Managing kernel Options
CCE Autopilot is a serverless cluster and isolated from the kernel of physical machines. kernel tuning is a common practice in advanced service deployment scenarios. In a safe situation, CCE Autopilot allows you to configure kernel parameters through a security context of a pod based on the solution recommended by the Kubernetes community, greatly improving the flexibility of service deployment. For details of security contexts, see Configure a Security Context for a Pod or Container.
In Linux, sysctl is the most common method of modifying kernel parameters. In Kubernetes, kernel parameters are configured through the sysctl security context of the pod. If you are not familiar with the sysctl concept, see Using sysctls in a Kubernetes Cluster. A security context applies to all containers in the same pod.
CCE Autopilot allows you to modify the following non-secure sysctl parameters:
kernel.shm*, kernel.msg*, kernel.sem, fs.mqueue.*, net.*

To avoid affecting the stability of the OS, modify the sysctl parameters after understanding the consequences of the modification.
The sysctl parameters with a namespace may change in future Linux kernel versions.
Non-secure sysctl parameters are unstable. Using non-secure sysctl parameters may cause some serious problems, such as container errors. You need to take care of the risks.
In the following example, the pod's security context is used to set two sysctl parameters: kernel.msgmax and net.core.somaxconn.
apiVersion: v1
kind: Pod
metadata:
name: sysctls-context-example
spec:
securityContext:
sysctls:
- name: kernel.msgmax
value: "65536"
- name: net.core.somaxconn
value: "1024"
...
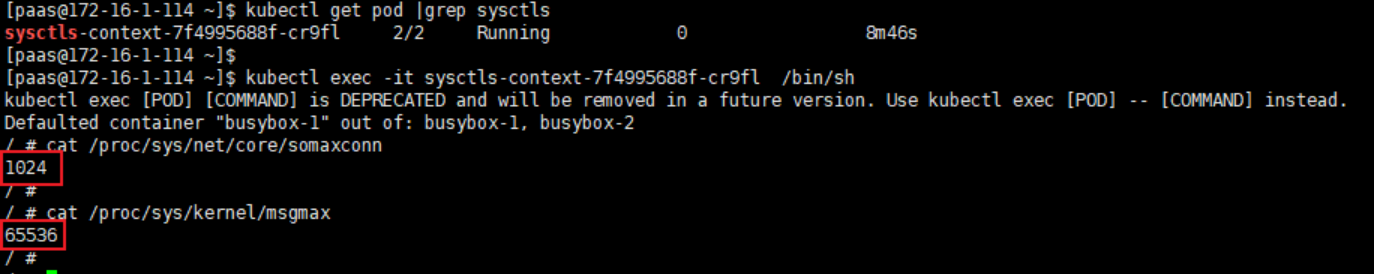
Go to the container to check whether the configuration takes effect.
kubectl exec -it podname -c container-1 -- /bin/sh
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot








