What Is the Border Protection and Response Service?
The Border Protection and Response Service uses Qiankun Shield devices to provide border protection for tenants' local networks. It also performs intelligent analysis and handling based on logs provided by Qiankun Shield devices, ensuring the enterprise intranet security. Huawei Qiankun integrates detection models, such as alarm-based automatic confirmation and threat analysis, to intelligently identify potential threats on tenants' local networks and automatically handle these threats. In this way, tenants can benefit from simplified local O&M and improved security protection.
Logical Architecture
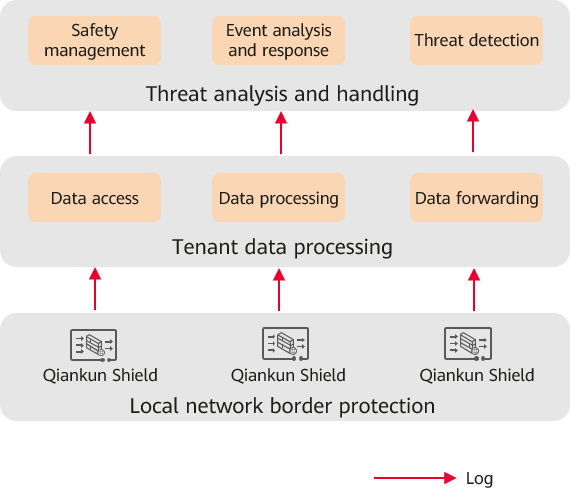
As shown in Figure 1, the Border Protection and Response Service is implemented in three stages.
- Local network border protection: Qiankun Shield devices deployed at the tenant network border ensure the security of the local network border with functions such as intrusion prevention, antivirus, and DNS filtering.
- Tenant data processing: The data access center of Huawei Qiankun processes logs from Qiankun Shield devices and persistently stores service data.
- Threat analysis and handling: After obtaining service data, the threat analysis and handling center of Huawei Qiankun completes automatic analysis and security response through threat detection, event analysis and response, and security management. Figure 2 shows the analysis procedure.
Threat Analysis and Handling
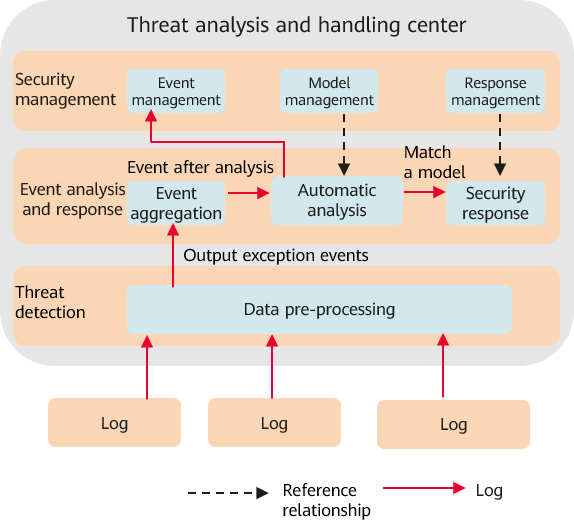
As shown in Figure 2, after obtaining service data, the threat analysis and handling center completes automatic analysis and security response through threat detection, event analysis and response, and security management.
- Threat detection: preprocesses the format and fields of the obtained logs and then outputs abnormal events.
- Event analysis and response: performs aggregation analysis, automatic analysis, and security response on output abnormal events, in that order.
Output abnormal events are aggregated and analyzed based on the corresponding aggregation policy. Then, the aggregated events are automatically analyzed and determined based on the automatic analysis model. The security response automatically responds to the events that match the analysis model. Based on automatic analysis, security experts further analyze and handle the analyzed events (including matched and unmatched events).
- Security management: provides security experts of Huawei Qiankun with visualized event portals, manual event handling capabilities, routine management capabilities, and security response management capabilities.
Security experts can check events after automatic analysis through event management, configure and adjust automatic analysis models in a timely manner through model management, and perform routine maintenance of blacklists and whitelists through response management.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot