Application Association Survey
When applications of an enterprise are migrated to the cloud, both internal and external correlations of the enterprise need to be considered. Based on internal associations, migration waves are planned, and switchover solutions are formulated. Based on external correlations, migration impact is evaluated, proper time windows are selected for shutdowns, and switchover solutions are formulated.
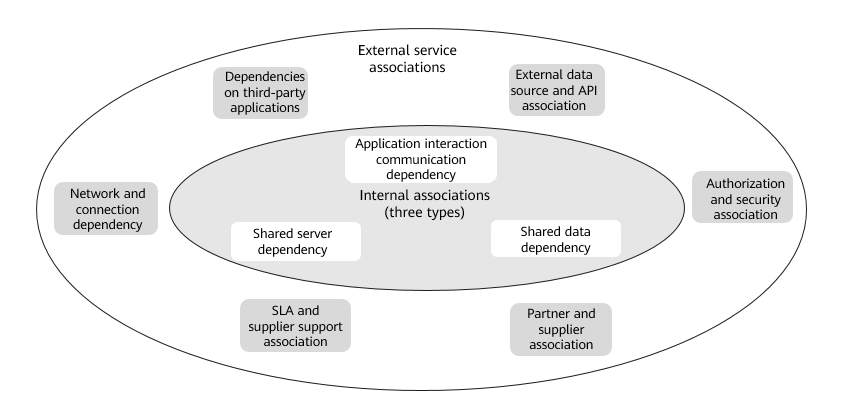
Internal Association Survey
Association analysis is an important input for batch planning and solution switchover. It is also a difficult point in cloud migration. The following figure shows the three types of associations that affect cloud migration.
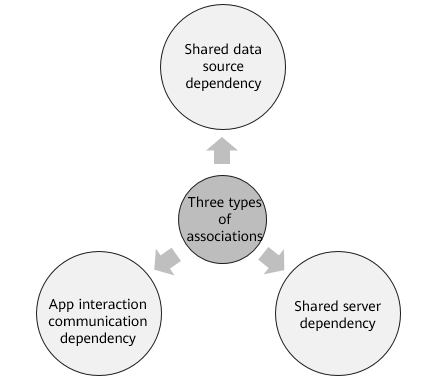
There are four association analysis methods. During cloud migration, enterprises can select a proper analysis method based on their actual conditions.
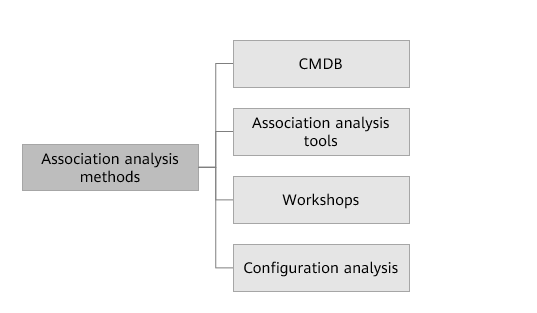
- CMDB method: This method is applicable to customers who have a CMDB system. The CMDB system usually has dependencies between applications, between applications and databases, and between applications and middleware. You can directly obtain the dependencies from the CMDB system.
Figure 4 CMDB method
 Figure 5 CMDB method example
Figure 5 CMDB method example
- Association analysis tool: You can use dedicated association analysis tools, such as Huawei Cloud Migration Center (MgC), or other association analysis tools in the industry.
Table 1 Association analysis tool method Software Name
Commercial Use
Description
Dynatrace
Yes
Dynatrace includes excellent tools for managing application performance and provides automatic application dependency mapping. It discovers and monitors microservices and applications, and even microservices and applications running in containers. It collects performance data and communication time data, and highlights poorly performing services and applications.
Cyberspace mapping
Yes
Cyberspace mapping is a tool for discovering applications and servers. It supports agentless automatic discovery on MS, Linux, Unix, cloud vendors, management programs, hardware, virtualization, and application layer. It is also applicable for remote data collection across multiple data centers.
Device42
Yes
Device42 is a discovery and mapping tool used to collect and organize data across the entire IT environment. It enables device discovery, asset management, and dedicated application mapping and management.
It can also check network devices, such as switches, load balancers, and power and environment devices, including PDUs, UPSs, and CRAC devices.
Airlync iSRG dynamic intelligent system
Yes
Airlync iSRG provides dynamic resource management for traditional networks, clouds, microservices, containers, and virtual systems. It enables resource discovery and collection, template management, resource management, and view editing.
ManageEngine Applications Manager
Yes
ManageEngine is an application manager tool. It is a monitoring tool for general-purpose servers and applications. It can monitor servers, databases, VMs, applications, web services, and other components.
Datadog
Yes
Datadog is a performance monitoring tool that provides application monitoring and mapping functions. It collects information from the entire infrastructure, including matching characteristic customers and tracing endpoints or errors. It automatically maps data flows and organizes services based on dependencies.
Pinpoint
Open-source
Pinpoint can trace transactions between distributed applications to check the overall structure and running status. Pinpoint can monitor applications in real time and understand the application topology clearly and rapidly.
- Workshops can be organized to guide key personnel who are familiar with the business system to sort out the associations.
Figure 6 Workshop method
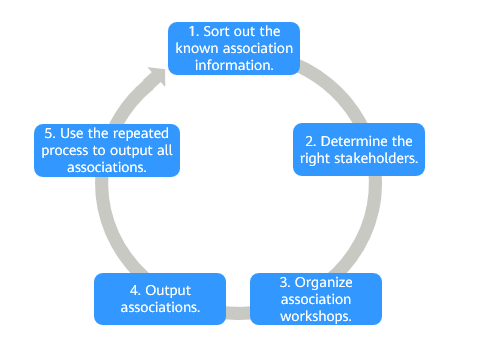
- Configuration analysis is a method that explores associations by analyzing configuration files of application systems. It helps us understand the mutual invocation relationships between applications, connections between applications and databases, and other associations. The following describes the basic procedure of the configuration analysis method:
- Collect configuration files. You need to collect and obtain configuration files related to the target application system. This may include configurations of DNS, ELB, NAT, and Nginx.conf.
- Parse configuration files: For each configuration file, you need to compile scripts or use existing tools to parse the content. The scripts can extract key information and process the information based on the file format and syntax rules.
- Extract associated information. When a configuration file is parsed, you need to identify information related to other components or resources. For example, you can search for the mutual calling relationship between applications, such as the URL or API calling from one application to another application. You can also search for the connection information between applications and databases, such as the database addresses, usernames, and passwords.
- Create an association graph. You can organize the extracted association information into a graph or an association model. The graph or model may be a directed graph, an undirected graph, or other proper data structures, and is used to represent associations and dependencies between applications.
- Analyze associations. For the association graph created earlier, we can use the graph theory algorithm or other analysis methods to explore the associations. This helps us find hidden dependencies.
By using the configuration analysis method, we can gain a deeper insight into the internal association of application systems and better understand the overall architecture and operation mode. This is of great value to system migration. It should be noted that configuration files may be subject to changes and updates, so the configuration information must be updated and verified in a timely manner to ensure its accuracy during association analysis.
External Association Survey
Before migrating applications, you need to survey and evaluate the following common external associations. Ensure that you fully understand the external dependencies of applications and take appropriate measures to ensure that external services are running properly after the migration.
- Dependencies on third-party applications
Identify third-party applications and services, including their versions and integration modes, related to the target application. Determine whether these dependencies need to be adjusted or reconfigured.
- External data source and API dependencies
Analyze and record the external data sources and APIs on which the target application depends, such as external databases, file systems, message queues, or third-party services. Ensure that these dependencies can work properly after the migration.
- Authorization and security associations
Identify the authorization and security associations related to the target application. These associations include external services and mechanisms related to identity authentication, access control, token management, and IP address whitelists.
- Partner and supplier associations
If the target application is integrated with offerings from partners or suppliers, you need to investigate associations and ensure that they can work properly after the migration.
- Service Level Agreement (SLA) and supplier support associations
Check existing SLAs and supplier support agreements and evaluate the impact of migration to the cloud platform on these associations. Ensure that the service requirements can be met and the expected support and services remain available in the cloud environment.
- Network and connection dependencies
Identify the network connections and transmission protocols required by the target application. Determine whether network configuration and access control are required after migration to ensure that the application can communicate with external systems.
The following methods can be used to survey external associations. You can use multiple methods to improve the efficiency and result integrity.
- Documents and existing materials
Read existing documents and technical materials, including the application architecture diagrams, deployment descriptions, and O&M manuals. These materials can identify key dependencies and integration points of the application.
- Communication with the development and O&M teams
Communicate with the application development and O&M teams to learn about their understanding of system dependencies. They may provide detailed information about the application, description of dependencies, and integration with other systems.
- Code analysis
Carefully check the source code of the application, especially the external dependencies involved in the configuration file and code. Some dependencies may be specified by the code.
- System scanning and monitoring
Use system monitoring tools and network scanning tools to scan the entire system and identify dependencies related to applications.
- Communication with related teams
Communicate with other departments or teams to understand the integration relationships between applications and offerings of other companies, suppliers, or partners. These relationships may include data sharing, interface invoking, and permissions control.
- Service providers and documentation
If the application relies on external service providers, review their documentation, API references, and support resources for more information about the dependencies.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





