Descripción de la confiabilidad del sistema
- Servicios de cómputo
Cuando se crea un nodo en un clúster, se crea un servidor en la nube en consecuencia. El requisito previo es que CCE haya obtenido los permisos para acceder a Elastic Cloud Service (ECS) y Bare Metal Server (BMS).
- Servicios de almacenamiento
CCE permite montar el almacenamiento en nodos y contenedores de un clúster. El requisito previo es que CCE haya obtenido los permisos para acceder a servicios como Elastic Volume Service (EVS), Scalable File Service (SFS) y Object Storage Service (OBS).
- Servicios de redes
CCE permite que los contenedores de un clúster se publiquen como servicios a los que pueden acceder los sistemas externos. El requisito previo es que CCE haya obtenido los permisos para acceder a servicios como Virtual Private Cloud (VPC) y Elastic Load Balance (ELB).
- Servicios de contenedores y monitorización
CCE admite funciones como la extracción de imágenes de contenedores, la supervisión y el registro. El requisito previo es que CCE haya obtenido los permisos para acceder a servicios como SoftWare Repository for Container (SWR) y Application Operations Management (AOM).
Después de aceptar la atribución, CCE crea automáticamente una delegación en IAM para delegar otros permisos de operación de recursos en su cuenta a Huawei Cloud CCE. Para obtener más información, consulte Delegación de la cuenta.
Las agencias creadas automáticamente por CCE son las siguientes:
cce_admin_trust
La delegación cce_admin_trust tiene los permisos de Tenant Administrator. Tenant Administrator tiene los permisos en todos los servicios en la nube excepto IAM, que se utilizan para invocar a los servicios en la nube de los que depende CCE. La delegación solo tiene efecto en la región actual.
Para usar CCE en varias regiones, debe solicitar permisos de recursos en la nube en cada región. Puede ir a la consola de IAM, elegir Agencies y hacer clic en cce_admin_trust para ver los registros de delegación de cada región.
CCE puede no ejecutarse como se esperaba si el rol Tenant Administrator no está asignado. Por lo tanto, no elimine ni modifique la delegación cce_admin_trust cuando utilice CCE.
cce_cluster_agency
La delegación cce_cluster_agency contiene solo los permisos de operación de recursos de servicio en la nube requeridos por los componentes de CCE. Genera credenciales de acceso temporales utilizadas por los componentes en clústeres de CCE.
- La delegación cce_cluster_agency admite clústeres de v1.21 o posterior.
- Cuando se crea la delegación cce_cluster_agency, se crea automáticamente una política personalizada llamada CCE cluster policies. No elimine esta política.
Si los permisos de la delegación cce_cluster_agency son diferentes de los esperados por CCE, la consola muestra un mensaje indicando que los permisos han cambiado y que necesita volver a autorizar la delegación.
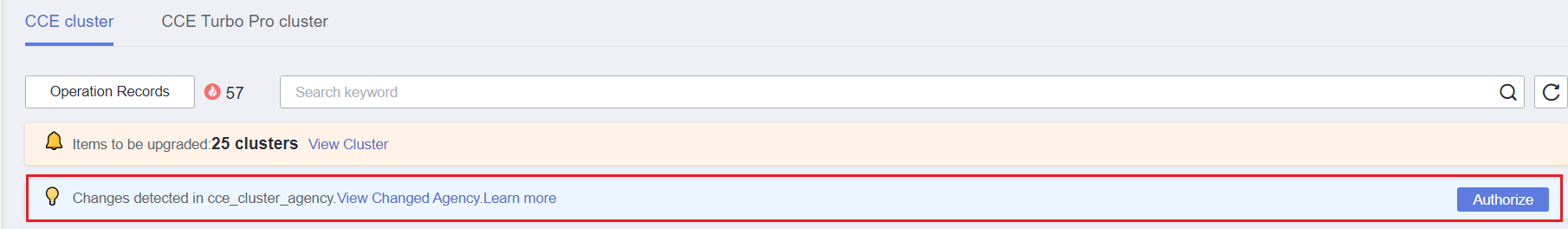
La delegación cce_cluster_agency puede ser reautorizada en los siguientes escenarios:
- Los permisos de los que dependen los componentes de CCE pueden cambiar con las versiones. Por ejemplo, si un nuevo componente depende de nuevos permisos, CCE actualizará la lista de permisos esperados y deberá conceder permisos a cce_cluster_agency de nuevo.
- Cuando modifica manualmente los permisos de la delegación cce_cluster_agency, los permisos de la delegación son diferentes de los esperados por CCE. En este caso, se muestra un mensaje, pidiéndole que vuelva a autorizar a la delegación. Si vuelve a autorizar la delegación, los permisos modificados manualmente pueden no ser válidos.






