Oracle WebLogic wls9-async Deserialization Remote Command Execution Vulnerability (CNVD-C-2019-48814)
On April 17, 2019, Huawei Cloud Emergency Response Center found that China's National Vulnerability Database (CNVD) released a security notice on Oracle WebLogic wls9-async component. It revealed that the Oracle WebLogic wls9-async component had a deserialization vulnerability. Unauthorized remote attackers can use this vulnerability to implement remote code execution and gain server permissions.
Vulnerability ID
CNVD-C-2019-48814
Vulnerability Name
Oracle WebLogic wls9-async Deserialization Remote Command Execution Vulnerability
Vulnerability Description
The WebLogic wls9-async component has a defect. The website built on the WebLogic Server has security risks. Attackers can construct HTTP requests to obtain the permission of the target server and execute arbitrary code remotely without authorization.
Affected Products
- Oracle WebLogic Server 10.X
- Oracle WebLogic Server 12.1.3
Official Solution
The patch for fixing this vulnerability has not been released.
Mitigation
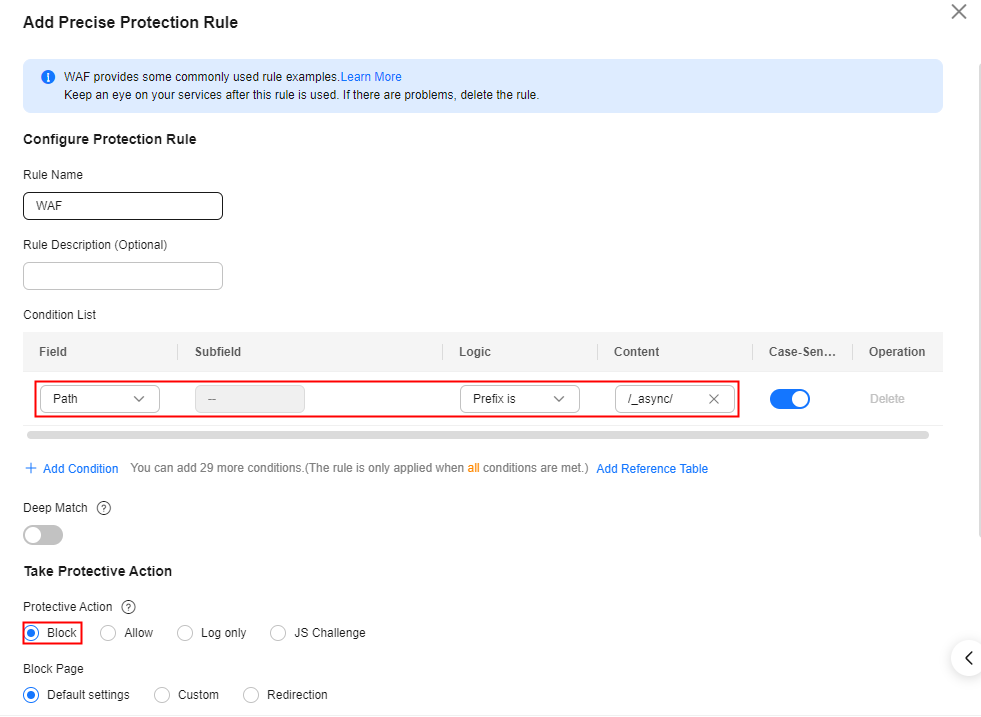
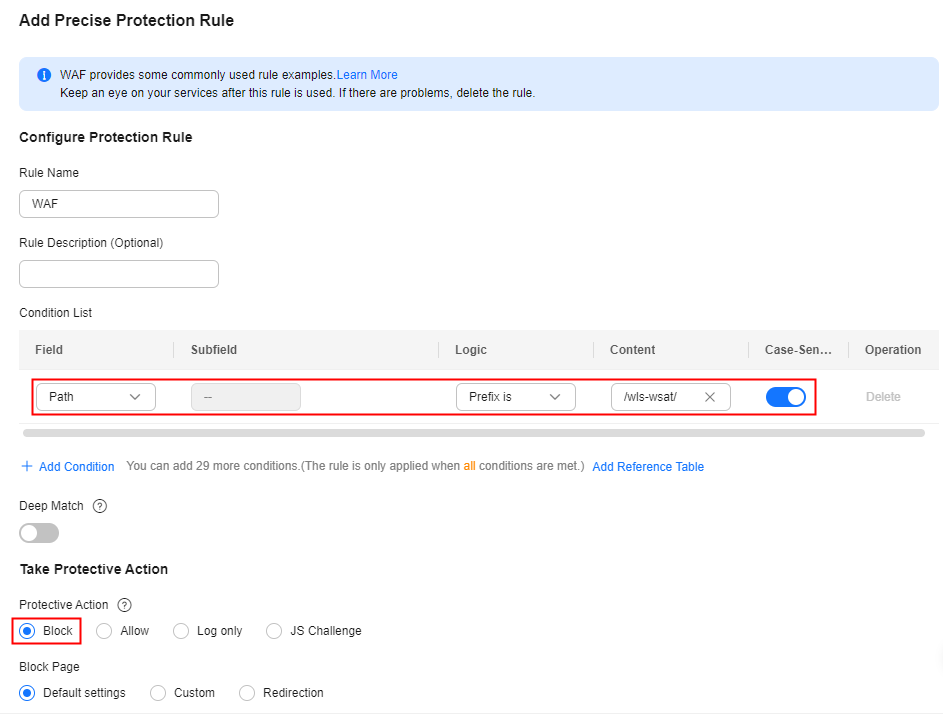
Configure precise protection rules to restrict access from the URLs whose prefixes are /_async/ or /wls-wsat/ by referring to Figure 1 and Figure 2 and block remote code execution requests initiated by exploiting this vulnerability. For details, see Configuring a Precise Protection Rule.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot