Linux Image Scan
Before releasing an image asset, perform a security scan using HSS and antivirus scan using a recommended tool, and pre-process the scan results to ensure that no high-risk vulnerability exists after the image is deployed on an ECS. If a vulnerability persists, the KooGallery operations manager will reject the request for releasing the image asset.
Perform antivirus scan for Linux images as follows.
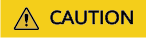
- Kaspersky offers a 30-day trial.
- Internet access is required when you download installation packages and databases. Therefore, you need to bind an EIP to the ECS.
Downloading the Scan Tool
You can use either of the following methods:
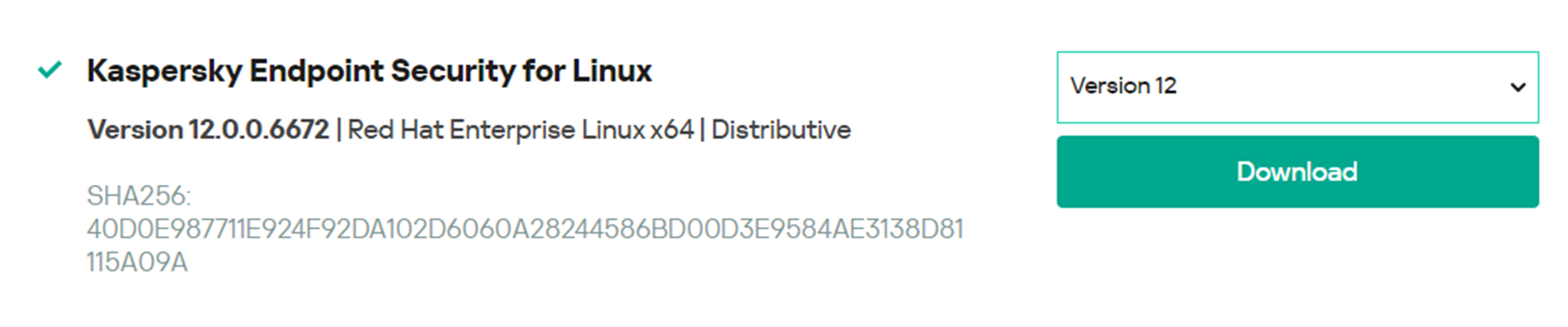
- Quick download (The version is fixed. If a new version is available, replace the link in following commands with the link of the new version.)
- CentOS, OpenEuler, and Fedora x86 architecture
wget https://products.s.kaspersky-labs.com/endpoints/keslinux10/12.0.0.6672/multilanguage-12.0.0.6672/3739343633347c44454c7c31/kesl-12.0.0-6672.x86_64.rpm
- Arm architecture
wget https://products.s.kaspersky-labs.com/endpoints/keslinux10/12.0.0.6672/multilanguage-12.0.0.6672/3739343633327c44454c7c31/kesl-12.0.0-6672.aarch64.rpm
- Ubuntu x86 architecture
wget https://products.s.kaspersky-labs.com/endpoints/keslinux10/12.0.0.6672/multilanguage-12.0.0.6672/3739343634317c44454c7c31/kesl_12.0.0-6672_amd64.deb
- CentOS, OpenEuler, and Fedora x86 architecture
- Manual download
Download the Kaspersky Endpoint Security installation package based on the OS type.
After the download is complete, run the sha256sum <Installation package file> command.
Check whether the result is consistent with the information displayed during download. If yes, start the installation.
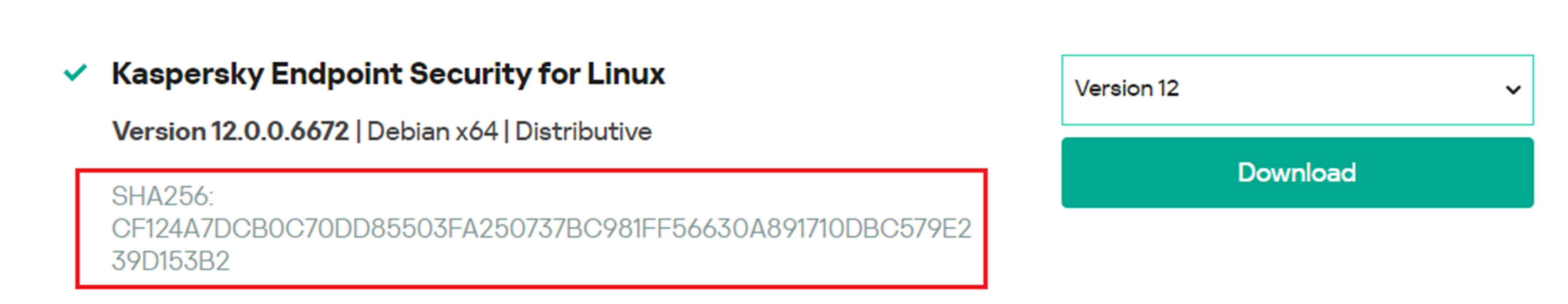
Installing the Tool
Red Hat: Run the rpm -ivh <Installation package file> command to install the RPM installation package.
Debian: Run the dpkg -i <Installation package file> command to install the DEB installation package.
Initialing the Configuration
When the following information is displayed, run the /opt/kaspersky/kesl/bin/kesl-setup.pl script.
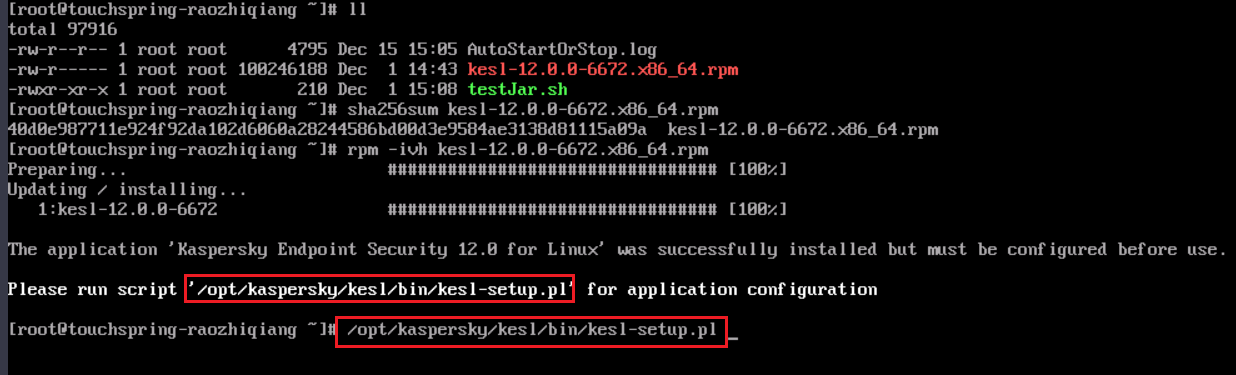
The system prompts you to initialize the configuration.
- If parameters have default values, press Enter and wait until the environment initialization is complete.
- If there are no default values, enter y and wait until the environment initialization is complete.
Scanning Files and Viewing the Result
- Perform a full scan.
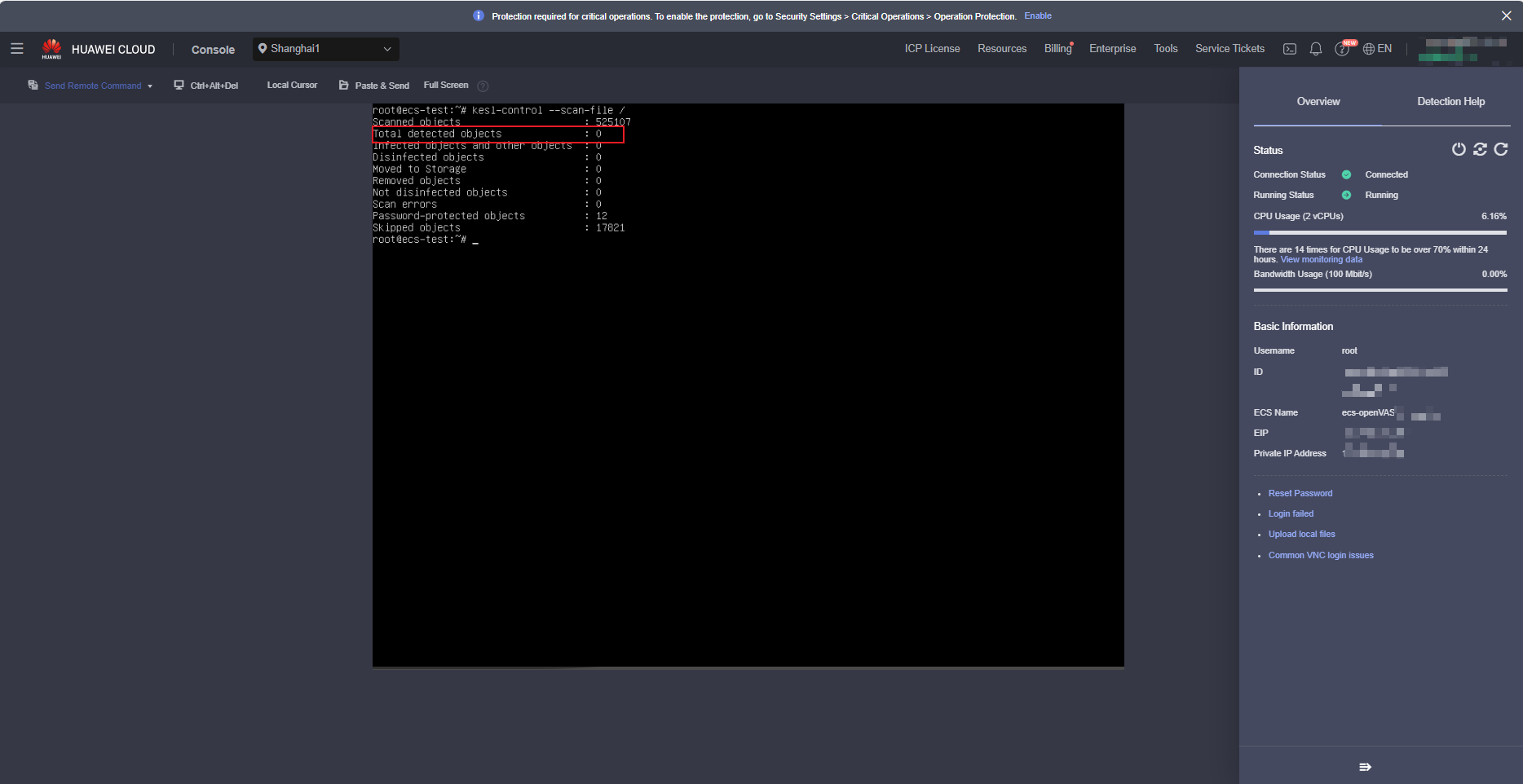
After the environment is initialized, run the kesl-control --scan-file / command.
After the scan is complete, the scan result is displayed. The following figure shows a result example (after remote login to the ECS on the ECS console).
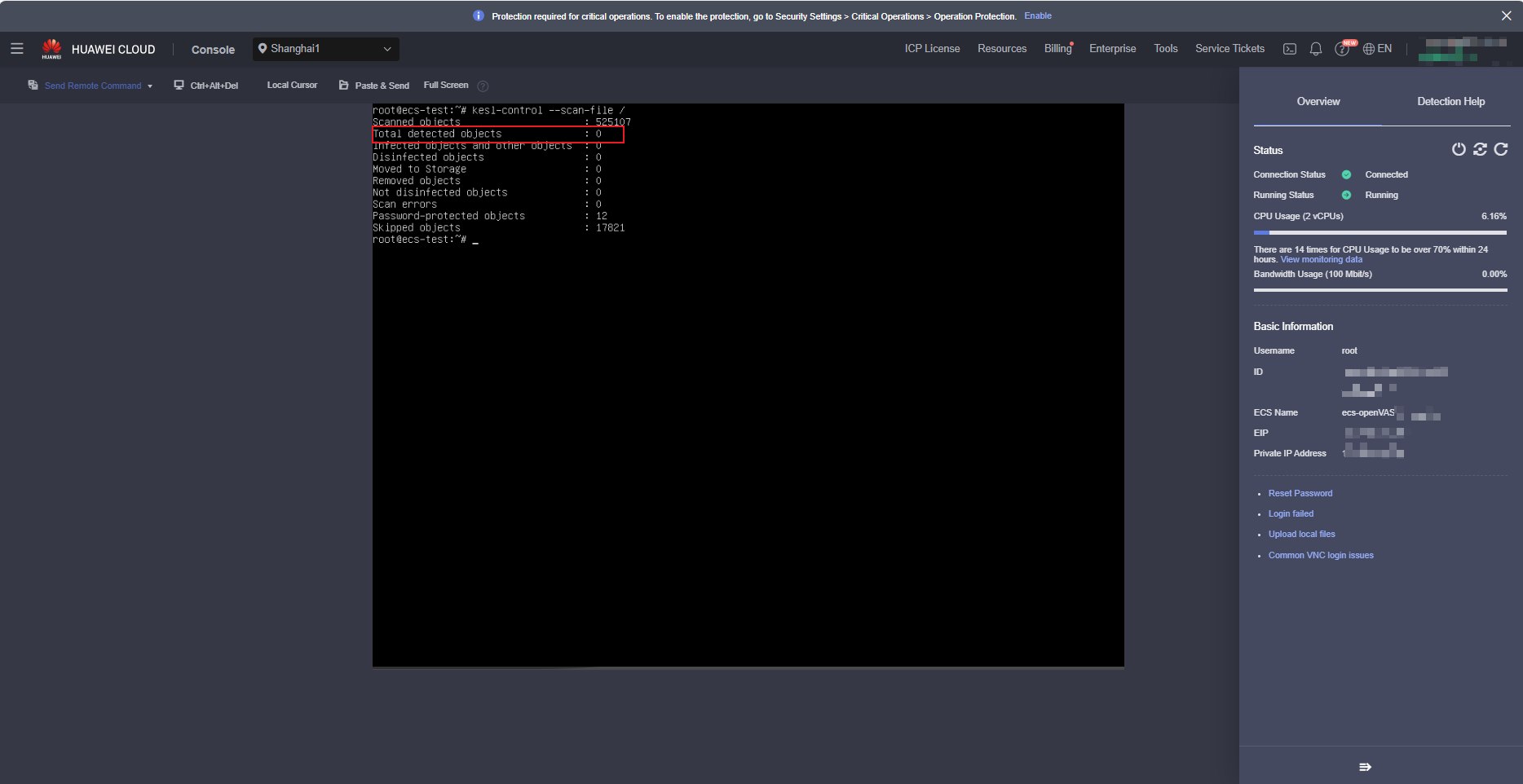
- If the value in the red box is not 0, risks exist and the risky files are moved to Quarantine.
- If the value in the red box is 0, no virus file is found. However, this does not mean that the system has no risk. After the software is installed, the system may have automatically scanned and isolated files.
Therefore, you need to check the files in Quarantine.
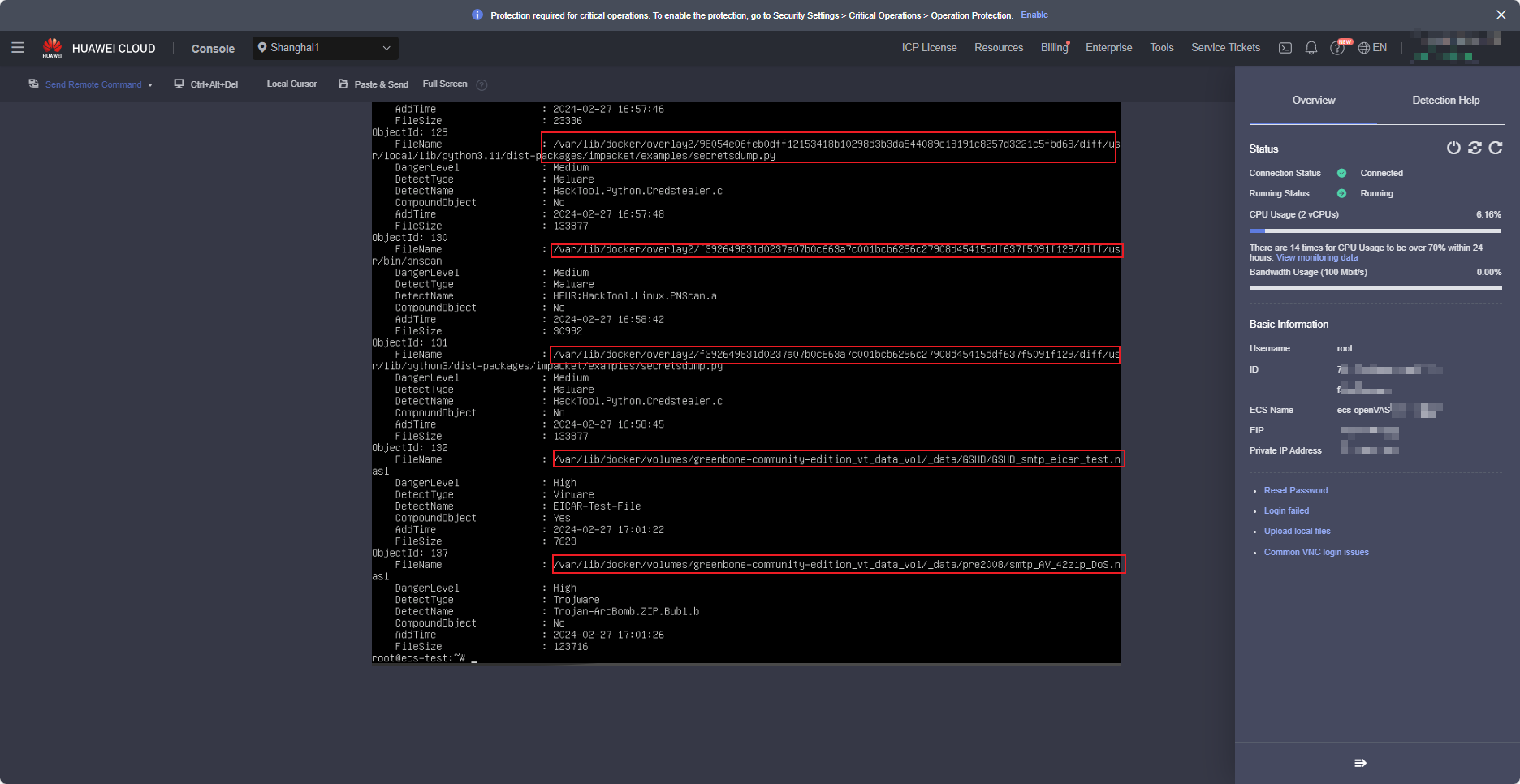
- View files in Quarantine.
Run the kesl-control -B -query command to view the files in Quarantine. The following figure is a screenshot example (after remote login to the ECS on the ECS console).
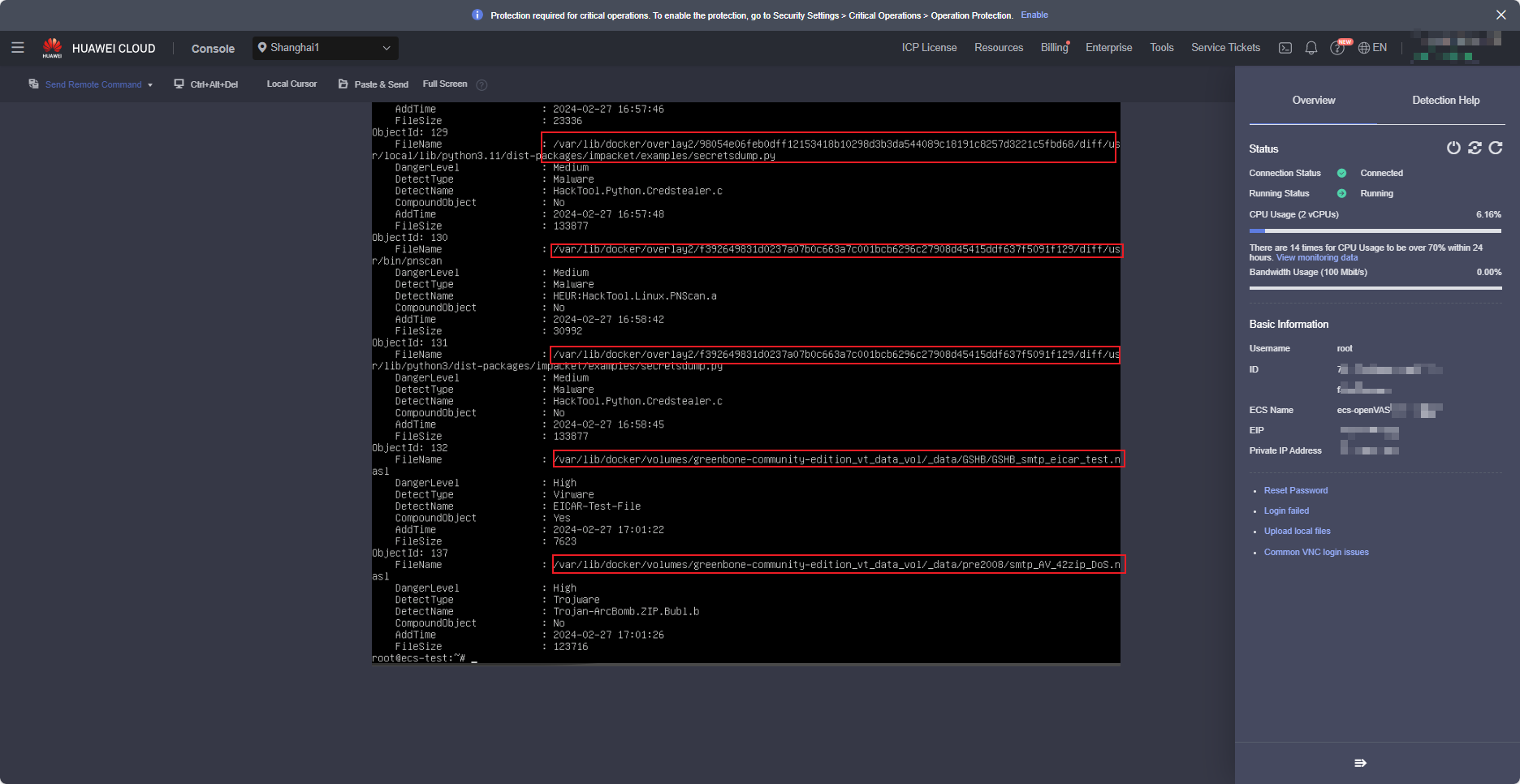
Analyze the files. Delete files that are not used by the image. If a file is used, check whether there is a false positive. Save the analysis file as a document (Format is not limited).
Providing the Scan Result
Send the seller name, image asset name, HSS scan result file, and the following materials as attachments to wujunchuan@huawei-partners.com. No mosaic processing is required for screenshots.

The server information in all screenshots must be the same.
- Screenshot of files in Quarantine after risk handling (after remote login to the ECS on the ECS console)
- Document describing false positives (if any)
Helpful Link
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot