Malicious Files
Context
Huawei Qiankun determines the detection type of a threat event based on logs provided by the device. If the detection type is AV/CDE, the threat event is identified as a malicious file event.
If the malicious file is blocked when the device detects it, the status of the malicious file event is Blocked. If the malicious file is not blocked when the device detects it, the status of the malicious file event is Unhandled.
For malicious files that are in Blocked or Unhandled state, Huawei Qiankun can send SMS and email alarms to notify tenants or deliver an IP address blacklist.
Tenants need to handle the malicious files in Unhandled state and mark them as Manually handled or Ignored.
Procedure
- Log in to the Huawei Qiankun console, and choose .
- Click in the menu bar.
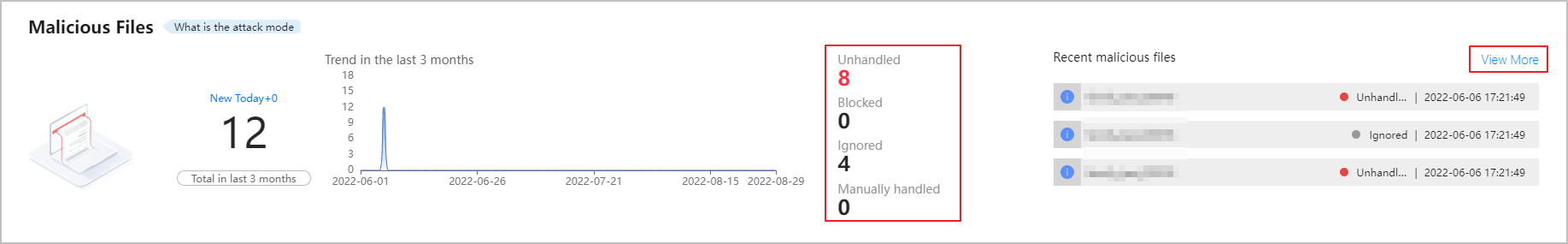
- Check the overview of malicious files, and click a number or View More to view details.
Figure 1 Overview of malicious files
- Mark the status of unhandled malicious files.
- Manually handled
Tenants manually handle specific events, for example, searching for and clearing malicious files based on the source and destination addresses of events, and file names.
After confirming that malicious files have been cleared from hosts, mark the events as Manually handled in the Operation column.
- Ignored
If the events are false positives or do not need to be handled, mark the events as Ignored in the Operation column.
If you do not know how to handle the problem or the problem persists after you handle it, contact the corresponding Managed Security Service Provider (MSSP) or channel partner.
- Manually handled
Follow-up Procedure
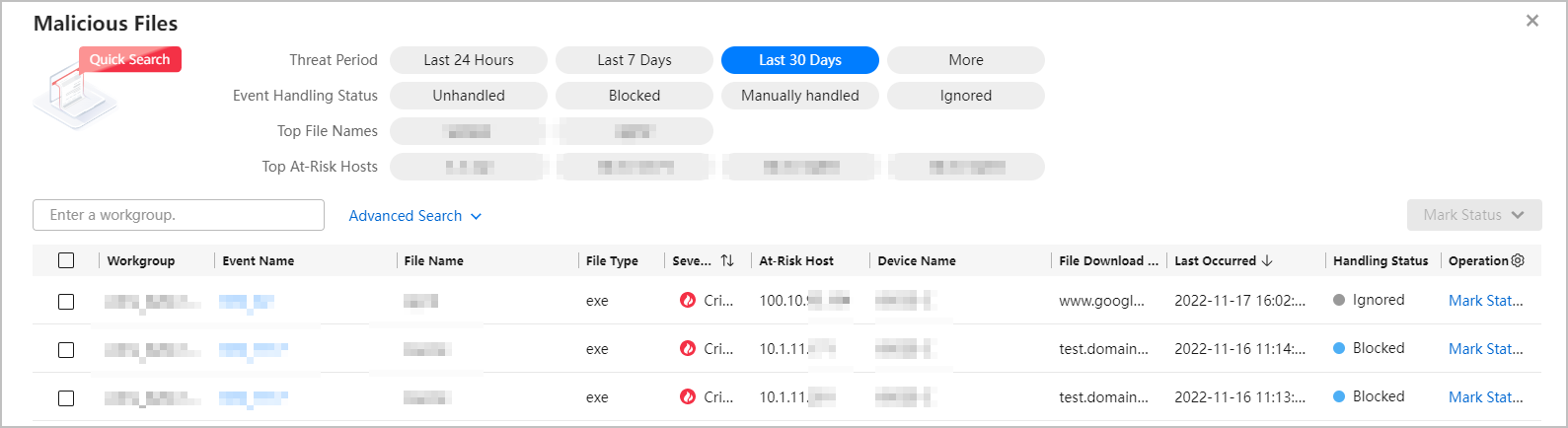
- On the Malicious Files page, you can click an event name to view details of the malicious file event.
Figure 2 Malicious Files page
- The Malicious File Details page contains Handling Suggestions, Operation Records, and Threat Analysis.
Figure 3 Malicious File Details page
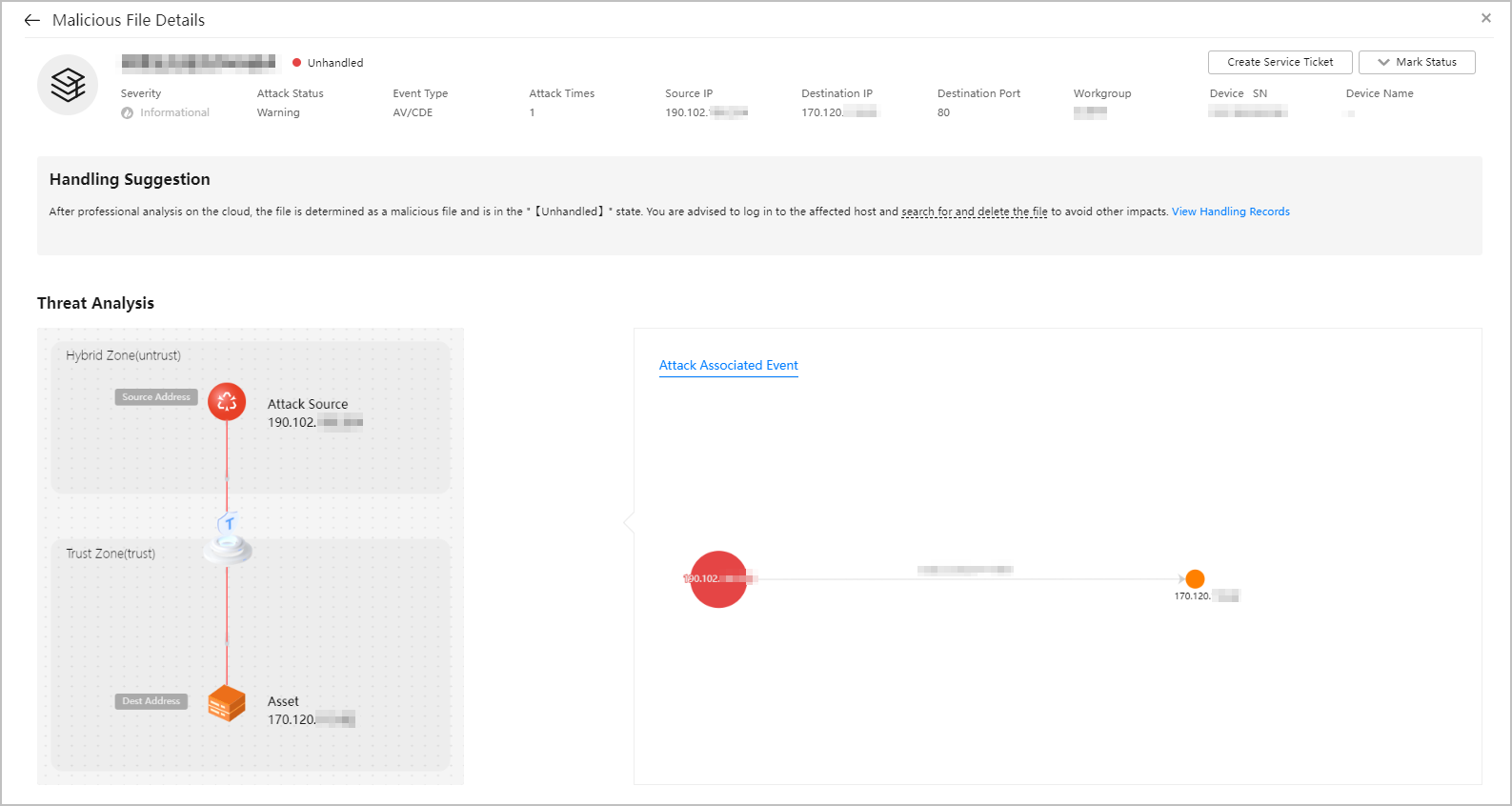
On the Malicious File Details page, the event names and malicious file information may contain public IP addresses, helping you learn about threat events. The service does not proactively initiate connections to these public IP addresses.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






