Connecting ELB to a Cloud Mode WAF Instance on the ELB Console
If your service servers are deployed on the cloud, you can connect your web services to your WAF instance in the cloud load balancer access mode.
You can select Cloud Mode - Load balancer to connect a website to WAF only when the website has used a dedicated load balancer to forward traffic. In this mode, WAF works in the out-of-path mode and does not forward traffic.
This feature is available in certain regions. You can see which regions support this feature on the console.
Overview
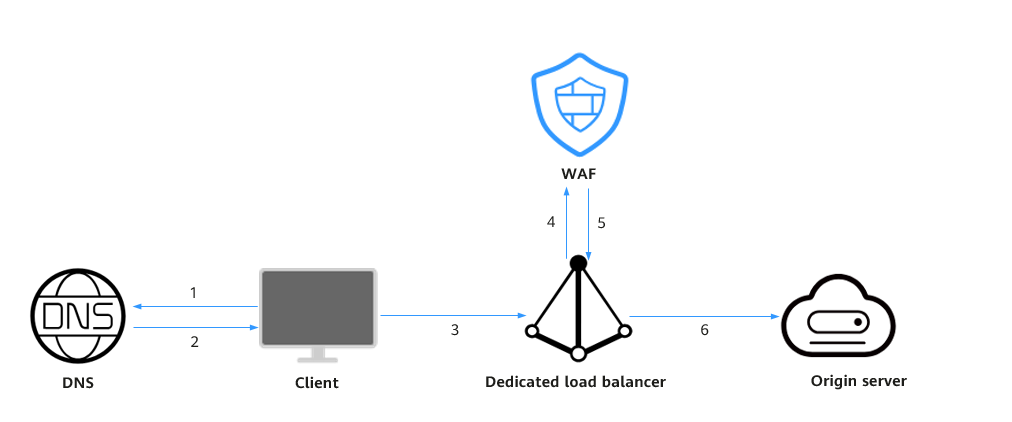
In the cloud load balancer access mode, WAF is integrated into the load balancer gateway through an SDK module. After your website is connected to WAF, the load balancer mirrors the website traffic to WAF. WAF checks the mirrored traffic and sends the check result to the load balancer. The load balancer then determines whether to forward client requests to the origin server based on these check results. In this process, WAF does not forward traffic. This eliminates compatibility and stability issues that might be caused by an additional layer of traffic forwarding.
Figure 1 shows how a website is accessed after being connected to WAF. For details, see Connecting Your Website to WAF (Cloud Mode - Load Balancer Access).
Prerequisites
- You have purchased a cloud WAF instance and learned about the details on how to connect a website to WAF.
- You have purchased an application dedicated load balancer and added an HTTP or HTTPS listener by referring to Adding an HTTP Listener or Adding an HTTPS Listener. You have added the web servers to be protected to the backend server group associated with the load balancer's listener and verified that the load balancer can forward traffic properly.
Procedure
- Go to the load balancer list page.
- On the load balancer list page, click the name of the load balancer you want to connect to the cloud WAF instance.
- Switch to the Associated Services tab and click Add WAF Policy.
Table 1 describes the parameters.
Table 1 Parameters for adding a WAF policy Parameter
Setting
Example Value
Domain Name
Set this parameter to the domain name or IP address (public or private IP address) you want to protect. Make sure that the domain name has been resolved to the EIP of the load balancer.
Domain name: Single domain names or wildcard domain names are supported.- Single domain name: Enter a single domain name, for example, www.example.com.
- Wildcard domain name
- If the server IP address of each subdomain name is the same, enter a wildcard domain name. For example, if the subdomain names a.example.com, b.example.com, and c.example.com have the same server IP address, you can directly add the wildcard domain name *.example.com.
- If the server IP addresses of subdomain names are different, add each subdomain name as a single domain name one by one.
- Wildcard domain name * can be added.
NOTE:WAF can protect both public and private IP addresses. If a private IP address is used, ensure that the corresponding network path is accessible so that WAF can correctly monitor and filter traffic.
Single domain name: www.example.com
Wildcard domain name: *.example.com
IP address:
XXX.XXX.1.1
Listeners
Select listeners to be protected.
- All listeners
- Specific listener
All listeners
WAF Policy
The system-generated policy is selected by default. You can select a policy you configured earlier, or customize rules after the domain name is connected to WAF.
System-generated policies
- Basic web protection (Log only mode and common checks)
The basic web protection defends against attacks such as SQL injections, XSS, remote overflow vulnerabilities, file inclusions, Bash vulnerabilities, remote command execution, directory traversal, sensitive file access, and command/code injections.
- Anti-crawler (Log only mode and Scanner feature)
WAF only logs web scanning tasks, such as vulnerability scanning, virus scanning, and crawling behavior of OpenVAS and Nmap.
NOTE:- Log only: WAF only logs detected attacks instead of blocking them.
- Only the professional and platinum editions allow you to specify a custom policy.
System-generated policy
- Click OK.
You can view the added websites in the protected website list on the WAF console.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot