Disabling the Sub-account Permission to Read Keys for Key Protection
When you use many accounts to manage the CAE environment, you can create sub-accounts under your cloud service account for employees in different departments based on your organization structure and set different access permissions for these sub-accounts to isolate user permissions.
For example, you can create a development account and a test account for development and test personnel respectively. Because test personnel do not need to be aware of sensitive information, you can disable the permission of the test account to obtain sensitive information.
This practice describes how to disable all DEW permissions and CAE remote login permission of a sub-account so that the sub-user cannot read keys.
Creating a Custom Policy
- Log in to IAM.
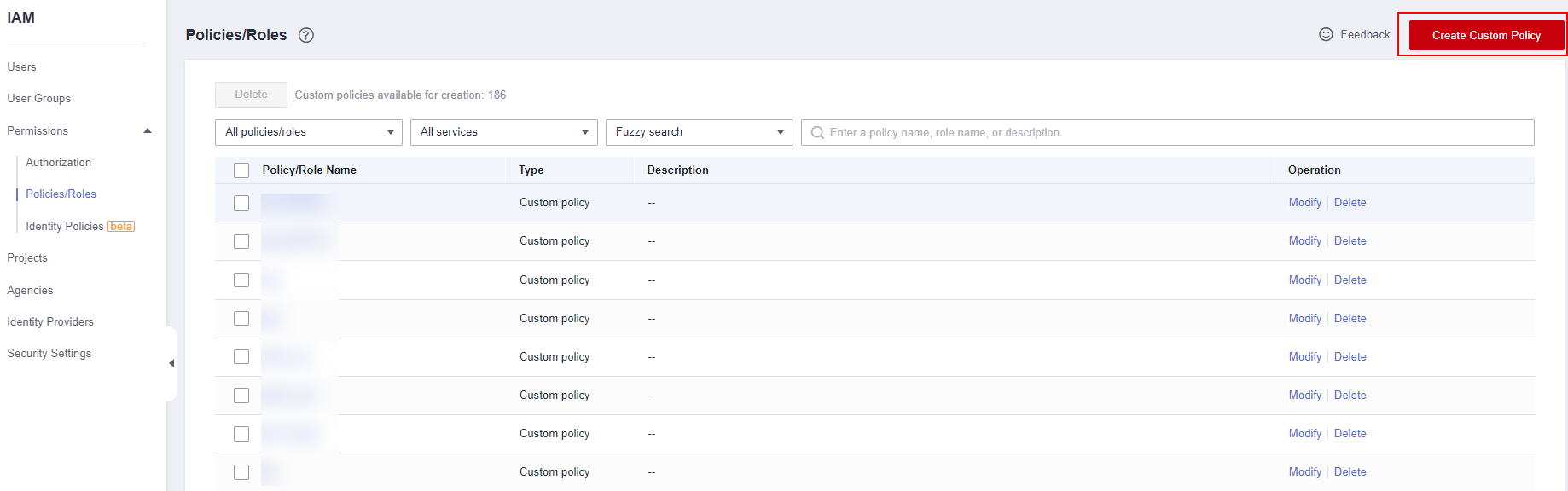
- Choose Permissions > Policies/Roles.
- Click Create Custom Policy in the upper right corner.
Figure 1 IAM console
- Configure a custom policy.
- Policy Name: Enter cae-subuser.
- Policy Content: Select Deny.
- Select service: Select Cloud Application Engine.
- Select Action: Select cae:application:createConsole.
Figure 2 Creating a custom policy
- Click OK.
Creating a User Group and Assigning Permissions
- Choose User Groups and click Create User Group.
Figure 3 Creating a user group

- Enter a user group name, for example, cae-test, and click OK.
- In the user group list, click cae-test.
- On the Permissions tab, click Authorization and select the custom policy created in Creating a Custom Policy.
Figure 4 Authorizing a custom policy

- Click Next and set Scope to All resources.
- Click OK.
Click Finish to go back to the User Groups page.Figure 5 User group authorized

- Click the Users tab.
- In the user list, select the sub-user whose permissions need to be configured and click OK.
Figure 6 Configuring user management

Verifying Sub-user Permissions
- Log in to CAE as the sub-user in 8.
- Perform operations such as Adding a Secret and Configuring an Environment Variable. The operations are normal.
- Choose Instance List.
- Select the target instance and click Remote Login in the Operation column. The secret details cannot be viewed.
Figure 7 No remote login permission

- Click
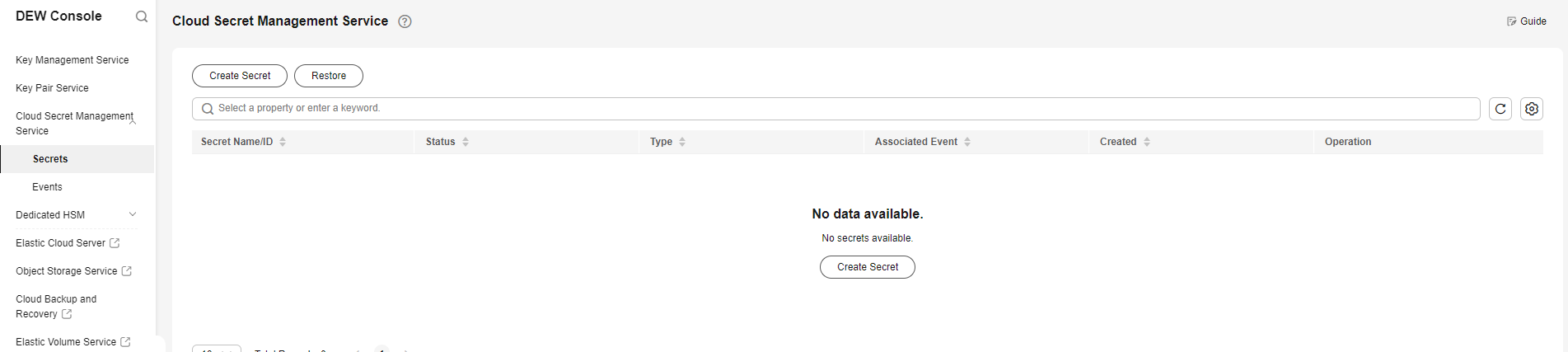
 in the upper left corner. In the service list, choose Data Encryption Workshop to go to the DEW console.
in the upper left corner. In the service list, choose Data Encryption Workshop to go to the DEW console. - Choose Cloud Secret Management Service > Secrets. The secret details cannot be viewed.
Figure 8 No DEW agency permission
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





