Quick Deployment
This section describes how to quickly deploy this solution.
|
Parameter |
Type |
Mandatory |
Description |
Default Value |
|---|---|---|---|---|
|
subnet_id |
String |
Yes |
Subnet ID. This template uses an existing subnet. Select the subnet in the VPC same as the one your backend service servers belong to. For details, see 1. |
Left blank |
|
security_group_id |
String |
Yes |
Security group ID. This template uses an existing security group. You are advised to select the security group that your backend service servers belong to. For details, see 2. |
Left blank |
|
ecs_name |
String |
Yes |
Name of the ECS for deploying a WAF. The name must be unique. It can contain 1 to 54 characters and can include letters, digits, underscores (_), hyphens (-), and periods (.) |
waf_on_modsecurity_demo |
|
ecs_flavor |
String |
Yes |
WAF ECS specifications. For details, see A Summary List of x86 ECS Specifications. |
s6.medium.2 (1 vCPUs | 2GiB) |
|
ecs_image |
String |
Yes |
WAF ECS image. For more details, see IMS Public Images. |
CentOS 7.6 64bit. |
|
ecs_password |
String |
Yes |
Initial password of the WAF ECS. After an ECS is created, reset this password by referring to Step 1 in 3.3. The password can include 8 to 26 characters and must include at least three of the following character types: uppercase letters, lowercase letters, digits, and special characters ($!@%-_=+[]:./^,{}?). The password cannot include the username or the username spelled backwards. The administrator username is root. |
Left blank |
|
bandwidth_size |
Number |
Yes |
Bandwidth size. This template is billed by bandwidth. Value range: 1 to 2,000 Mbit/s. |
5 Mbit/s |
|
ip_list |
String |
Yes |
Private IP address and port for accessing your backend service servers. The format is IP address 1:Port 1,IP address 2:Port 2. For example, 192.168.0.1:8080,192.168.0.2:8081,192.168.0.3:8083. (When accessing this environment using a browser, select HTTP or HTTPS based on what the backend port uses.) |
Left blank |
|
ssl_certificate |
String |
Yes |
Name of your SSL certificate public key file, including the file name extension. After the template is deployed, upload this certificate file to the /usr/local/nginx/ssl/ directory on the WAF ECS. |
Left blank |
|
ssl_certificate_key |
String |
Yes |
Name of your SSL certificate private key file, including the file name extension. After the template is deployed, upload this certificate file to the /usr/local/nginx/ssl/ directory on the WAF ECS. |
Left blank |
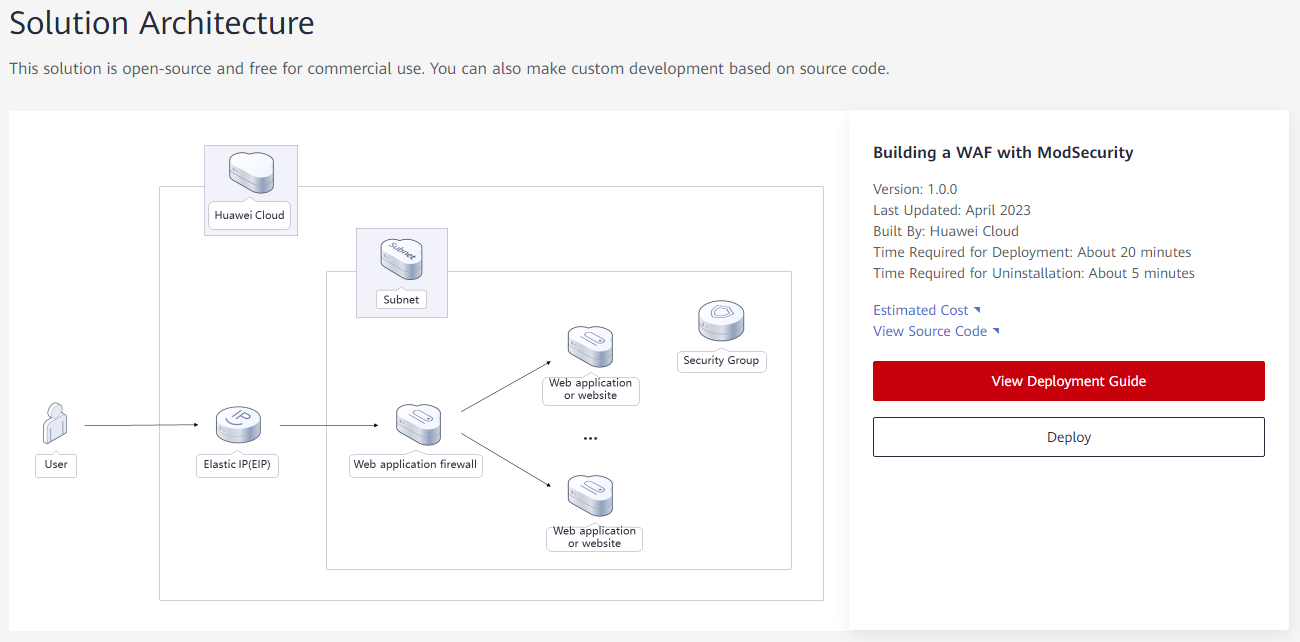
- Log in to Huawei Cloud Solution Best Practices, choose Building a WAF with ModSecurity, and click Deploy. The Create Stack page is displayed.
Figure 1 Selecting a solution
- On the Select Template page, click Next.
Figure 2 Selecting a template

- On the Configure Parameters page, configure parameters by referring to Table 1 and click Next.
Figure 3 Parameter configuration

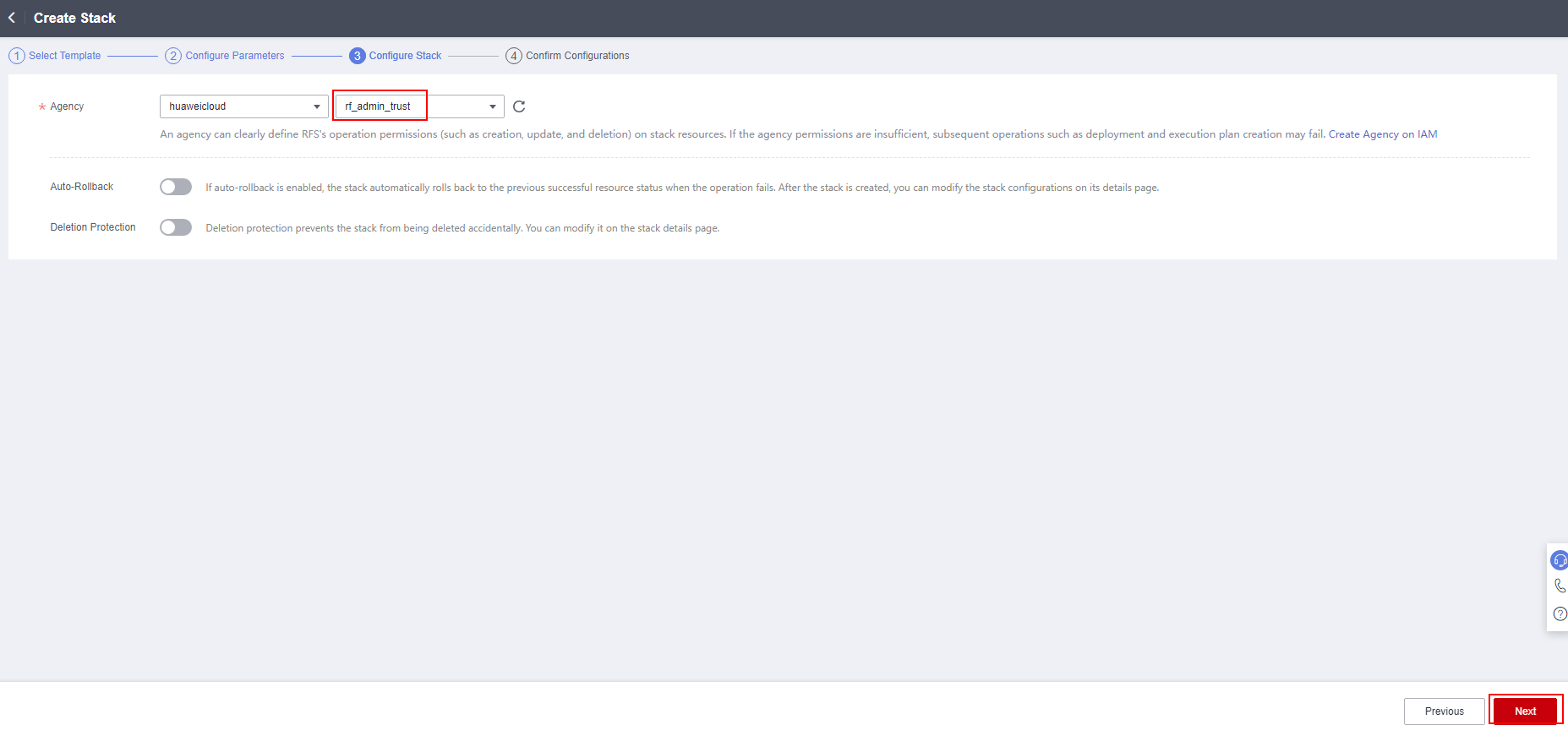
- On the displayed page, select rf_admin_trust from the Agency drop-down list and click Next.
Figure 4 Configure Stack
- On the Confirm Configurations page, click Create Execution Plan.
Figure 5 Confirm Configurations

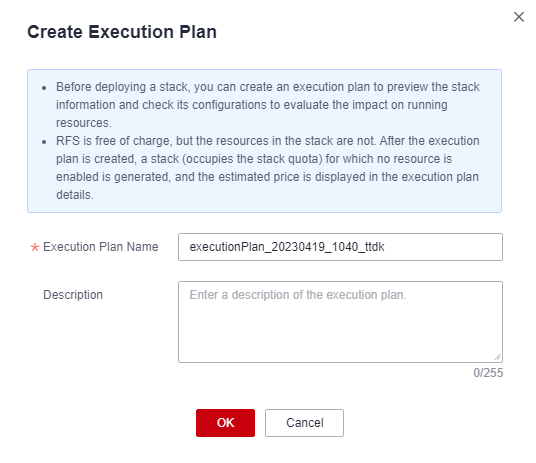
- In the displayed Create Execution Plan dialog box, enter a plan name and click OK.
Figure 6 Create Execution Plan
- Click Deploy. In the displayed dialog box, click Execute.
Figure 7 Execution Plans
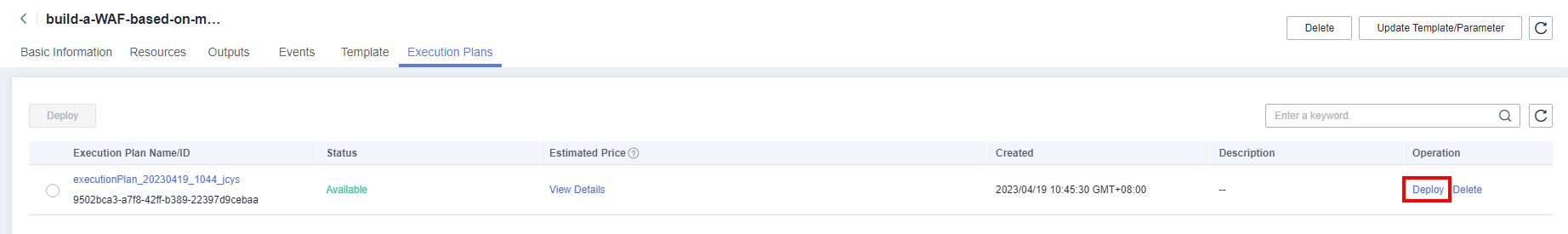 Figure 8 Execution Plan
Figure 8 Execution Plan
- Click the Events tab and check whether the solution has been deployed. If message "Apply required resource success" is displayed in the Description column, the solution has been deployed.
Figure 9 Solution deployed

- Select the Outputs tab and obtain the EIP.
Figure 10 Obtaining an EIP

Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





