AK/SK Authentication
- AK indicates the access key ID. It is a unique identifier associated with a secret access key and is used in conjunction with a secret access key to sign requests cryptographically.
- SK indicates the secret access key used together with the access key ID to sign requests. AK and SK can be used together to identify a request sender to prevent the request from being modified.
Generating an AK and SK Pair
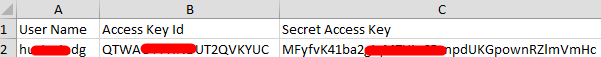
If an AK/SK pair has already been generated, skip this step. Find the downloaded AK/SK file, which is usually named credentials.csv.
As shown in the following figure, the file contains the username, access key ID, and secret access key.
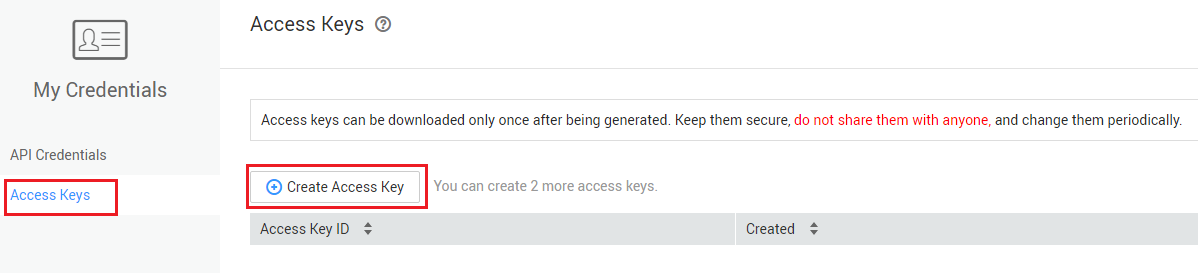
- Log in to the management console.
- Click the username in the upper right corner and choose My Credentials from the drop-down list.
- On the My Credentials page, choose Access Keys.
- Click Create Access Key.
- Enter the password and verification code, and click OK to download the access key. Keep the access key secure.
Generating a Signature
Generate a signature in the same way as in App authentication mode. Replace AppKey with AK and replace AppSecret with SK to complete the signing and request processing.
The client must synchronize the local time with the clock server to avoid a large offset in the value of X-Sdk-Date in the request header.
In addition to verifying the time format of X-Sdk-Date, ROMA Connect also verifies the time difference between the time specified by X-Sdk-Date and the actual time when the request is received. If the time difference exceeds 15 minutes, ROMA Connect rejects the request.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





