supported, the following shows an example:
"Action": [ "modelarts:trainJob:create", "modelarts:notebook:create" ],
modelarts:sfsId
SFS Turbo ID, which can be obtained on the SFS Turbo details page. You can enter multiple IDs, the following shows an example:
"modelarts:sfsId": [ "0e51c7d5-d90e-475a-b5d0-ecf896da3b0d", "2a70da1e-ea87-4ee4-ae1e-55df846e7f41" ],
modelarts:sfsPath
Path of the SFS Turbo folder whose permissions need to be configured. You can enter multiple paths, the following shows an example:
"modelarts:sfsPath": [ "/path1", "/path2/path2-1" ],
If there are multiple SFS IDs, the SFS paths will apply to all SFS IDs. As shown in the following example, permission to access /path1 and /path2/path2-1 of both 0e51c7d5-d90e-475a-b5d0-ecf896da3b0d and 2a70da1e-ea87-4ee4-ae1e-55df846e7f41 are configured.
"modelarts:sfsId": [ "0e51c7d5-d90e-475a-b5d0-ecf896da3b0d", "2a70da1e-ea87-4ee4-ae1e-55df846e7f41" ], "modelarts:sfsPath": [ "/path1", "/path2/path2-1" ],
modelarts:sfsOption
Type of the access permission. The following parameters are supported:
- readonly: Read-only permission
- readwrite: Read and write permission. When you create a development environment instance, modelarts:notebook:create must be set to readwrite.
To add multiple SFS options to a custom policy, add a JSON structure to Statement, the following shows an example:
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "modelarts:trainJob:create" ], "Condition": { "StringEqualsIfExists": { "modelarts:sfsId": [ "0e51c7d5-d90e-475a-b5d0-ecf896da3b0d" ], "modelarts:sfsPath": [ "/path1" ], "modelarts:sfsOption": [ "readonly" ] } } }, { "Effect": "Allow", "Action": [ "modelarts:trainJob:create" ], "Condition": { "StringEqualsIfExists": { "modelarts:sfsId": [ "0e51c7d5-d90e-475a-b5d0-ecf896da3b0d" ], "modelarts:sfsPath": [ "/path2" ], "modelarts:sfsOption": [ "readwrite" ] } } } ] } - Create a user group and add the user to the user group. For details, see Step 1 Creating a User Group and Adding Users to the User Group.
- Grant a policy to the user group. On the user group list page of IAM, click Authorize of the target user group. The Authorize User Group page is displayed. Select the ma_sfs_turbo policy created in Step 2. Click Next and then OK.
- Add the IAM ReadOnlyAccess permission to an existing ModelArts agency.
- Log in to the ModelArts management console. In the navigation pane on the left, choose Permission Management. On the displayed page, locate the target agency, choose View Permissions in the Operation column, and click Modify permission in IAM.
- On the IAM console, choose Agencies from the navigation pane on the left, and choose Permissions > Authorize. Search for IAM ReadOnlyAccess, enable it, and click Next and OK.
- Verify that the permission is granted.
Log in to ModelArts as the IAM user, only the configured SFS Turbo folders are displayed during training job creation and notebook creation.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





