Configuring a Baseline Check Policy
Scenarios
Two scheduled check policies, Advanced policy and Basic policy, have been preconfigured in HSS. If HSS is enabled for a server, the server will be bound to either of these policies by default. HSS will automatically perform a baseline check some time between 04:00 to 05:00 every day.
- Advanced policy
When you enable the HSS enterprise, premium, container, or WTP edition for a server, the advanced policy will be bound to the server by default. The check items of the policy vary depending on the OS type (Windows or Linux):
- Linux: Baseline settings, password complexity policies, and common weak passwords
- Windows: Baseline settings and common weak passwords
For details about how to modify the check items, check time, and scanned servers of the advanced policy, see Modifying an Advanced Policy.
- Basic policy
When you enable the HSS basic or professional edition for a server, the basic policy will be bound to the server by default. The check items of the policy vary depending on the OS type (Windows or Linux):
- Linux: Common weak passwords and password complexity policies
- Windows: Common weak passwords
For details about how to modify the check items, check time, and scanned servers of the basic policy, see Modifying a Basic Policy.
You can create custom check policies in the HSS enterprise, premium, container, and WTP editions, for either one-time or periodic checks. If you do not want to bind the advanced policy to all servers, you can create custom policies for refined management. For details, see Creating a Custom Check Policy.
After configuring a default or custom policy, you can define the rules for checking password complexity policies and weak passwords. For details, see Defining a Rule to Check Password Complexity Policies and Defining Weak Passwords.
Constraints
- Each server can only be bound to a single scheduled scan policy (including the default one). When a server is bound to a new scheduled policy, it is automatically unbound from any existing policies.
- Each server can be bound to multiple one-time scan policies.
Modifying an Advanced Policy
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Baseline Checks.
Figure 1 Baseline checks
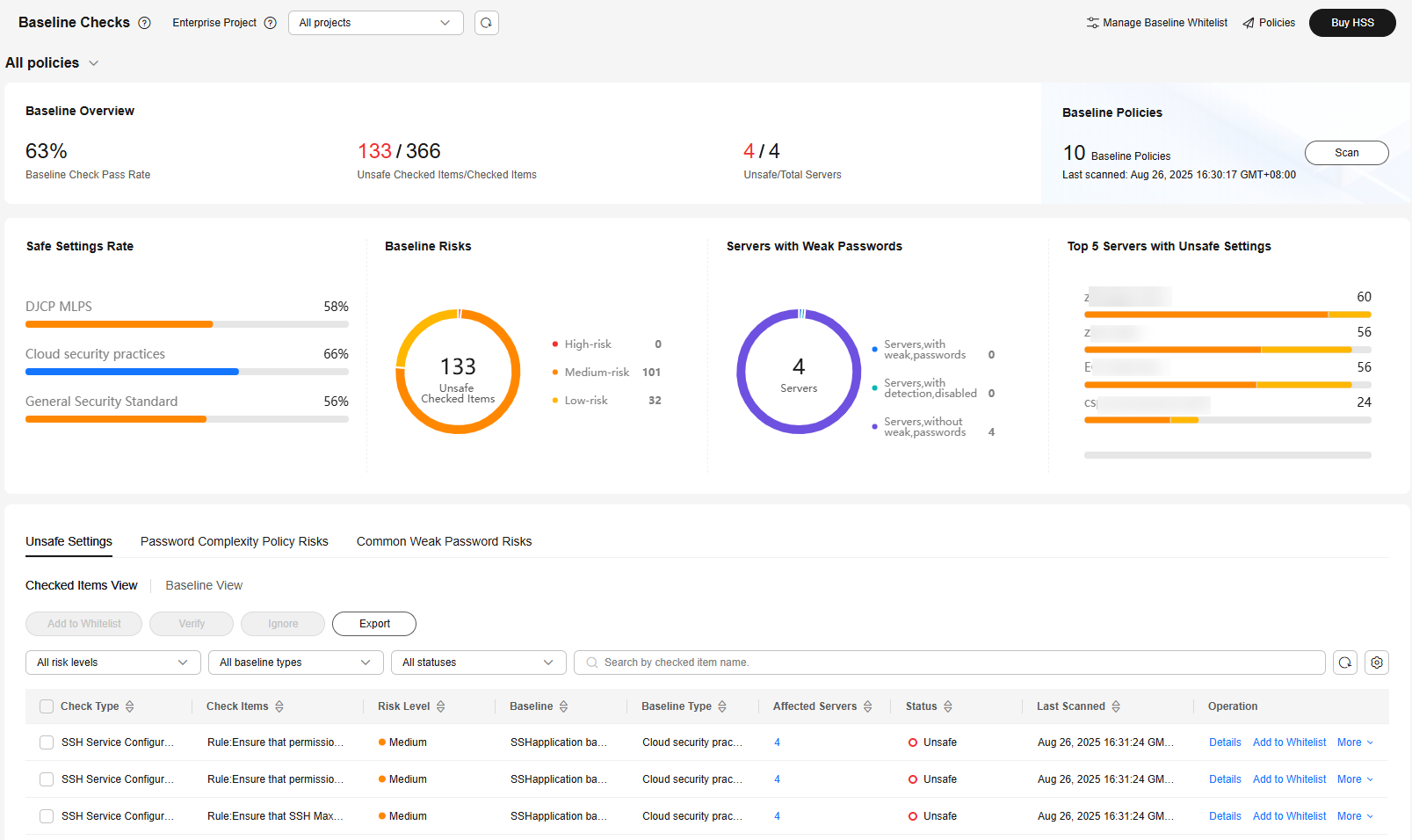
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- In the upper right corner of the page, click Policies.
- In the Operation column of an Advanced policy, click Edit. Modify the policy on the edit page.
- Configure the baseline check policy as needed. For more information, see Table 1.
Figure 2 Editing an advanced policy
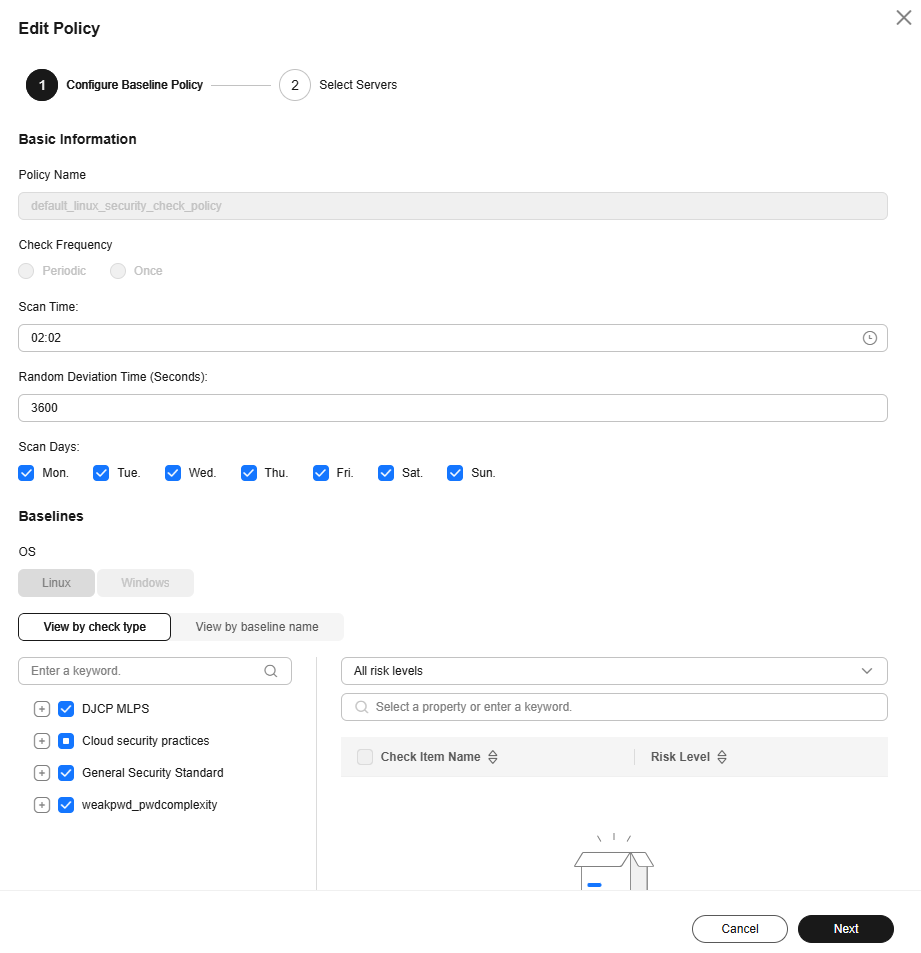
Table 1 Advanced policy parameters Parameter
Description
Recommended Value
Policy Name
Default advanced policy name. It cannot be changed.
- Linux: default_linux_security_check_policy
- Windows: default_windows_security_check_policy
-
Check Frequency
The default value is Periodic and cannot be changed.
-
Scan Time
Click the input box and set the scan time.
04:00
Random Deviation Time (Seconds)
Enter the allowed delay (in seconds) of a scan task. The value must be a positive integer.
For example, if the scan time is 04:00 and the random deviation time is 3,600 seconds, the scan task will be performed sometime between 04:00 and 05:00.
3600
Scan Days
Select the days of a week for scans.
The options include Sunday, Monday, Tuesday, Wednesday, Thursday, Friday, and Saturday.
Sunday, Monday, Tuesday, Wednesday, Thursday, Friday, and Saturday.
Baselines
- OS
The default value is used and cannot be changed.
- Baseline
Select baselines. You can click View by check type or View by baseline name to browse faster.
- You can select top-level types DJCP MLPS Compliance, Cloud security practices, General Security Standard, and Weak Password & Password Complexity.
- You can click the
 next to a top-level type to expand level-2 types.
next to a top-level type to expand level-2 types. - You can click the
 next to a level-2 type to expand level-3 types.
next to a level-2 type to expand level-3 types. - After you click a level-2 or level-3 type, the check items of that type will be displayed in the list on the right.
- If you click Common weak passwords or Password complexity check (supported for Linux only), you can click Define in the area on the right to define the rules for checking common weak passwords or password complexity policies. You can also configure them on the Baseline Checks page. For details, see Defining a Rule to Check Password Complexity Policies and Defining Weak Passwords.
For more information, see Baseline Check Content.
- OS: -
- Baselines: Select all.
- Confirm parameter settings and click Next.
- Select the servers where the policy is to be applied. Click OK.
Modifying a Basic Policy
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Baseline Checks.
Figure 3 Baseline checks

- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- In the upper right corner of the page, click Policies.
- In the Operation column of a Basic policy, click Edit. Modify the policy on the edit page.
- Configure the baseline check policy as needed. For more information, see Table 2.
Figure 4 Editing a basic policy
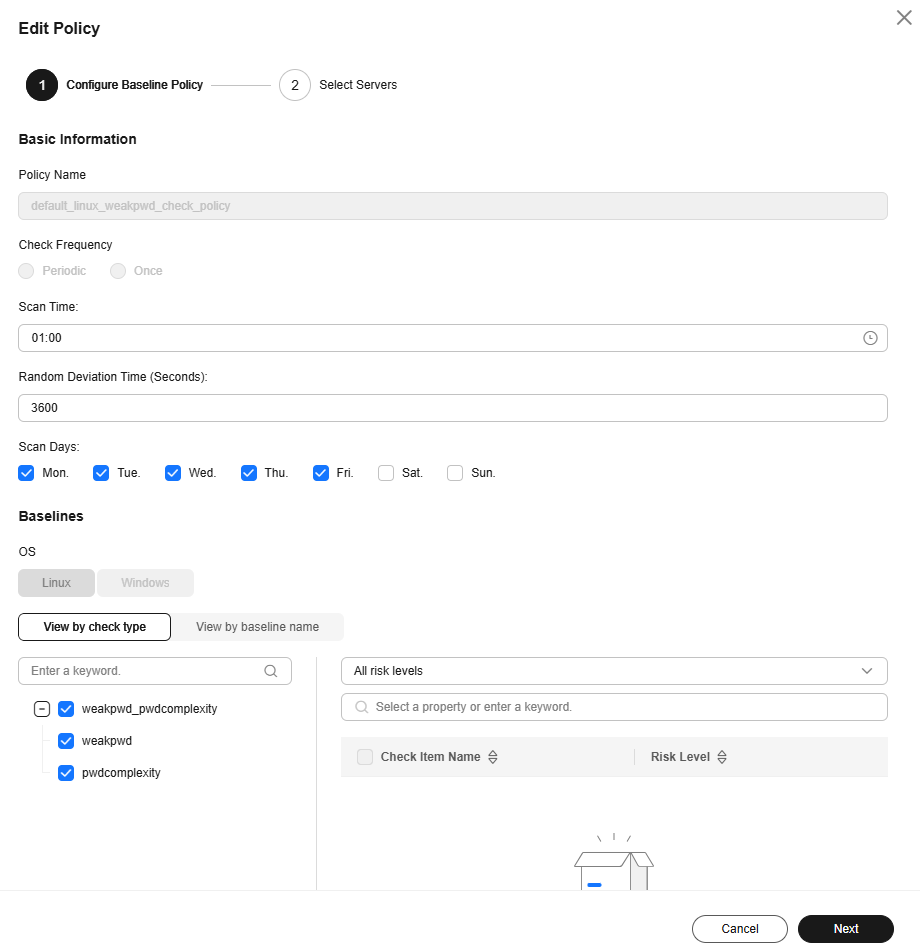
Table 2 Basic policy parameters Parameter
Description
Recommended Value
Policy Name
Default basic policy name. It cannot be changed.
- Linux: default_linux_weakpwd_check_policy
- Windows: default_windows_weakpwd_check_policy
-
Check Frequency
The default value is Periodic and cannot be changed.
-
Scan Time
Click the input box and set the scan time.
04:00
Random Deviation Time (Seconds)
Enter the allowed delay (in seconds) of a scan task. The value must be a positive integer.
For example, if the scan time is 04:00 and the random deviation time is 3,600 seconds, the scan task will be performed sometime between 04:00 and 05:00.
3600
Scan Days
Select the days of a week for scans.
The options include Sunday, Monday, Tuesday, Wednesday, Thursday, Friday, and Saturday.
Sunday, Monday, Tuesday, Wednesday, Thursday, Friday, and Saturday.
Baselines
- OS
The default value is used and cannot be changed.
- Baseline
Select baseline check items. For Linux, you can select Common weak passwords or Password complexity check. For Windows, you can select only Common weak passwords.
You can click the detection item name and click Define in the list on the right to customize weak password or password complexity detection rules. You can also configure them on the Baseline Checks page. For details, see Defining a Rule to Check Password Complexity Policies and Defining Weak Passwords.
For more information, see Baseline Check Content.
- OS: -
- Baselines: Select all.
- Confirm parameter settings and click Next.
- Select the servers where the policy is to be applied. Click OK.
Creating a Custom Check Policy
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Baseline Checks.
Figure 5 Baseline checks

- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- In the upper right corner of the page, click Policies.
- Click Create Policy. On the Create Policy page, configure the baseline check policy as prompted. For more information, see Table 3.
Figure 6 Creating a policy
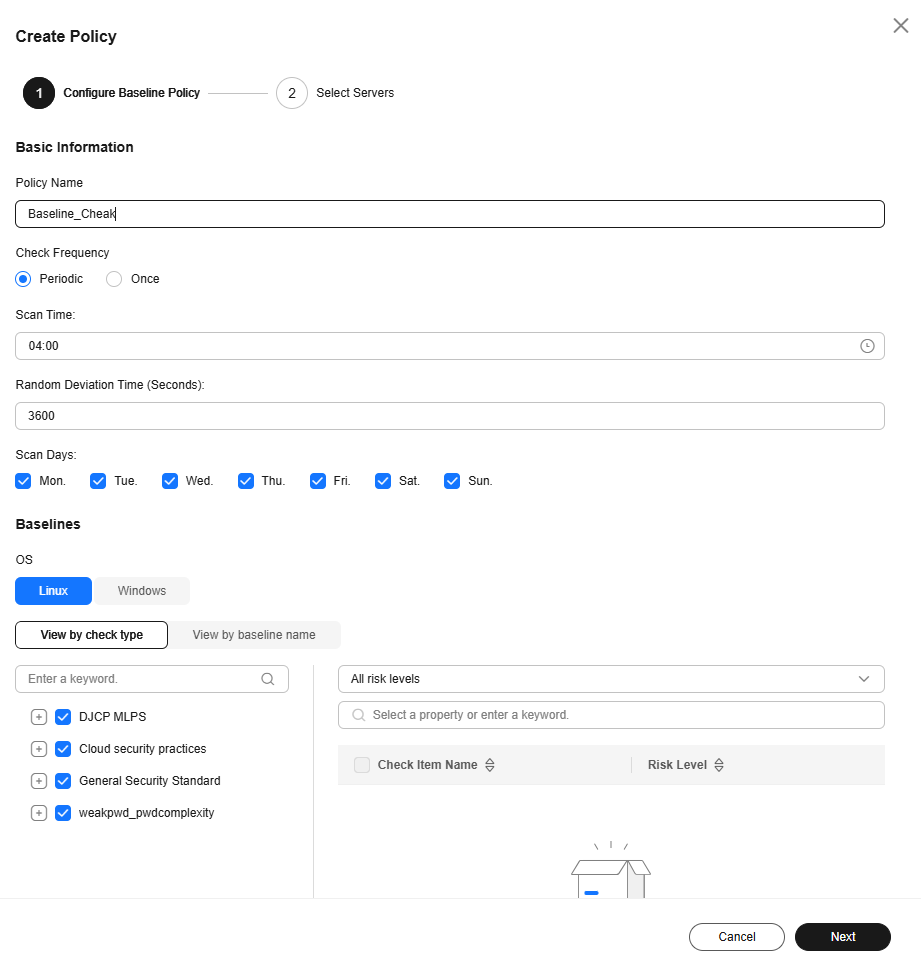
Table 3 Policy parameters Parameter
Description
Recommended Value
Policy Name
Enter a policy name. The requirements are as follows:
- It can contain 1 to 64 characters.
- It can contain letters, numbers, underscores (_), and hyphens (-).
-
Check Frequency
Set the check frequency of the policy.
- Periodic: The check is performed automatically and periodically.
- Once: The check is performed manually only once.
Periodic
Scan Time
Click the input box and set the scan time.
04:00
Random Deviation Time (Seconds)
Enter the allowed delay (in seconds) of a scan task. The value must be a positive integer.
For example, if the scan time is 04:00 and the random deviation time is 3,600 seconds, the scan task will be performed sometime between 04:00 and 05:00.
3600
Scan Days
Select the days of a week for scans.
The options include Sunday, Monday, Tuesday, Wednesday, Thursday, Friday, and Saturday.
Sunday, Monday, Tuesday, Wednesday, Thursday, Friday, and Saturday.
Baselines
- OS
Select the server OS type (Linux or Windows).
- Baseline
Select baselines. You can click View by check type or View by baseline name to browse faster.
- You can select top-level types DJCP MLPS Compliance, Cloud security practices, General Security Standard, and Weak Password & Password Complexity.
- You can click the
 next to a top-level type to expand level-2 types.
next to a top-level type to expand level-2 types. - You can click the
 next to a level-2 type to expand level-3 types.
next to a level-2 type to expand level-3 types. - After you click a level-2 or level-3 type, the check items of that type will be displayed in the list on the right.
- If you click Weak Passwords & Password Complexity (supported for Linux only), you can click Define to define the check standard for common weak passwords or password complexity policies. You can also configure them on the Baseline Checks page. For details, see Defining a Rule to Check Password Complexity Policies and Defining Weak Passwords.
For more information, see Baseline Check Content.
- OS: -
- Baselines: Select all.
- Confirm parameter settings and click Next.
- Select the servers where the policy is to be applied. Click OK.
If the new policy is displayed in the protection policy list, the creation succeeded.
Defining a Rule to Check Password Complexity Policies
While you configure a baseline check policy, you can select whether to check the password complexity policies on servers. This section describes how to modify the rule used for checking password complexity policies.
The rule will be applied to all the baseline check policies under the current enterprise project.
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Baseline Checks.
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- On the Password Complexity Policy Risks tab, click Customize Password Complexity Policy.
Figure 7 Defining a rule to check password complexity policies
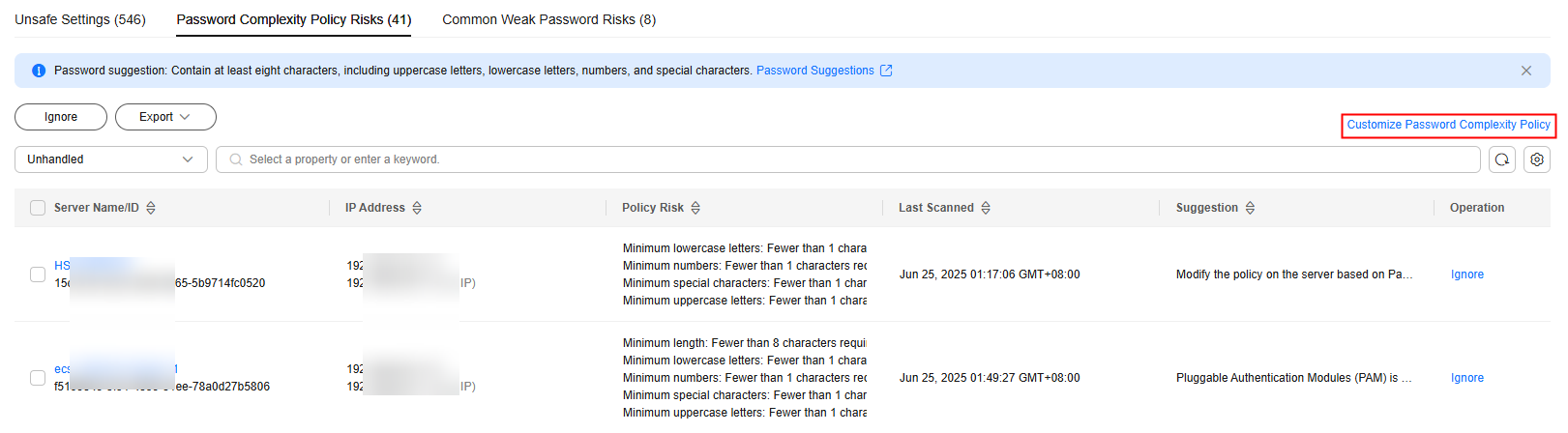
- In the dialog box that is displayed, configure the password complexity policy items, and click OK.
The system checks the password complexity against your settings.
Defining Weak Passwords
While you configure a baseline check policy, you can select whether to check for common weak passwords. This section describes how to define weak passwords.
The weak password settings will be applied to all the baseline check policies under the current enterprise project.
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Baseline Checks.
- (Optional) If you have enabled the enterprise project function, select an enterprise project from the Enterprise Project drop-down list in the upper part of the page to view its data.
- On the Common Weak Password Risks tab page, click Define Weak Passwords.
Figure 8 Defining weak passwords
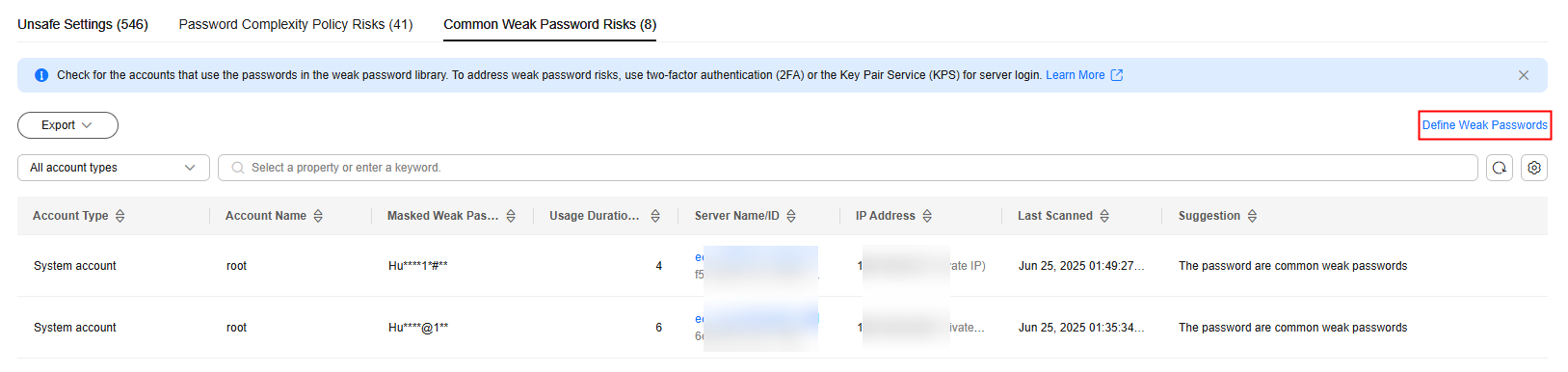
- In the dialog box that is displayed, enter weak passwords and click OK.
HSS will check for the weak passwords you defined in addition to common weak passwords.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





