Event Management
DSC integrates with key security components, including Database Audit, and Cloud Bastion Host, enabling centralized event management and real-time event delivery to DSC. This allows users to promptly verify and handle events. You can also convert alarms on the Alarm Management page to events.
Prerequisites
The DBSS service has been enabled and there are available assets on it. For details, see Purchasing Database Audit.
Creating an Event
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation tree on the left, choose . The Event Management page is displayed.
- Click Create in the upper left corner. The page for creating an event is displayed.
- Set the event parameters based on Table 1.
Table 1 Event parameters Parameter
Description
Event Name
The value can contain 4 to 255 characters, including letters, digits, hyphens (-), and underscores (_), and must start with a letter.
Type
Select an event type from the drop-down list box.
Database- SQL Injection
- Risky operations
Event Level
Select an event level from the drop-down list box.
- Suggestion
- Low
- Medium
- High
- Critical
Status
Select a status from the drop-down list box.
- Open
- Blocked
- Closed
Module
Select a source function module from the drop-down list box.
- Database auditor
- Cloud bastion host
Instance
Select an event source instance from the drop-down list box.
Owner
Select an event handling owner from the drop-down list box.
Affected Assets (Optional)
Enter the information about the assets affected by the event.
Occurred On
Time when an event occurs for the first time.
Planned Closure Time
Time when an event is planned to be closed.
Recommended Handling Method (Optional)
Enter the recommended event handling method. A maximum of 1000 characters can be entered.
Verification Status
Select an event verification status from the drop-down list box.
- Unknown
- Confirmed
- False
Description
Enter the event description.
- Click OK.
Viewing the Event Management List
- Log in to the DSC console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation tree on the left, choose . The Event Management page is displayed.
- View the number of unhandled events and the total number of events.
The doughnut chart displays the number of expired and unexpired events.
Figure 1 Event handling statistics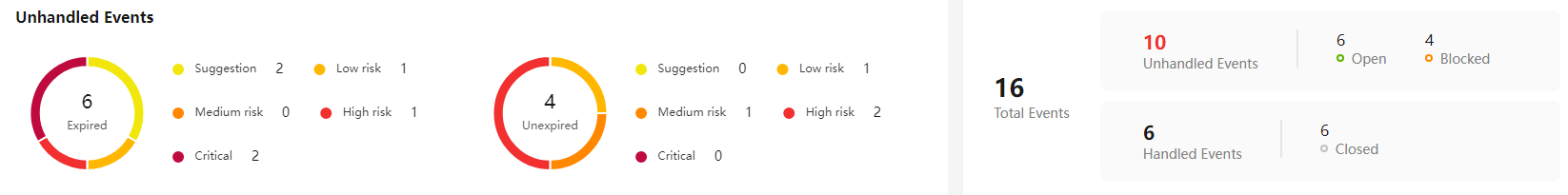
- View the alarm list. For details about the parameters, see Table 2.
Table 2 Data risk event parameters Parameter
Description
Event Name/ID
- Name of an event. The event name should denote the content of the event. You can click the event name on the right of the event name to view the basic information, handling suggestions, and associated alarms of the event.
- Click the event name to view the event details.
Event Level
There are five event levels:
- Suggestion
- Low
- Medium
- High
- Critical
Subcategory/Category
Event sources are classified into the following categories:
- Database attacks
Source
Database audit and instance names.
Status
The status options are:
- Open
- Blocked
- Closed
Affected Assets
Affected databases
Verification Status
Its value can be:
- Unknown
- Confirmed
- False
Owner
Username.
Created
Event creation time
Occurred On
Time when an event occurs for the first time.
Planned Closure Time
Time when an event is planned to be closed.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





