Notice of the NVIDIA Container Toolkit Container Escape Vulnerabilities (CVE-2025-23266 and CVE-2025-23267)
NVIDIA Container Toolkit is an open-source toolkit from NVIDIA. It allows you to use NVIDIA GPUs to speed up computing in a containerized environment. The toolkit includes a container runtime library and utilities for automatically configuring containers to leverage NVIDIA GPUs.
Description
|
Type |
CVE-ID |
Severity |
Discovered |
|---|---|---|---|
|
Container escape |
Critical |
2025-07-17 |
|
|
Data tampering and denial of service |
High |
2025-07-17 |
Impact
In NVIDIA Container Toolkit v1.17.7 and earlier versions, an attacker can run a malicious image, which may result in container escape and enables the attacker to obtain host permissions. Successful exploitation of these vulnerabilities may cause privilege escalation, data tampering, information leakage, and denial of service.
Identification Method
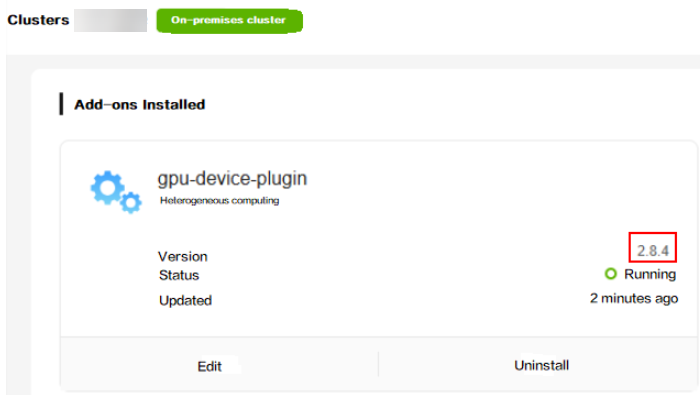
- If the UCS GPU add-on (gpu-device-plugin) is not installed in the cluster or the add-on version is 2.8.4, these vulnerabilities are not involved.
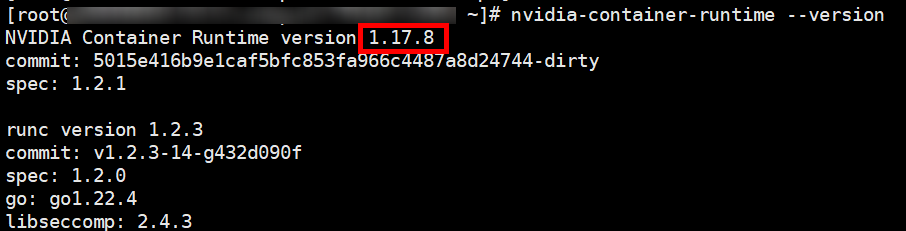
- If the version of the UCS GPU add-on (gpu-device-plugin) is earlier than 2.8.4, log in to the GPU node and run the following command:
nvidia-container-runtime --version
Solution
Do not run an untrusted container image in the cluster before the vulnerabilities are fixed.
UCS has released a new version of the add-on to fix these vulnerabilities. Upgrade the add-on to the fixed version (2.8.4).
Helpful Links
NVIDIA Container Toolkit Security Bulletin: https://nvidia.custhelp.com/app/answers/detail/a_id/5659
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot