Configuring Basic Protection Rules to Defend Against Common Web Attacks
After this function is enabled, EdgeSec can defend against common web attacks, such as SQL injections, XSS, remote overflow vulnerabilities, file inclusions, Bash vulnerabilities, remote command execution, directory traversal, sensitive file access, and command/code injections. You can also enable basic web protection, such as web shell detection.
Prerequisites
A protected website has been added. For details, see Adding a Website to EdgeSec.
Constraints
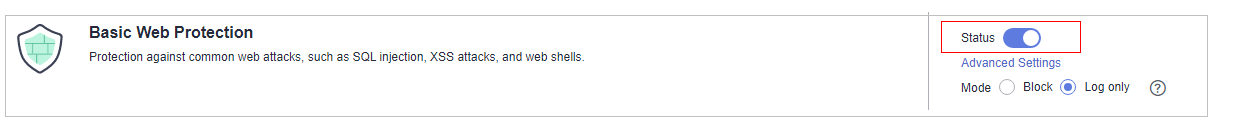
- Basic web protection has two modes: Block and Log only.
- It takes several minutes for a new rule to take effect. After the rule takes effect, protection events triggered by the rule will be displayed on the Events page.
- If you select Block for Basic Web Protection, you can configure access control criteria for a known attack source. EdgeSec will block requests matching the configured IP address, Cookie, or Params for a length of time configured as part of the rule.
Procedure
- Log in to the EdgeSec console.
- In the navigation pane on the left, choose . The Website Settings page is displayed.
- In the Policy column of the row containing the domain name, click the number to go to the Policies page.
Figure 1 Website list

- In the Basic Web Protection configuration area, change Status as needed by referring to Table 1.
- On the Protection Status tab page on the right, enable protection types you need by referring to Table 2.
Figure 2 Basic web protection


If you select Mode for Block, you can select a known attack source rule to let EdgeSec block requests accordingly. For details, see Configuring a Known Attack Source Rule.
- Set the protection type.

By default, General Check is enabled. You can enable other protection types by referring to Table 2.
Table 2 Protection types Type
Description
General Check
Defends against attacks such as SQL injections, XSS, remote overflow vulnerabilities, file inclusions, Bash vulnerabilities, remote command execution, directory traversal, sensitive file access, and command/code injections. SQL injection attacks are mainly detected based on semantics.
NOTE:If you enable General Check, EdgeSec checks your websites based on the built-in rules.
Web Shell Detection
Protects against web shells from upload interface.
NOTE:If you enable Web Shell Detection, EdgeSec detects web page Trojan inserted through the upload interface.
- Set the protection type.
Example - Blocking SQL Injection Attacks
If domain name www.example.com has been connected to EdgeSec, perform the following steps to verify that EdgeSec can block SQL injection attacks.
- Enable General Check in Basic Web Protection and set the protection mode to Block.
Figure 3 Enabling General Check

- Enable EdgeSec basic web protection.
Figure 4 Enabling EdgeSec basic web protection
- Clear the browser cache and enter a simulated SQL injection (for example, http://www.example.com?id=' or 1=1) in the address box.
The access request is blocked. Figure 5 shows an example of the block page.
- Go to the EdgeSec console. In the navigation pane on the left, choose Events. View the event on the Events page.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot








