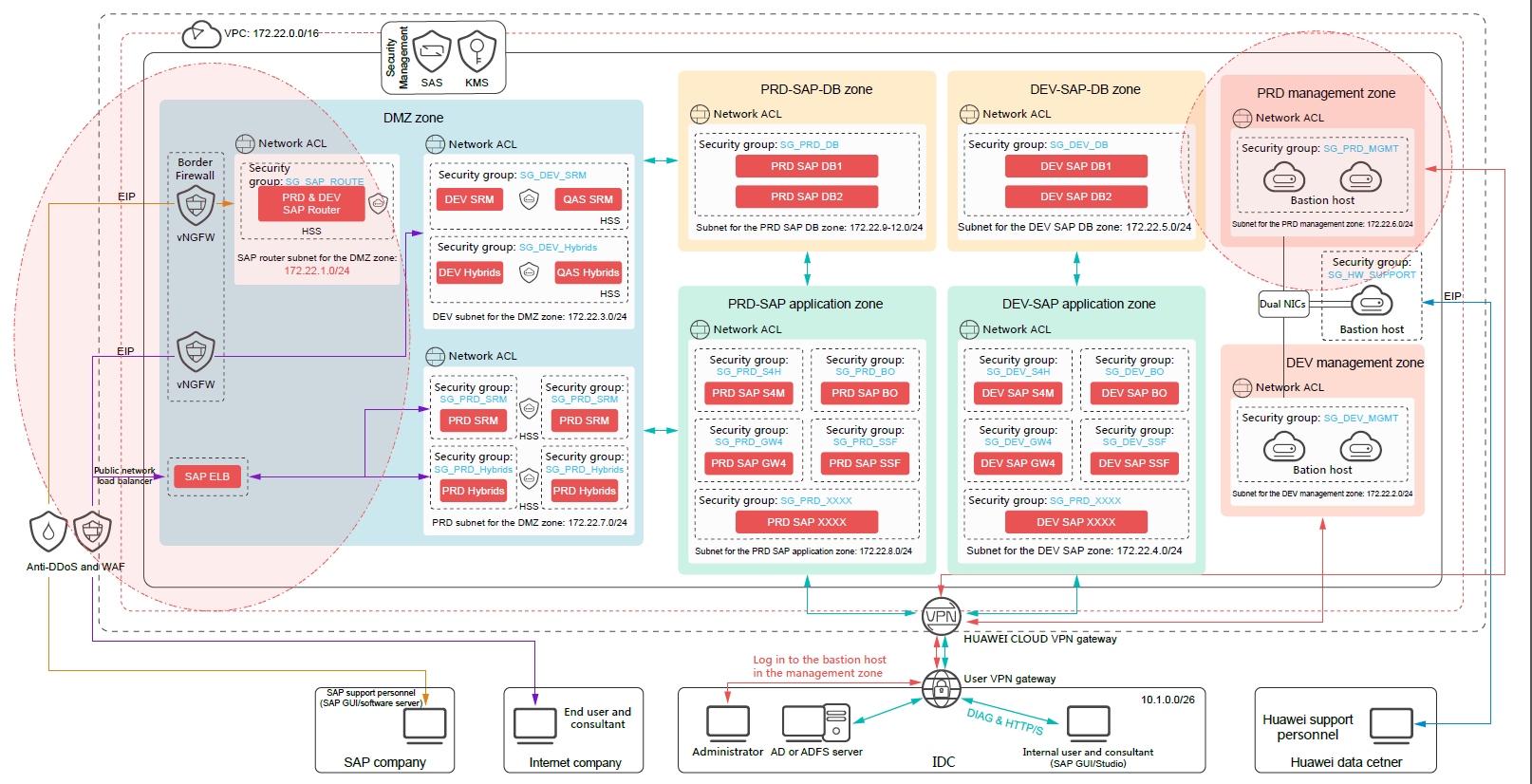
Network Isolation and Access Control
Figure 1 shows the SAP production environment security solution.
After service characteristics and enterprise security practices are taken into consideration, it is recommended that you divide the cloud-based system (production environment and development and test environment) into zones of different security levels, including the management, application, SAP DB, and demilitarized zone (DMZ) zones. The zones are isolated from each other using subnets.
The DMZ zone is special because it interacts with the Internet and is shared by the production system and the development and test system. It is recommended that you configure specific security policies for each zone to control inter-zone access and access from external networks.
- DMZ zone: This zone directly interconnects with the Internet. All service system access requests from public network users and SAP support personnel are processed in the zone. The DMZ zone has a low security level and a high security risk.
- Application zones: SAP applications are deployed in the zones for integrated data center (IDC) users (enterprise internal users) to use and for interconnection with systems including the AD server. The zones have a higher security level than the DMZ zone.
- SAP DB zones: SAP databases are deployed in the zones. The zones allow limited access from the internal network application and management zones and have the highest security level.
- Management zones: Operations and maintenance (O&M) bastion hosts are deployed in the zones. The zones are the intermediary areas through which system O&M personnel (in an enterprise) manage, operate, and maintain Elastic Cloud Servers (ECSs) and systems in other zones.
Configure specific security policies for each zone using security groups and network access control lists (ACLs) to control inter-zone access and access from external networks. Configure security policies according to the "deny by default" and "minimum permission" principles, allowing only access from specified sources to required IP addresses and ports.
For example, only administrators in an enterprise are allowed to access the remote access port of the bastion host in management zones. Common users and internal systems are not allowed to access the port. Common users in an enterprise should be allowed to access only SAP service ports in internal network application zones. Network ACLs are used to deny traffic between all zones (isolated using subnets) in the system by default. Necessary services must be allowed by adding ACL rules.
This section describes the access control policies between the zones in a production environment. This section also provides suggestions on network ACL and security group configuration according to the "deny by default" and "minimum permission" principles. (The development and test environment is special. To ensure that IDC users can efficiently access the internal resources and that networking is flexible, looser access control policies are configured for the development and test environment than for the production environment. For details, see Development and Test Environment Security Solution.)
Security Policies
As shown in Figure 2, the production environment has eight subnets. It is recommended that you create an independent network ACL for each subnet. These network ACLs include NACL-DMZ-SAP-Router, NACL-PRD-DMZ, NACL-PRD-APP, NACL-PRD-SAPDB-BUSI, NACL-PRD-SAPDB-INTERNAL, and NACL-PRD-MGMT.
Network ACL NACL-DMZ-SAP-Router is associated with the subnet for the DEV&PRD-SAP router shared by the production environment and the development and test environment. Configure outbound rules of network ACL NACL-DMZ-SAP-Router to allow access to specified service ports of the SAP application zone and SAP-DB zone in the production environment through the SAP router. Configure inbound rules of network ACL NACL-DMZ-SAP-Router to allow access to management ports (such as port 22) of servers in the subnet through the bastion host in the management zone.

IP addresses and ports in this section are only used as examples. If there are other management ports, you can add ACL rules as required. This section describes only network ACLs for the production environment.
|
Rule |
Destination IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-application zone |
172.22.8.0/24 |
TCP |
234 |
Allow |
Allows the SAP-Router server to access service port 234 of servers in the PRD-application zone. |
|
For the PRD-SAP-DB zone |
172.22.9.0/24 |
TCP |
345 |
Allow |
Allows the SAP-Router server to access service port 345 of servers in the PRD-SAP-DB zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
|
Rule |
Source IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-management zone |
172.22.6.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH ports of servers in the zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
Network ACL NACL-PRD-MGMT is associated with the subnet for the PRD-management zone in the production environment. Configure outbound rules of network ACL NACL-PRD-MGMT to allow access to management ports (such as port 22) of servers in other zones through the bastion host in the management zone and deny access from other zones to the bastion host in the management zone.
|
Rule |
Destination IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-DMZ zone |
172.22.7.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH ports of servers in the PRD-DMZ zone. |
|
For the PRD-application zone |
172.22.8.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH ports of servers in the PRD-application zone. |
|
For the PRD-SAP-DB zone |
172.22.9.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH ports of servers in the PRD-SAP-DB zone. |
|
For the DEV&PRD SAP router |
172.22.1.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH port of the DEV&PRD-SAP-Router server. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all outbound traffic that is not processed based on preset rules. |
|
Rule |
Source IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
Network ACL NACL-PRD-DMZ is associated with the subnet for the PRD-DMZ zone in the production environment. Configure inbound rules of network ACL NACL-PRD-DMZ to allow access to management ports (such as port 22) of servers in the zone through the bastion host in the management zone. Configure outbound rules of network ACL NACL-PRD-DMZ to allow access to required service ports in the PRD-application zone and PRD-SAP-DB zone through this subnet.
|
Rule |
Destination IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-application zone |
172.22.8.0/24 |
TCP |
8080 |
Allow |
Allows hosts in the DMZ zone in the production environment to access service port 8080 of servers in the PRD-application zone. |
|
For the PRD-application zone |
172.22.8.0/24 |
TCP |
8443 |
Allow |
Allows hosts in the DMZ zone in the production environment to access service port 8443 of servers in the PRD-application zone. |
|
For the PRD-SAP-DB zone |
172.22.9.0/24 |
TCP |
345 |
Allow |
Allows hosts in the DMZ zone in the production environment to access service port 345 of servers in the PRD-SAP-DB zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all outbound traffic that is not processed based on preset rules. |
|
Rule |
Source IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-management zone |
172.22.6.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH ports of servers in the zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
Network ACL NACL-PRD-APP is associated with the subnet for the PRD-application zone in the production environment. Configure inbound rules of network ACL NACL-PRD-APP to allow access to management ports (such as port 22) of servers in the zone through the bastion host in the management zone and allow access to service ports of servers in this subnet through the SAP router and PRD-DMZ zone. Configure outbound rules of network ACL NACL-PRD-APP to allow access to required service ports in the PRD-SAP-DB zone through this subnet.
|
Rule |
Destination IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-SAP-DB zone |
172.22.9.0/24 |
TCP |
345 |
Allow |
Allows hosts in the application zone in the production environment to access service port 345 of servers in the PRD-SAP-DB zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all outbound traffic that is not processed based on preset rules. |
|
Rule |
Source IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-management zone |
172.22.6.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH ports of servers in the zone. |
|
For the DEV&PRD SAP router |
172.22.1.0/24 |
TCP |
234 |
Allow |
Allows the SAP-Router server to access service port 234 of servers in the PRD-application zone. |
|
For the PRD-DMZ zone |
172.22.7.0/24 |
TCP |
8080 |
Allow |
Allows hosts in the DMZ zone in the production environment to access service port 8080 of servers in the PRD-application zone. |
|
For the PRD-DMZ zone |
172.22.7.0/24 |
TCP |
8443 |
Allow |
Allows hosts in the DMZ zone in the production environment to access service port 8443 of servers in the PRD-application zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
Network ACL NACL-PRD-SAPDB-BUSI is associated with the service subnet (172.22.9.0/24) for the PRD-SAP-DB zone in the production environment. Configure inbound rules of network ACL NACL-PRD-SAPDB-BUSI to allow access to management ports (such as port 22) of servers in the zone through the bastion host in the management zone and allow access to service ports of servers in this subnet through the SAP router, PRD-DMZ zone, and PRD-application zone.
|
Rule |
Destination IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all outbound traffic that is not processed based on preset rules. |
|
Rule |
Source IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
For the PRD-management zone |
172.22.6.0/24 |
TCP |
22 |
Allow |
Allows the bastion host in the management zone in the production environment to access the SSH ports of servers in the zone. |
|
For the DEV&PRD SAP router |
172.22.1.0/24 |
TCP |
345 |
Allow |
Allows the SAP-Router server to access service port 345 of servers in the PRD-SAP-DB zone. |
|
For the PRD-DMZ zone |
172.22.7.0/24 |
TCP |
345 |
Allow |
Allows hosts in the DMZ zone in the production environment to access service port 345 of servers in the PRD-SAP-DB zone. |
|
For the PRD-application zone |
172.22.8.0/24 |
TCP |
345 |
Allow |
Allows hosts in the application zone in the production environment to access service port 345 of servers in the PRD-SAP-DB zone. |
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
Network ACL NACL-PRD-SAPDB-INTERNAL is associated with the internal communication subnet (172.22.10-12.0/24) for the PRD-SAP-DB zone in the production environment. The internal communication subnet is used for only internal communication within a subnet and requires a network ACL to deny all inbound and outbound traffic.
|
Rule |
Destination IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all outbound traffic that is not processed based on preset rules. |
|
Rule |
Source IP Address |
Protocol |
Destination Port |
Allow or Deny |
Description |
|---|---|---|---|---|---|
|
* |
0.0.0.0/0 |
Any |
Any |
Deny |
Denies all inbound traffic that is not processed based on preset rules. |
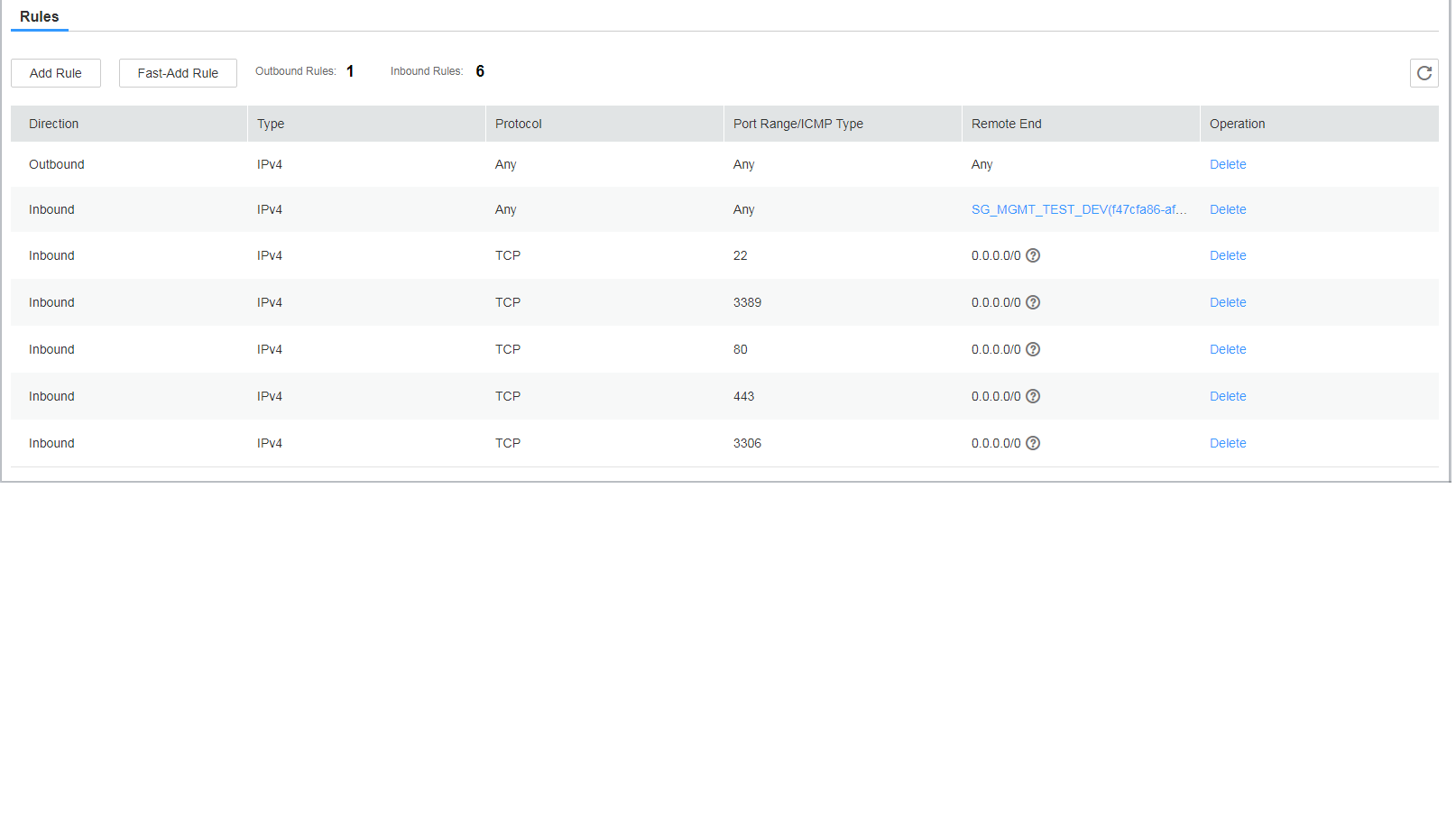
Security groups, such as SG_PRD_MGMT and SG_PRD_DB (which do not interact with the public network), are associated with Elastic Cloud Servers (ECSs) in the subnets in the production environment. The security groups must be configured according to the "minimum permission" principle so that a minimum number of ECS ports are opened. Figure 3 shows an example for configuring the security groups. You need to configure them based on your own ports. Network ACLs are used for IP address access control. Other security groups in the production environment (for details, see Figure 1) that do not interact with the public network can be configured similarly.
Security groups, such as SG_SAP_ROUTER (which interacts with the public network), are associated with ECSs in the subnets in the production environment. The security groups must be configured according to the "minimum permission" principle so that a minimum number of ECS ports and source IP addresses are opened. If the public IP address is fixed, you can refer to Figure 3 for configuring the security groups. You need to configure them based on your own ports.
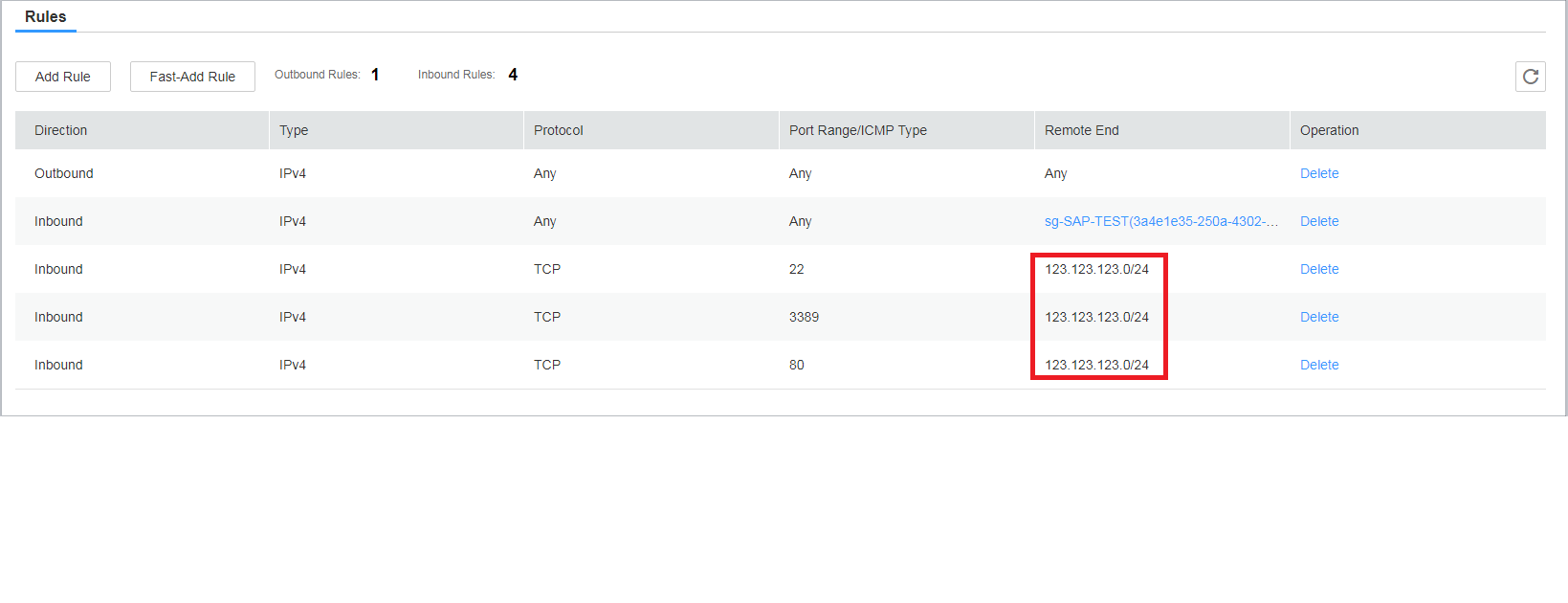
If the public IP address is not fixed, you can create a security group rule to allow access from a specified public source IP address to meet your service requirements (such as the simulation test or technical support) and then delete the rule when it is not required.
Security groups, such as SG_PRD_SRM and SG_PRD_Hybrids (which interact with the public network), need to open their service ports to the entire network. Figure 5 shows an example for configuring the security groups. You need to configure them based on your own ports. Network ACLs are used for source IP address access control on management ports, such as ports 22 and 3389, so that only access through the bastion host in the management zone is allowed. Service ports, such as port 80, are opened to the entire Internet and will not be configured with source IP address access control. It is recommended that you use proper security products to protect these ports. For details, see Service Border.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot