Authentication Based on Ranger
Scenario
Create and configure an Elasticsearch permission control policy on Ranger to manage Elasticsearch users' permissions to create and delete indexes.
Users can query, update, and delete data only when they have the operation permission on the specified data in Elasticsearch.

- In security mode, you can create policies in Ranger. In normal mode, Ranger cannot be used for permission control.
- In security mode, the newly installed Elasticsearch cluster uses the Ranger-based authentication mode by default.
- In Ranger-based authentication mode, the authentication information of a newly created role does not take effect on the Elasticsearch service.
Prerequisites
- The Elasticsearch and Ranger services have been installed and are running properly.
- User permissions have been planned based on service requirements.
Procedure
- Add the Elasticsearch access permission policy to Ranger by referring to Adding a Ranger Access Permission Policy for Elasticsearch.
- View the current default policies.
- Log in to the Ranger management page as users in the supergroup owner group, user elasticsearch or user rangeradmin by referring to Logging In to the Ranger Web UI.
- On the home page, click Elasticsearch in the ELASTICSEARCH area to view the current default policies.

Contact the system administrator to obtain the default password of user elasticsearch or rangeradmin. The actual situation prevails.
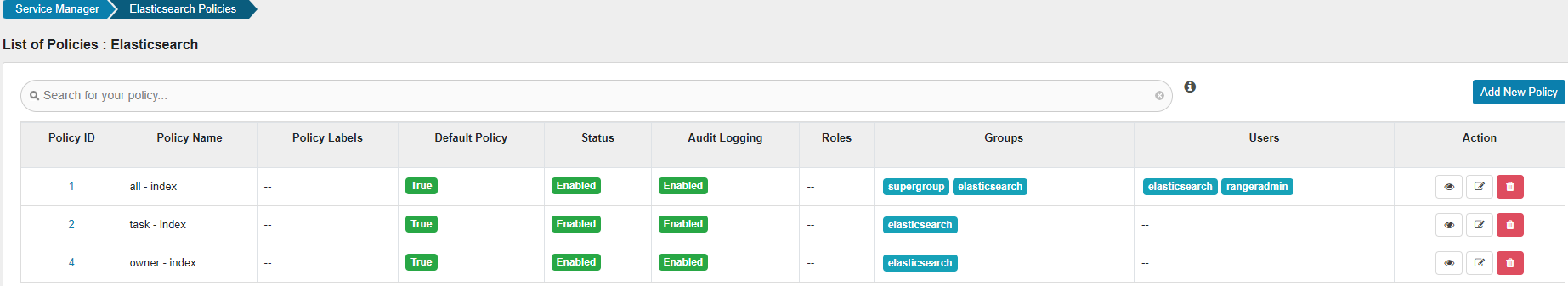
Elasticsearch has three default policies, which can be maintained only by users in the supergroup owner group, user elasticsearch or user rangeradmin. You can view and modify the default policies in the Action column. Changing default policies is a high-risk operation and deleting default policies is a forbidden operation.
For details about the default policy, see Table 1, Table 2, and Table 3.
Table 1 Default policy all - index Parameter
Default Value
Description
Policy Name
all - index
Indicates a policy name. The default policy status is enabled or normal.
Policy Label
-
-
Index
*
Indicates that the policy takes effect for all indexes.
Description
Policy for all - index
-
Audit Logging
Yes
Indicates that the audit function is enabled for the policy.
Allow Conditions
- Select Role:
- Select Group:
- Select User: rangeradmin
- Policy Conditions:
- Permissions: read index delete monitor manage view_index_metadata create create_index write
- Delegate Admin:
Indicates the permissions granted to user rangeradmin, allowing the user to read, write, update, delete, monitor, manage, and view index metadata, as well as create indexes, create documents, and write data.
Users in the condition are not allowed to manage the policy.
- Select Role:
- Select Group:
- Select User: elasticsearch
- Policy Conditions:
- Permissions: all monitor delete manage view_index_metadata read read_cross_cluster index create delete write delete_index create_index cluster_monitor cluster_manage indices_put indices_search_shards indices_put indices_index cat_index_recovery cat_index_metadata clear_search_scroll asynchronous_search script vector
- Delegate Admin: YES
Indicates all execution permissions granted to user elasticsearch.
Users in the condition are allowed to manage the policy.
- Select Role:
- Select Group: supergroup
- Select User:
- Policy Conditions:
- Permissions: all monitor delete manage view_index_metadata read read_cross_cluster index create write delete_index create_index cluster_monitor cluster_manage asynchronous_search script vector
- Delegate Admin: YES
Indicates all execution permissions granted to group supergroup.
The user in the permit condition manages the policy.
- Select Role:
- Select Group: elasticsearch
- Select User:
- Policy Conditions:
- Permissions: cluster_monitor asynchronous_search create_index
- Delegate Admin:
The permissions to monitor clusters and create indexes are assigned to the elasticsearch user group.
Users in the condition are not allowed to manage the policy.
Deny All Other Accesses
False
All other access permissions are accepted.
Table 2 Default policy task - index Parameter
Default Value
Description
Policy Name
task - index
Indicates a policy name. The default policy status is enabled or normal.
Policy Label
-
-
Index
.*
Indicates that the policy takes effect for all indexes starting with a dot.
Description
Policy for all - path
-
Audit Logging
Yes
Indicates that the audit function is enabled for the policy.
Allow Conditions
- Select Role :
- Select Group: elasticsearch
- Select User:
- Policy Conditions:
- Permissions: index read delete monitor manage create create_index view_index_metadata write
- Delegate Admin: YES
Indicates the permissions granted to user group elasticsearch, allowing the user to read, write, update, delete, monitor, manage, and view index metadata, as well as create indexes, create documents, and write data.
The user in the permit condition manages the policy.
Deny All Other Accesses
False
All other access permissions are accepted.
Table 3 Default policy owner - index Parameter
Default Value
Description
Policy Name
task - index
Indicates a policy name. The default policy status is enabled or normal.
Policy Label
-
-
Index
index_owner_info .index_owner_info
The policy takes effect for indexes index_owner_info and .index_owner_info.
Description
Policy for all - path
-
Audit Logging
Yes
Indicates that the audit function is enabled for the policy.
Allow Conditions
- Select Role :
- Select Group: elasticsearch
- Select User:
- Policy Conditions:
- Permissions: read
- Delegate Admin: YES
The read permission is assigned to users in the elasticsearch group.
Users in the condition are allowed to manage the policy.
- Select Role:
- Select Group: supergroup
- Select User:
- Policy Conditions:
- Permissions: all monitor delete manage view_index_metadata read read_cross_cluster index create write delete_index create_index cluster_monitor cluster_manage asynchronous_search script vector
- Delegate Admin: YES
Indicates all execution permissions granted to users in the supergroup group.
Users in the condition are allowed to manage the policy.
Deny All Other Accesses
True
All other access permissions are denied.
For details about the Elasticsearch user group permissions in Ranger authentication, see Table 4.
Table 4 Elasticsearch user group permissions User Group
User Permission
supergroup
This user can create indexes, read and write all indexes, manage all indexes and the Elasticsearch cluster, and create asynchronous search and pre-aggregation tasks.
elasticsearch
Users in this group can execute cluster and cat query APIs, excluding cat count.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





