SEC10-04 Security Incident Drill
It is a simulated activity that enables organization members to perform operations and respond to security incidents in a simulated scenario. The purpose is to test and improve their capabilities of responding to security incidents. Organizations can assess the effectiveness of their security incident response plans, identify potential problems, and make improvements to improve the team's response capabilities.
- Risk level
High
- Key strategies
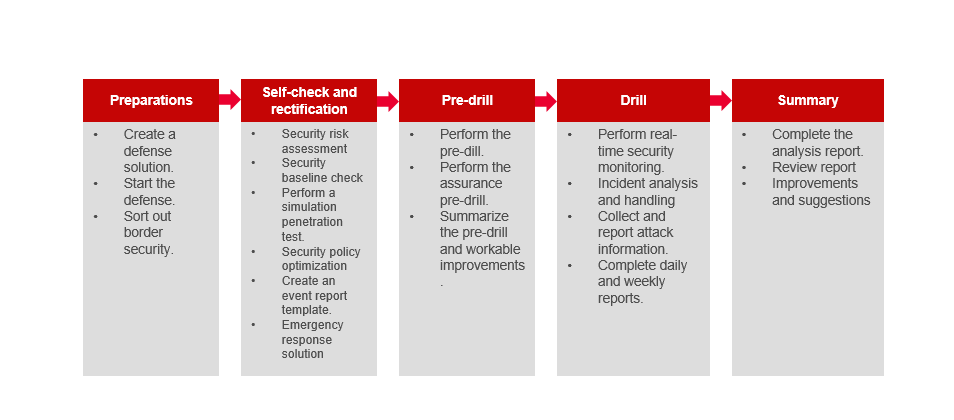
According to the security requirements of practical, systematic, and regular defense; dynamic defense, proactive defense, in-depth defense, precise defense, overall defense, and joint defense and control, practical attack-defense drills will become the norm. Promoting defense through attacks is an effective way to achieve precise defense and protection.
Event drills are used to simulate real attack scenarios. The attack chain is the same as that of actual cyber warfare, including information collection, boundary breakthrough, weapon delivery, and lateral movement. In actual attacks, weak password (simple password and repeated password) cracking, popular vulnerability exploitation, and phishing are the most frequently used.
Drills have rules, such as specifying the time, determining the target system, setting the score, and limiting the impact scope. However, there are no rules for actual attacks. So the regular security construction requirements must be higher than the specific requirements of attack-defense drills to truly improve the overall capability.
- Attack tactics analysis:
- 0-day attacks, backdoor exploitation, VPN vulnerabilities, phishing, and social engineering attacks. With the increase of attack intensity and investment of attack resources, the proportion of 0-day attacks increases, and the diversity of social engineering attacks increases. Most attacks are intranet penetration attacks, and there are few direct intrusions. The overall attack tactics are closer to real network intrusions and comply with the goal of "attack-driven prevention".
- Changes in defense points
- Single-point protection is changed to multi-point collaborative protection; large-scale blacklist interception is changed to collaborative protection; border in-depth interception is extended to intranet abnormal monitoring; passive monitoring and defense are changed to proactive deception and source tracing.
- Changes in user requirements
- Product level: In addition to traditional intrusion prevention, WAF, and vulnerability scanning, the requirements for asset mapping, APT detection, security intelligence, and honeypots is increasing.
- Service level: In addition to security hardening and attendance services during the assurance period, the requirements for routine security inspection, security training, and internal attack-defense drills are increasing.
- Attack tactics analysis:
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





