HTTPS Certificate Requirements
The HTTPS configuration only supports certificates or private keys in PEM format. The certificate/private key upload requirements vary depending on certificate issuing agencies.
Certificates Issued by Root CA
A Certificate issued by Root CA is a complete certificate. You only need to upload the certificate when configuring HTTPS.
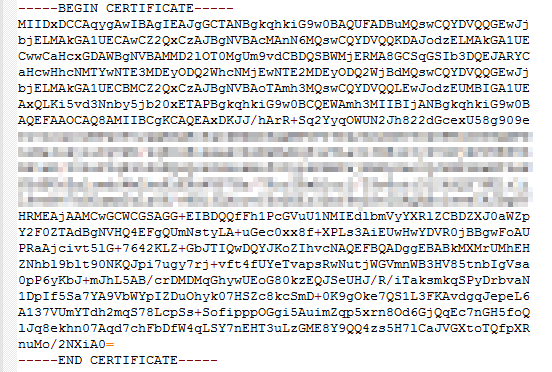
Use the text program to open the certificate in the PEM format, then you can view the certificate content, as shown in Figure 1.
A certificate in PEM format
- The certificate starts with the -----BEGIN CERTIFICATE----- chain and ends with the -----END CERTIFICATE----- chain.
- Each line of the certificate content contains 64 characters, but the number of characters in the last line can be smaller than 64.
- No space is allowed in the certificate content.
Certificates Issued by Intermediate CAs
The certificate file issued by an intermediate agency contains several certificates. You need to combine the certificates into an integral one, and upload it when configuring HTTPS security acceleration. A combined certificate is shown as Figure 2.
RSA Private Key
PEM files can contain certificates or private keys. If a PEM file contains only private keys, the file suffix may be replaced by KEY.
Use the text program to open the private key file in the PEM or KEY format, then you can view the private key content, as shown in Figure 3.
Content of an RSA private key:
- The private key starts with the -----BEGIN RSA PRIVATE KEY----- chain and ends with the -----END RSA PRIVATE KEY----- chain.
- Each line of the private key content contains 64 characters, but the number of characters in the last line can be smaller than 64.
- No space is allowed in the private key content.
If the certificate chain of a private key file contains the following information: -----BEGIN PRIVATE KEY----- and -----END PRIVATE KEY-----, or -----BEGIN ENCRYPTED PRIVATE KEY----- and -----END ENCRYPTED PRIVATE KEY-----, you need to use the OpenSSL tool to run the following command to convert the format.
openssl rsa -in old_key.pem -out new_key.pem
Format Conversion
The HTTPS configuration only supports certificates or private keys in PEM format. It is recommended that OpenSSL be used to convert certificates in other formats into the PEM format. The following examples illustrate some popular converting methods.
In the following examples, the name of certificates before conversion is old_certificate by default, and that of private keys before transformation is old_key by default. The new certificate and private key names are new_certificate and new_key respectively.
- Converting DER to PEM
openssl x509 -inform der -in old_certificate.cer -out new_certificate.pem openssl rsa -inform DER -outform pem -in old_key.der -out new_key.pem
- Converting P7B to PEM
openssl pkcs7 -print_certs -in old_certificate.p7b -out new_certificate.cer
- Converting PFX to PEM
openssl pkcs12 -in old_certificat.pfx -nokeys -out new_certificate.pem openssl pkcs12 -in old_certificat.pfx -nocerts -out new_key.pem
To convert a PKCS8 private key to a PKCS1 one, run the following command:
openssl rsa -in old_certificat.pem -out pkcs1.pem
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot