Viewing and Handling CI/CD Image Scan Results
Scenarios
To perform CI/CD image security scans, access CI/CD first. For details, see Integrating Image Security Scan in CI/CD..
After CI/CD is accessed, HSS will check image security during project building in Jenkins or CodeArts Pipeline, and display the scan results on the HSS console. It can help you identify and eliminate image security risks in a timely manner.
HSS can present image security statistics in the risk view and image view, helping you comprehensively learn, locate, and fix image risks.
- Risk view: View all the scan results of a risk, for example, a system vulnerability, application vulnerability, malicious file, unsafe setting, sensitive information risk, software compliance issue, or unsafe image building instruction.
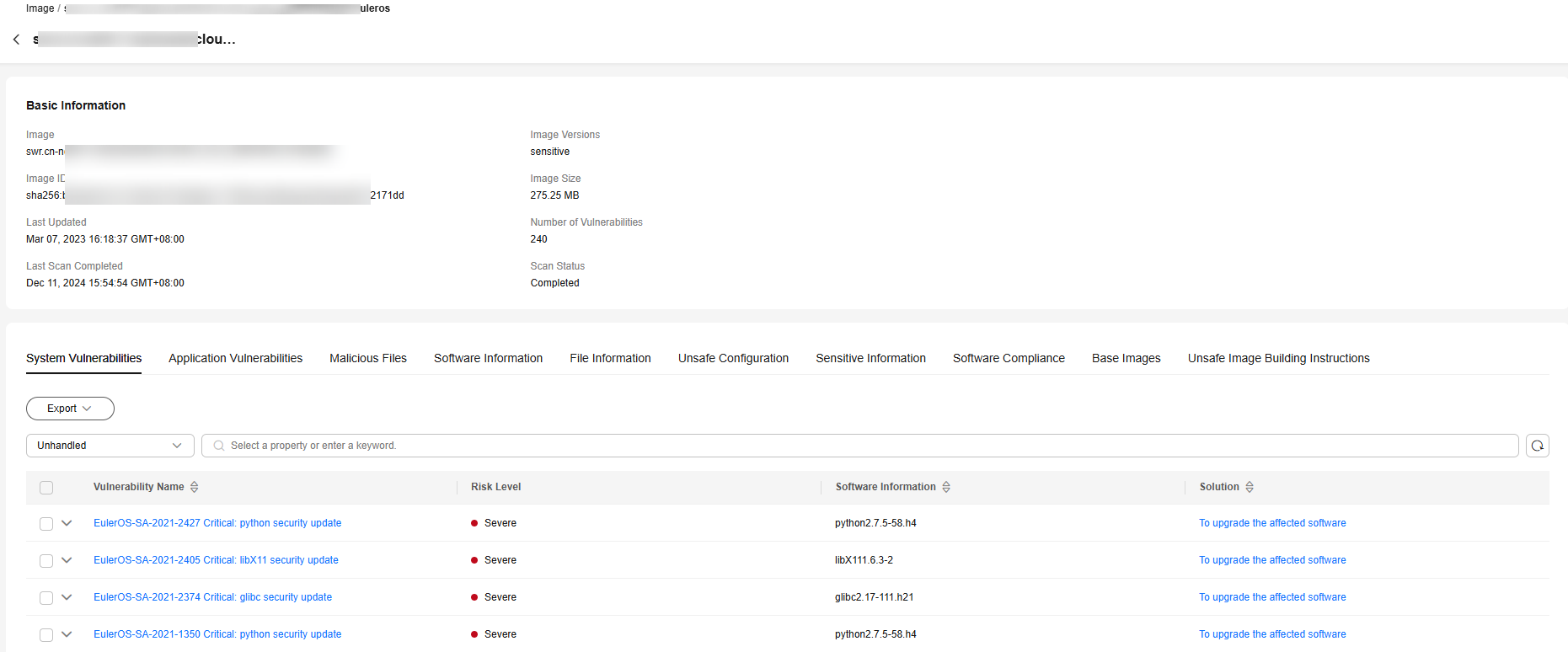
- Image view: View the scan results of an image. The results include system vulnerabilities, application vulnerabilities, malicious files, software information, file information, unsafe baseline settings, sensitive information, software compliance, base image information, and unsafe image building instruction.
Viewing and Handling CI/CD Image Scan Results in the Risk View
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Container Images.
- On the Risk View tab page, click a risk sub-tab, and select CI/CD Images from the drop-down list. Check and handle scan results. For details, see Table 1.
Image names are not displayed for some risks. You can export risk results to obtain these image names and image tags.
Figure 1 Risk view of CI/CD images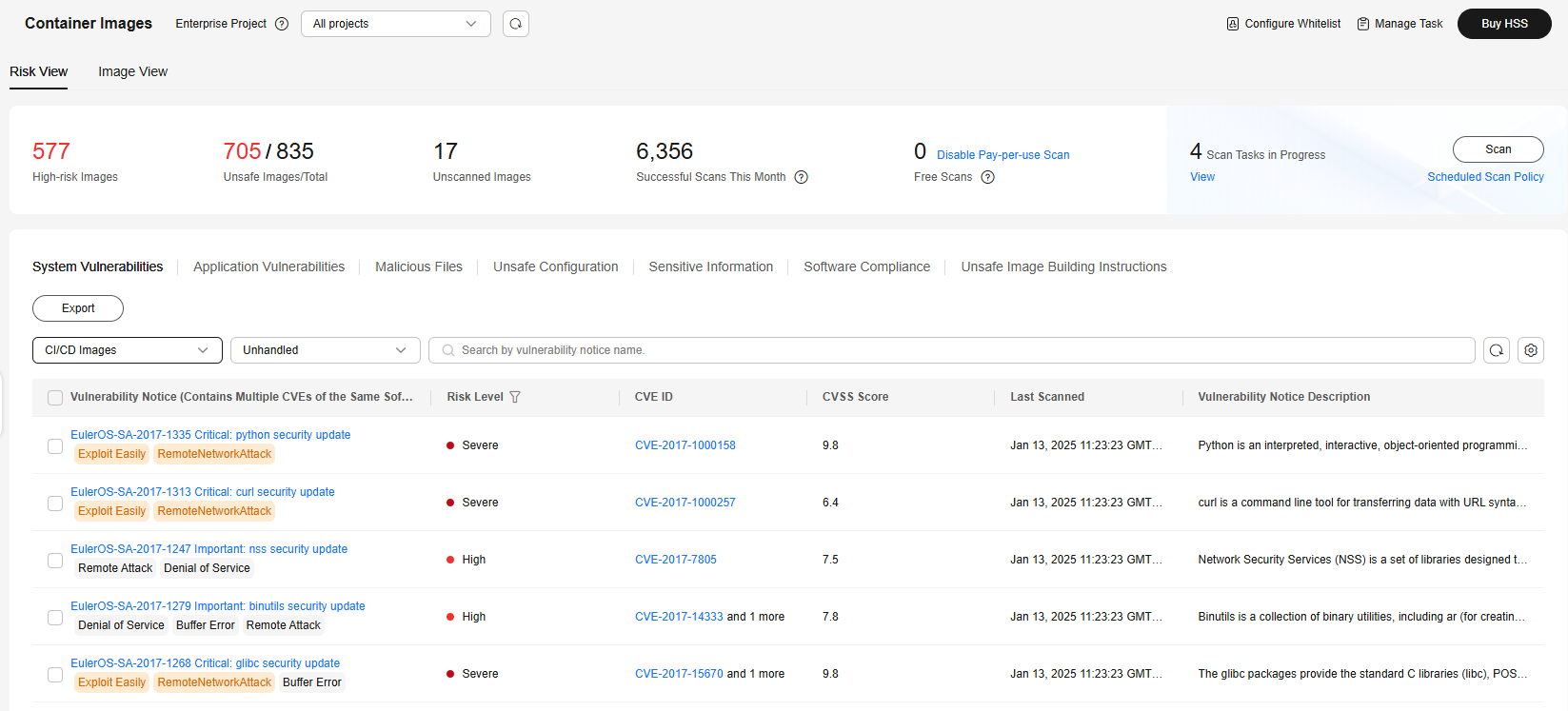
Table 1 Image scan results Risk Type
Description
System Vulnerabilities
OS vulnerability scan results.
Click a vulnerability notice name to go to the vulnerability details page. You can view the notice details, CVE details, suggestions, and affected images. You can fix the vulnerability based on the suggestions.
Application vulnerabilities
Application software vulnerability scan results.
Click a vulnerability notice name to go to the vulnerability details page. You can view the notice details, suggestions, and affected images. You can fix the vulnerability based on the suggestions.
Malicious Files
Results of malicious image file scans, including the file names, paths, file sizes, image types, affected images, and image tags.
You can locate and remove malicious files accordingly.
Unsafe Configuration
Results of image baseline checks, including unsafe settings, password complexity policy risks, and common weak password risks. You can perform operations based on the check type:
- Unsafe Settings
You can view the check items in the list. In the Operation column of a check item, click View Details. On the displayed slide-out panel on the right, you can view the audit description, suggestion, and affected images of the check item.
- Password Complexity Policy Risks
Check Affected Images and Policy Risks, and modify your password complexity policies based on Suggestion.
- Common Weak Password Risks
The scan result contains the account name, account type, masked weak password, weak password usage duration, affected image, and image tag. You can log in to the account to change its password.
To let HSS scan for user-defined weak passwords, perform the following operations:- Click Common Weak Password Detection and click Manage Weak Password.
- Configure weak passwords and click OK.
Sensitive Information
The scan result contains the risk level, file path, sensitive information, rule name (sensitive information type), affected image, and image tag.
You are advised to remove sensitive information and create an image again.
Software Compliance
The scan result contains the non-compliant software name, version, path, affected image, and image tag.
You are advised to remove non-compliant software in time.
Unsafe Image Building Instructions
The scan result of unsafe image building instructions contains the risk name, risk level, number of affected images, latest scan time, and risk description.
Click a risk name to view the risk description and affected image list. In the Operation column of an image, click Details to view the suggestions and fix the unsafe building instruction accordingly.
- Unsafe Settings
Viewing and Handling CI/CD Image Scan Results in the Image View
- Log in to the HSS console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose Risk Management > Container Images.
- Click the Image View tab.
- Click the CI/CD Images sub-tab. View CI/CD images.
- In the Operation column of an image, click View Results to go to the image details page.
- View and handle risk scan results. For details, see Table 2.
Figure 2 CI/CD image scan results
Related Operations
For details about how to add or modify the vulnerability blacklist, vulnerability whitelist, or image whitelist, see Editing the Blacklist or Whitelist of Image Scan in CI/CD.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot






