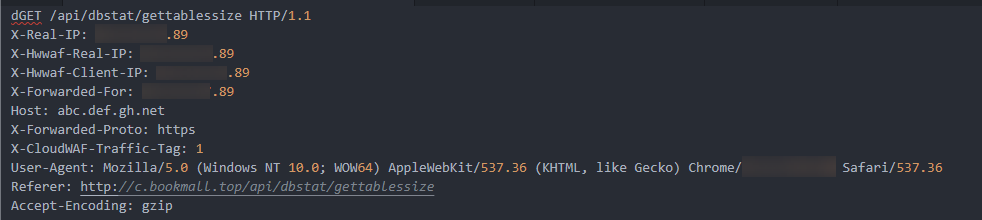
How Do I Obtain the Real IP Address of an Attacker?
After traffic passes through the reverse proxy, the source IP address is translated into the back-to-origin IP address. In this case, if an external attack occurs, CFW cannot obtain the real IP address of the attacker based on the source IP address. You can obtain the real IP address based on the X-Forwarded-For field in attack event logs.
Viewing X-Forwarded-For
- Log in to the CFW console.
- Click
 in the upper left corner of the management console and select a region or project.
in the upper left corner of the management console and select a region or project. - (Optional) Switch to another firewall instance. Select a firewall from the drop-down list in the upper left corner of the page.
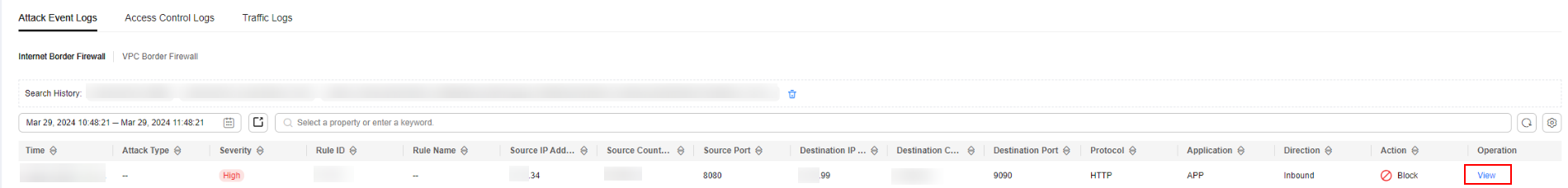
- In the navigation pane, choose Log Audit > Log Query. Click Attack Event Logs tab. In the Operation column of the target event, click View.
Figure 1 Viewing Attack Event Log Details
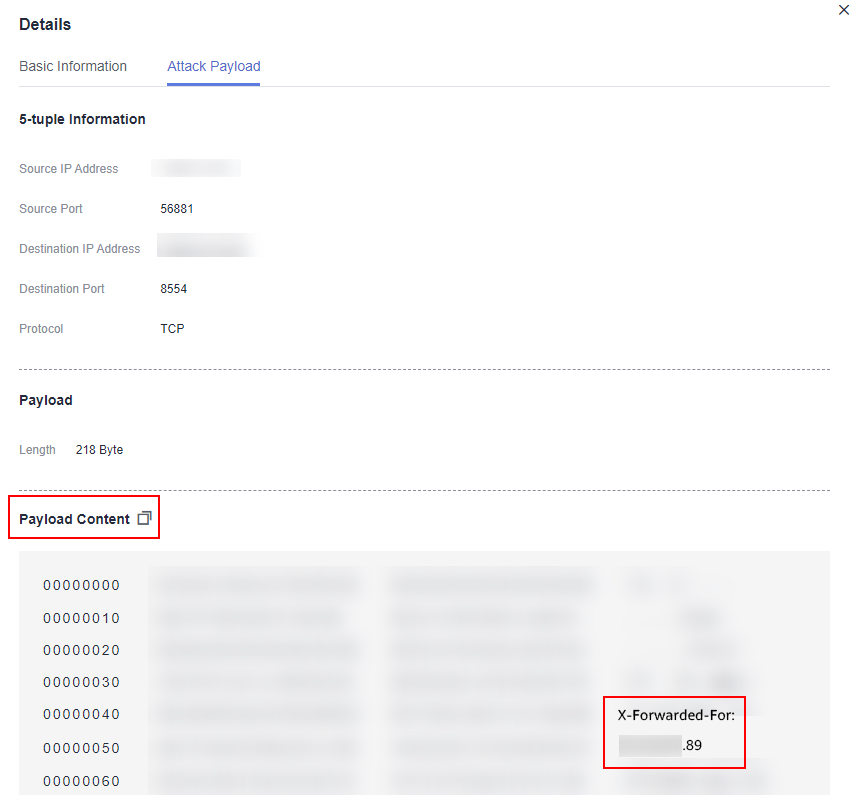
- In the Details page, click the Attack Payload tab, and obtain the value of X-Forwarded-For field.
- Method 1: Check X-Forwarded-For (all IP addresses from the client to the last proxy server) in the Payload Content area.
Figure 2 X-Forwarded-For in the payload
- Method 2: Copy the Payload Content and use the Base64 tool to obtain the decoding result.
X-Forwarded-For: all IP addresses from the client to the last proxy server
For example, the client IP address obtained in Example of the Base64 decoding result is xx.xx.xx.89, and only cloud WAF is used.
- Method 1: Check X-Forwarded-For (all IP addresses from the client to the last proxy server) in the Payload Content area.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot