URL Validation
Referer validation can filter visitors' identities. However, the referer content can be forged, which cannot completely protect your VOD resources. Therefore, VOD provides URL validation. You can configure the key and generate the corresponding playback URL. The URL has a certain validity period, which effectively prevents VOD resources from being illegally stolen.
Implementation
Referer validation works in a simple way. After a blacklist or whitelist is configured on the VOD console, VOD distributes the blacklist or whitelist to CDN. When receiving a request, CDN checks whether the request is valid based on the list. If the request is valid, CDN accesses the requested resource. If the request is invalid, CDN rejects the request and returns a status code 403.
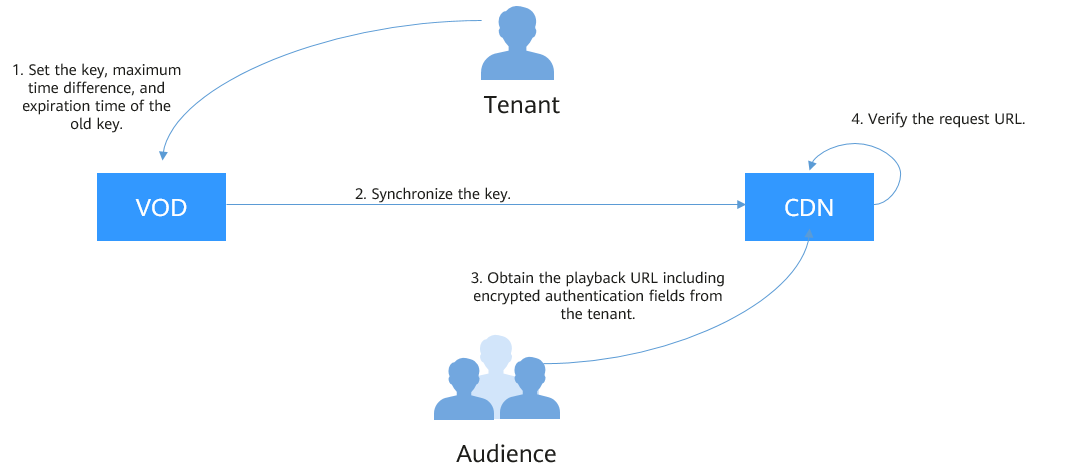
URL validation is implemented by VOD edge nodes and origin server in VOD. It is a more secure and reliable anti-piracy solution than referer validation. Figure 1 shows how URL validation works.
The process is as follows:
- You enable URL validation on the VOD console and configure the allowed time difference and algorithm.
- VOD delivers the configured key value to CDN nodes.
- You obtain the authentication URL of a VOD media file.
- Viewers request CDN to play a video through the authentication playback URL.
- CDN verifies the request based on authentication information carried in the playback URL. Only requests that pass the verification are allowed.
Notes
- This function is optional and is disabled by default.
- After this function is enabled, the original URLs cannot be used. New signed URLs must be generated based on rules.
- If the signed URL expires or the signature fails to be authenticated, the video fails to be played and the message "403 Forbidden" is returned.
- Algorithms A, B, and C do not support HLS and DASH playback scenarios.
- To disable URL validation, submit a service ticket.
- When URL validation is enabled, playback with multiple audio tracks and multilingual subtitles is not supported.
Procedure
- Log in to the VOD console.
- In the navigation pane, choose Domain Name Management.
- Click Configure on the right of the domain name and choose the Hotlink Protection Settings tab.
- Click URL Validation. The URL Validation dialog box is displayed.
- Configure URL validation parameters. Table 1 describes the parameters.
Figure 2 Configuring URL validation
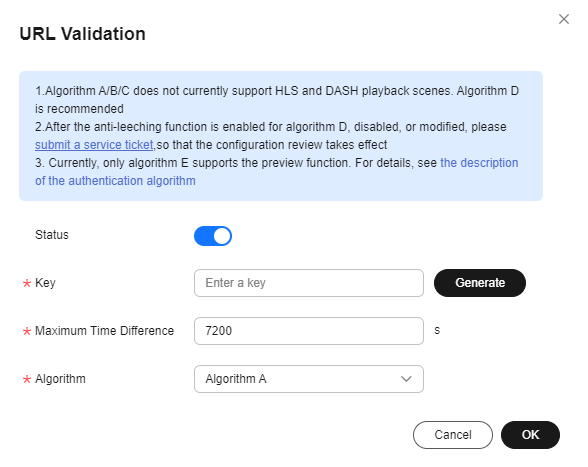
Table 1 Parameters Parameter
Description
Key
Click Generate to generate a key value.
Maximum Time Difference
How long a signed URL remains valid. The default value is 120 minutes.
For example, if the signed URL generation time is 1573806090 (Nov. 15, 2019 16:21:30 GMT+08:00) and the allowed time difference is 120 minutes, the signed URL expires at Nov. 15, 2019 18:21:30 GMT+08:00.
Expiration Time of the Old Key
By default, the old key expires 60 minutes later since the new key takes effect.
For example, if the new key takes effect on Nov. 15, 2019 16:21:30 GMT+08:00 and Expiration Time of the Old Key is 60 minutes, the old signed URL expires at Nov. 15, 2019 17:21:30 GMT+08:00.
Algorithm
Key encryption algorithm. The following algorithms are supported:
Algorithms A, B, and C: The MD5 digest algorithm is used. For details, see Encryption Algorithm A, Encryption Algorithm B, and Encryption Algorithm C.
Algorithm D: The symmetric encryption algorithm is used. For details, see Encryption Algorithm D.
Algorithm E: The SHA-256 algorithm is used. For details, see Encryption Algorithm E (same as the Signing Method C2 of CDN). Algorithm E is now displayed on the GUI but not available for your use.
NOTE:- Algorithms A, B, and C do not support HLS and DASH playback. Algorithm D or E is recommended.
- Currently, algorithm E supports preview only for HLS and MP4 files. The preview function of MP4 files takes effect only when MOOV is in front of MDAT. After the preview function is enabled, the playback URL can be obtained from the VOD console. The default preview duration is 300s.
Authentication Scope
Specifies the files to be authenticated. Currently, you can authenticate all files, authenticate files with a specified file name extension, or choose not to authenticate files with a specified file name extension.
Authentication Inherit Config
Adds the authentication parameter to TS and MP4 files under M3U8/MPD index files, so that the files can be played after authentication succeeds.
NOTE:- If there are multi-layer M3U8/MPD files, only the first-layer M3U8/MPD files are parsed, and the TS/MP4 streams of M3U8/MPD files at other layers are not expanded.
- The standard M3U8 format is supported. M3U8 files are parsed by line. If the parsing fails, responses from the origin server are returned to users. URIs starting with the #EXT-X-MAP tag and URLs/URIs not starting with the pound key (#) are supported.
- The standard MPD format is supported. MPD files are parsed by line. If the parsing fails, responses from the origin server are returned to users. The URI between tags <BaseURL> and </BaseURL> is identified. The SegmentTemplate tag is not supported.
Preview
Only HLS and MP4 files can be previewed.
- Click OK.
- If you select algorithm D, you need to submit a service ticket for approval after configuring the parameters. The submitted information must contain the configured domain name and information listed in Table 1.
URL validation settings take effect once your request is approved. If you modify the URL validation settings, you also need to submit a service ticket for approval.
- Verify whether the URL validation settings have taken effect.
Obtain the signed streaming URL and play the content via the URL. If the playback is successful, the URL validation settings have taken effect.
Generating a Signed URL
From the console
- Log in to the VOD console.
- In the navigation pane, choose Management > Audio and Video Management.
- Click Details in the row containing your media file and then choose the Playback tab.
URL is the original streaming URL of the media file. Click
 to obtain the signed URL.Figure 3 Streaming URL
to obtain the signed URL.Figure 3 Streaming URL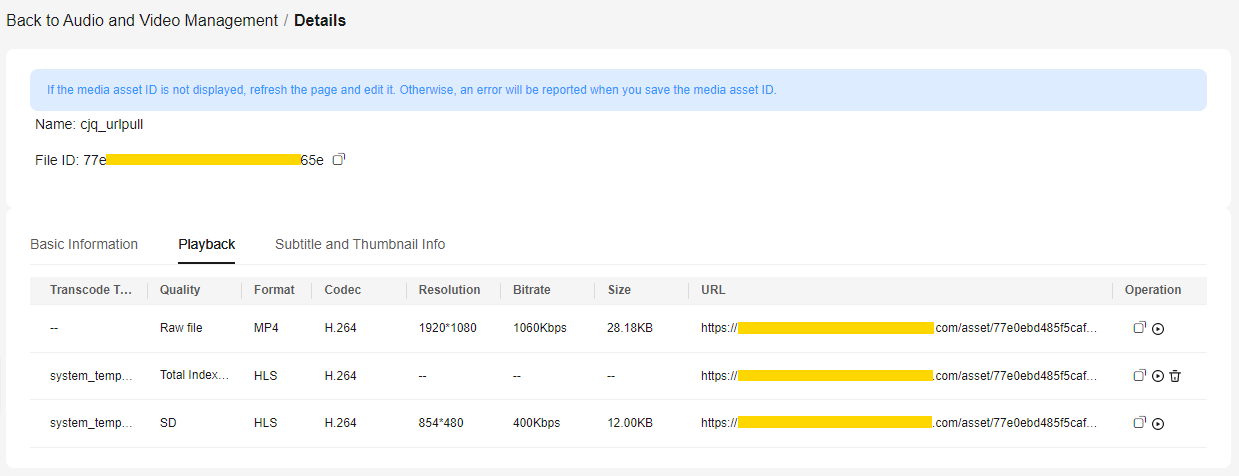
Encryption Algorithm A
Signed URL format
Original URL?auth_key={timestamp}-{rand}-{uid}-{auth_key}
auth_key = MD5(/asset/{assetId}/{file_name}-{timestamp}-{rand}-{uid}-{private_key})
|
Field |
Description |
|---|---|
|
timestamp |
Time when a signed URL is generated. The value is a Unix timestamp, which is the number of seconds since January 1, 1970. Example: 1564731935 (2019.08.02 15:45) |
|
rand |
Random number. The recommended value is a UUID, which cannot contain hyphens (-). Example: f03cbe7c4a3849bc8d8769e3110e4533 |
|
uid |
This parameter is not used now. Set it to 0. |
|
private_key |
Key value set on the console. For details, see Procedure. |
Original URL: http://1.cdn.myhuaweicloud.com/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4 private_key: myPrivateKey timestamp: 1547123166 rand: 477b3bbc253f467b8def6711128c7bec uid: 0
auth_key = md5(/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4-1547123166-477b3bbc253f467b8def6711128c7bec-0-myPrivateKey) = 584883719a3f722bf1a32a3b0a4d25dd
Signed URL based on algorithm A
http://1.cdn.myhuaweicloud.com/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4?auth_key=1547123166-477b3bbc253f467b8def6711128c7bec-0-584883719a3f722bf1a32a3b0a4d25dd
Encryption Algorithm B
https://{cdn_domain}/{date_YYYYmmddHHMM}/{md5sum}/asset/{asset_id}/{file_name}
md5sum = md5({private_key}{date_yyyyMMddHHmm}/asset/{asset_id}/{file_name})
|
Field |
Description |
|---|---|
|
date_yyyyMMddHHmm |
Time when a signed URL is generated. The format is yyyyMMddHHmm. Example: 201908051445 |
|
file_name |
Part starting behind the media asset ID of the original streaming URL to the end of the URL. Example: play_video/test.mp4 |
|
private_key |
Key value set on the console. For details, see Procedure. |
Original URL: http://1.cdn.myhuaweicloud.com/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4 private_key: myPrivateKey date_yyyyMMddHHmm: 201901102026 file_name: test.mp4
Obtain md5sum based on the calculation formula.
md5sum = md5(myPrivateKey201901102026/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4) = 713ef643de8df076da6ec3c0545968cb
Signed URL based on algorithm B
http://1.cdn.myhuaweicloud.com/201901102026/713ef643de8df076da6ec3c0545968cb/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4
Encryption Algorithm C
https://{cdn_domain}/{md5hash}/{time_hex}/asset/{asset_id}/{file_name}
md5hash = md5({private_key}/asset/{asset_id}/{file_name}{time_hex})
|
Field |
Description |
|---|---|
|
file_name |
Part starting behind the media asset ID of the original streaming URL to the end of the URL. Example: play_video/test.mp4 |
|
time_hex |
Time when a signed URL is generated. The value is a hexadecimal Unix timestamp. Example: hex(1564987530)=5D47D08A |
|
private_key |
Key value set on the console. For details, see Procedure. |
Original URL: http://1.cdn.myhuaweicloud.com/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4 private_key: myPrivateKey time_hex: hex(timestamp) = hex(1547123166) = 5C3739DE file_name: test.mp4
md5hash=md5(myPrivateKey/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp45C3739DE) = afa20c956043fe6d130b16f2704ac870
Signed URL based on algorithm C
http://1.cdn.myhuaweicloud.com/afa20c956043fe6d130b16f2704ac870/5C3739DE/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.mp4
Encryption Algorithm D
Signed URL format
Original URL?auth_info={Encrypted string}.{EncodedIV}&plive={plive_starttime}
- Original encrypted string = url_encoding({path}+"$"+{Timestamp})+"$"+{plive_starttime}
- Encrypted string = aes_cbc_128_pkcs5padding(Original encrypted string,key,IV)
- EncodedIV = hex(IV)
|
Field |
Description |
|---|---|
|
path |
Directory from the domain name to the last level, including the slash (/) behind the domain name and slash (/) behind the last level of directory, excluding the file name Example: /asset/32237c8f68fcc6071a2d8e3421eee20d/play_video/ |
|
Timestamp |
Time when a signed URL is generated. The value is UTC time in yyyyMMddHHmmss format. Example: 20190805101025 |
|
key |
Key value set on the console. For details, see Procedure. |
|
(Optional) plive |
Start time of pseudo-streaming, in UTC time. Specify this parameter only for Pseudo-Streaming. In other cases, this parameter is not required for calculating the signed URL. |
|
IV |
Randomly generated byte array. It can be up to 16 characters long. hex(): converts the byte array into a hexadecimal string.
Sample code for generating IV is:
byte[] iv = new byte[16]; SecureRandom secureRand = new SecureRandom(); secureRand.nextBytes(iv); |
Original URL: https://179.cdn-vod.huaweicloud.com/asset/32237c8f68fcc6071a2d8e3421eee20d/play_video/index.m3u8 path: /asset/32237c8f68fcc6071a2d8e3421eee20d/play_video/ key: 8Ks1qn14XRO28qOa Timestamp: 20190805102430 plive: 1704074400
Original encrypted string = url_encoding("/asset/32237c8f68fcc6071a2d8e3421eee20d/play_video/") + "$" + "20190805102430"+ "$" + "1704074400"
Encrypted string = aes_cbc_128_pkcs5padding(Original encrypted string,key,IV) = 34M%2F6KtYgxuAozdBLIVTe0dUVAZdvXsYQoYAnDmuhRHh1hshYg%2B2Tl0AmSwySDh%2BmkER44qYKpSP%2BgfsLM%2FIZe4F6K4n1Nx6ouGwyKfqdDA%3D
EncodedIV = hex(IV) = 79436d453636364e335941713330534e
https://179.cdn-vod.huaweicloud.com/asset/32237c8f68fcc6071a2d8e3421eee20d/play_video/index.m3u8?auth_info=34M%2F6KtYgxuAozdBLIVTe0dUVAZdvXsYQoYAnDmuhRHh1hshYg%2B2Tl0AmSwySDh%2BmkER44qYKpSP%2BgfsLM%2FIZe4F6K4n1Nx6ouGwyKfqdDA%3D.79436d453636364e335941713330534e&plive=1704074400
Encryption Algorithm E

- Algorithm E is now displayed on the GUI but not available for your use.
- The preview and pseudo-streaming functions cannot be enabled at the same time. The following URLs are for reference only. exper and plive cannot exist at the same time.
Signed URL format
Original URL?auth_key={authKey}×tamp={timestamp}&exper={exper}&plive={plive_starttime}
Formula for calculating authKey:
- To enable preview: auth_key = sha256({PrivateKey}{fileName}{timestamp}{exper}
- To enable pseudo-streaming: auth_key = sha256({PrivateKey}{fileName}{timestamp}{plive_starttime})
Table 6 Authentication fields Field
Description
timestamp
Time when a signed URL is generated. The value is a Unix timestamp, which is the number of seconds since January 1, 1970. Unit: second.
Example: 1564731935, that is, the time is 2019.08.02 15:45.
fileName
Back-to-origin URL. During authentication, the value must start with a slash (/) and cannot include the parameters behind ? in the signed URL.
Example: /asset/6b2d740f10b8697d8ea6672868ecdb6f/test.hls
PrivateKey
Signing key, which is used to generate a signed URL.
The key can contain 16 to 32 characters in only letters and digits.
exper (optional)
Video preview duration, in second. Only MP4 and HLS videos can be previewed.
Specify this parameter only for preview. In other cases, this parameter is not required for calculating the signed URL.
(Optional) plive
Start time of pseudo-streaming, in UTC time. This field is valid only for the HLS format.
Specify this parameter only for pseudo-streaming. In other cases, this parameter is not required for calculating the signed URL. The preview and Pseudo-Streaming functions cannot be enabled at the same time.
Original URL: http://1.cdn.myhuaweicloud.com/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.hls private_key: 32d6b2d740f10b86 timestamp: 1547123166 fileName: /asset/6b2d740f10b8697d8ea6672868ecdb6f/test.hls exper: 300 plive: 1704074400
- Enabling preview
auth_key = sha256(32d6b2d740f10b86/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.hls1547123166300) = 3a935cf1d8299fe63ec8d4e0afb5ef3304883a702a4e760f3c5ae838a4b69768
- Enabling pseudo-streaming
auth_key = sha256(32d6b2d740f10b86/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.hls15471231661704074400) = 3a935cf1d8299fe63ec8d4e0afb5ef3304883a702a4e760f3c5ae838a4b69768
- Preview enabled
http://1.cdn.myhuaweicloud.com/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.hls?auth_key=3a935cf1d8299fe63ec8d4e0afb5ef3304883a702a4e760f3c5ae838a4b69768×tamp=1547123166&exper=300
- Pseudo-streaming enabled
http://1.cdn.myhuaweicloud.com/asset/6b2d740f10b8697d8ea6672868ecdb6f/test.hls?auth_key=3a935cf1d8299fe63ec8d4e0afb5ef3304883a702a4e760f3c5ae838a4b69768×tamp=1547123166&plive=1704074400
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot