Confused Deputy Problem
The confused deputy problem occurs when a low-permission principal tricks a high-permission principal into performing unauthorized actions on their behalf. Huawei Cloud provides multiple measures to help you securely grant access to your account resources to third party accounts or other Huawei Cloud services.
You may need a third-party company to monitor your Huawei Cloud account to optimize costs, and authorize a third party account to access your resources. The third-party company may monitor many Huawei Cloud accounts for other customers. You can use an IAM trust agency to establish a trust relationship between your Huawei Cloud account and the third-party company account. The external ID is a key element for preventing confused deputy. You can use it in the trust policy of a trust agency to specify who can assume the agency.
In cloud service delegation, you may authorize some cloud services to operate resources in your account. For example, you create and configure a trust agency for a cloud service. You assign the trust agency to the tasks of the cloud service. Since the URN of the trust agency is not a secret, an attacker can run a task in the cloud service that assumes the trust agency. The confused deputy problem occurs. To address such risk, you can add the g:SourceAccount and g:SourceUrn condition keys to the trust policy of the trust agency for the cloud service.
Preventing Cross-Account Confused Deputy
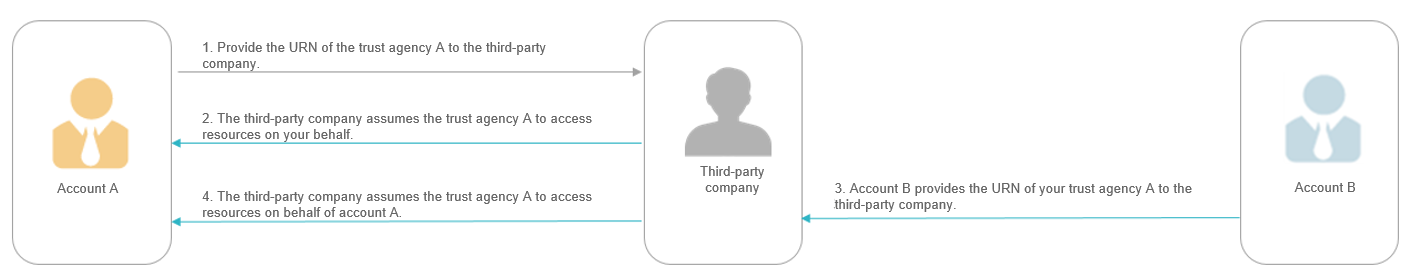
In this example, your account A created the trust agency A to trust a third-party company. Here is how confused deputy occurred:
- When you use the third-party company's service, you provide the URN of trust agency A to the third-party company.
- The company uses the URN of the trust agency to obtain temporary security credentials to access resources in your account.
- Account B also starts using the third-party company's service. Because the URN of trust agency A is not confidential, account B may have guessed the URN of trust agency A and provided it to the third-party company.
- When account B asks the company to access resources in its (what it claims to be) account, the company uses the URN of trust agency A to access resources in account A.
This is how another account can access your resources without your authorization. Account B can now trick the company into operations on your resources, so the company is now a confused deputy.
{
"Version": "5.0",
"Statement": [{
"Action": [
"sts:agencies:assume"
],
"Effect": "Allow",
"Principal": {
"IAM": [
"AccountA ID"
]
},
"Condition": {
"StringEquals": {
"sts:ExternalId": [
"123456"
]
}
}
}]
}
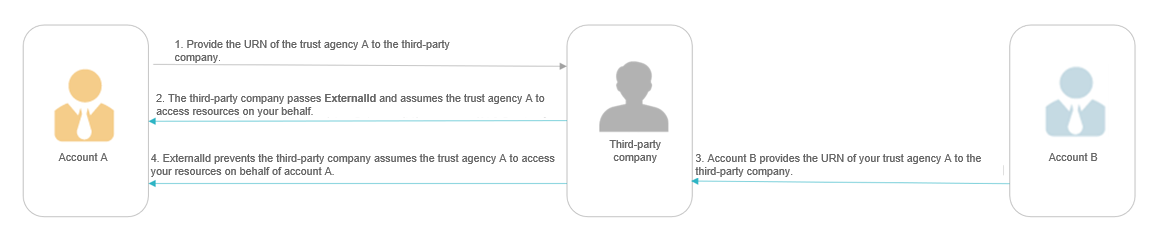
- As before, when you use the third-party company's service, you provide the URN of trust agency A to the third-party company.
- The third-party company calls the AssumeAgency API and passes the ExternalId to obtain the temporary security credentials of trust agency.
- Account B also starts using the third-party company's service, and provides the URN of trust agency A to the third-party company.
- But this time, when account B requests the third-party company to access the so called "its" resources, the third-party company calls the AssumeAgency API and passes the ExternalId (456789) associated with account B. Since you only added your ExternalId (123456) but not the ExternalId (456789) of account B to the trust policy, the AssumeAgency API fails to use the URN of trust agency A.
Preventing Cross-Service Confused Deputy
To prevent unauthorized accounts from accessing your Huawei Cloud resources using trust agencies, Huawei Cloud service principals provide the information about the Huawei Cloud accounts and resources they represent. This information is included in the request context in the form of global condition keys g:SourceAccount and g:SourceUrn. The two condition keys can be used to solve the cross-service confused deputy problem.
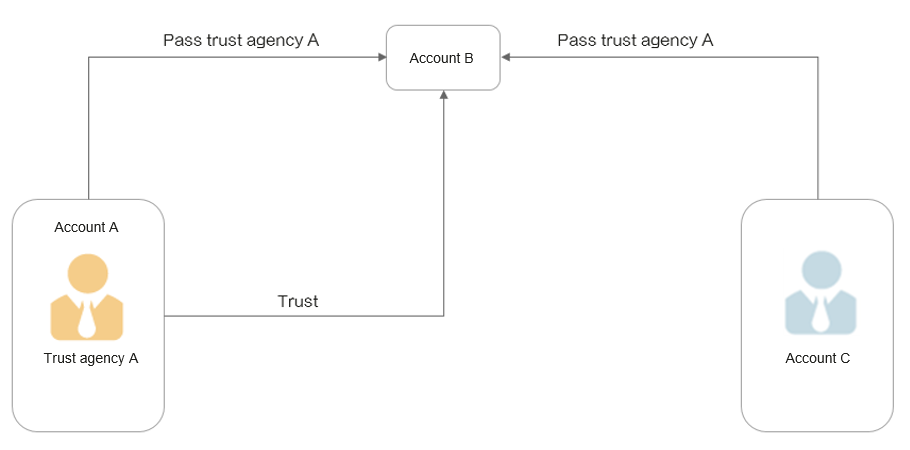
In the following example, account A creates a trust agency A, trusts the cloud service B, and attaches the trust agency to the tasks of cloud service B.
{
"Version": "5.0",
"Statement": [{
"Action": [
"sts:agencies:assume"
],
"Effect": "Allow",
"Principal": {
"Service": [
"service.B"
]
}
}]
}
The trust agency URN is not a secret. If attacker account C runs a task in service B and uses trust agency A for task execution, service B may use trust agency A to access your resources. The cross-service confused deputy occurs. The following describes how to use the global condition keys g:SourceAccount and g:SourceUrn to solve this problem.
- g:SourceAccount
g:SourceAccount specifies the account for which cloud services acquire temporary credentials. If you add the g:SourceAccount condition key when creating a trust agency for service B, service B can only use trust agency A to obtain temporary credentials for account A. If attacker account C also sends a request to service B, IAM will check the condition key and reject the request.
{ "Version": "5.0", "Statement": [{ "Action": [ "sts:agencies:assume" ], "Effect": "Allow", "Principal": { "Service": [ "service.B" ] }, "Condition": { "StringEquals": { "g:SourceAccount": [ "AccountA ID" ] } } }] }
- g:SourceUrn
g:SourceUrn specifies the resource for which cloud services acquire temporary credentials. If you add the g:SourceUrn condition key when creating a trust agency for service B, service B can only use trust agency A to obtain temporary credentials for the specified resource. If attacker account C also sends a request to service B, IAM will check the g:SourceUrn condition key and reject the request.
{ "Version": "5.0", "Statement": [{ "Action": [ "sts:agencies:assume" ], "Effect": "Allow", "Principal": { "Service": [ "service.B" ] }, "Condition": { "StringEquals": { "g:SourceUrn": [ "Specific Resource URN" ] } } }] }
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





