Why Does an Image Fail to Be Pushed Using a Container Engine Client?
denied: you do not have the permission
Symptom: When you push an image to SWR through your container engine client, the operation fails with the following information returned:
denied: you do not have the permission
Possible causes:
- The organization name you specified has already been used by another user or the maximum number of organizations that you are allowed to create has been reached.
- The docker login command you used to log in to SWR is generated using the AK and SK of an IAM user who does not have the permission of the target organization.
Solutions:
- If the organization name has been used by other users, create an organization with another name first, and then push the image to it. For details about how to create an organization, see Creating an Organization.
- If the maximum number of organizations (5 per user) you are allowed to create has been reached, you can push the image to an existing organization.
- If the IAM user does not have the permission of the target organization, you can authorize this user on either the SWR or IAM console.
Method 1: Log in to the SWR console as an SWR administrator. In the organization list, locate the organization. On the details page of the organization, grant the IAM user the permission to manage this organization. For details, see User Permissions.
Method 2: Use IAM fine-grained authorization to assign a custom policy to this IAM user. This policy contains the permission to push images.- Log in to the IAM console.
- In the navigation pane, choose Permissions > Policies/Roles. Click Create Custom Policy. Enter a policy name and set Policy View to JSON. Enter the policy content as follows (replace namespace1 with the organization name) and click OK.
{ "Version": "1.1", "Statement": [ { "Effect": "Allow", "Action": [ "swr:repo:upload" ], "Resource": [ "SWR:*:*:repo:namespace1/*" ] }, ] }
- In the navigation pane, choose User Groups. Click the name of the user group that the IAM user belongs to. Click Authorize. Select the policy created in 2 for the user group.
- Wait for 1 minute. After the policy takes effect, push the image again.
denied: Image organization does not exist, you should create it first
Symptom: When you push an image to SWR through your container engine client, the operation fails with the following information returned:
denied: Image organization does not exist, you should create it first
Possible cause: The organization name in the docker push command does not exist.
Solution: Create an organization and upload the image again.
"tag does not exist: xxxxxx" or "An image does not exist locally with the tag: xxxxxx" Displayed
Symptom: When you push an image to SWR through your container engine client, the operation fails with the following information returned:
tag does not exist: xxxxxx
Or
An image does not exist locally with the tag: xxxxxx
Possible cause: The image or image tag to be pushed does not exist.
Solution: Run the docker images command to view all the local images. Check the target image name and tag, and push the image again.
name invalid: 'repository' is invalid
Symptom: When you push an image to SWR through your container engine client, the operation fails with the following information returned:
name invalid: 'repository' is invalid
Possible cause: The organization name or image name does not comply with the naming rules.
Solution: The regular expressions of the organization (namespace) name and image (repository) name are as follows:
namespace: The value contains 1 to 64 characters and must meet regular expression ^([a-z]+(?:(?:(?:_|__|[-]*)[a-z0-9]+)+)?)$.
repository: The value contains 1 to 128 characters and must meet regular expression ^([a-z0-9]+(?:(?:(?:_|__|[-]*)[a-z0-9]+)+)?)$.
Specify a valid organization name or image name, and push the image again.
invalid_image, fail to parse 'manifest.json'
Symptom: When you upload an image using the client, the following error message is displayed: invalid_image, fail to parse 'manifest.json'.
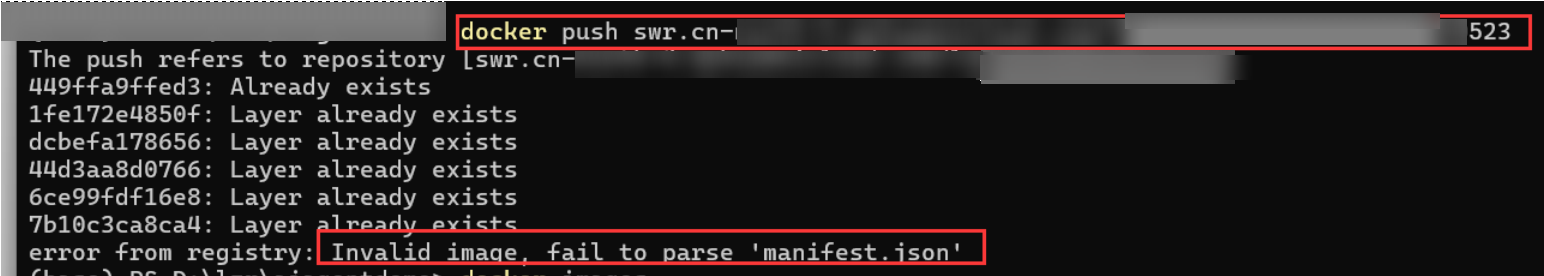
Cause: In SWR Basic Edition, images that comply with the Open Container Initiative (OCI) specifications (v1.0 and v1.1) cannot be uploaded.
Solution: Use SWR Enterprise Edition instead and then upload the image.
Image Push Occasionally Times Out
Symptom: Image push occasionally times out.
Possible cause: When you push an image from a server in Chinese mainland to a server outside Chinese mainland, the network may be unstable.
The Quota of Images That Can Be Uploaded Is Exceeded
The number of images that can be uploaded by a tenant is limited by the quota. There are image quota and image tag quota. If the image quota is exceeded, images cannot be uploaded.
- If the number of uploaded images reaches the quota, new images cannot be uploaded. However, if there are existing images but the number of image tags does not reach the quota, more images can be pushed.
- If the number of tags of an image reaches the quota, the image cannot be uploaded, but other images can still be uploaded.
You can add an image retention policy to delete unused images and then upload new images, or submit a service ticket to increase the quota.
The default quotas are as follows:
- Image quota: 500
- Image tag quota: 300
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





