Viewing Events
The Events page gives you a full view of your asset security status, helping you determine the priority of handling the events in a timely manner and analyze the security trends.
On the Events page, you can:
- View information about threat alarms, vulnerabilities, risks, compliance check, violations, and public opinions.
- View real-time detection data from other security products.
- Filter events by time range or filter. The events of the last seven days are displayed by default.
- View detailed events on the console or view them in JSON format.
- Customize the event list.
- Mark the processing status of events
Constraints
- When you search for events by filter, a maximum of 10,000 events can be displayed.
- Only the events of the last 180 days can be displayed.
Prerequisites
- SA has received the detection results or events from other security products.
Procedure
- Log in to the management console.
- Click
 in the upper left corner of the page and choose .
in the upper left corner of the page and choose . - In the navigation pane on the left, choose Events.
Figure 1 Viewing the event list
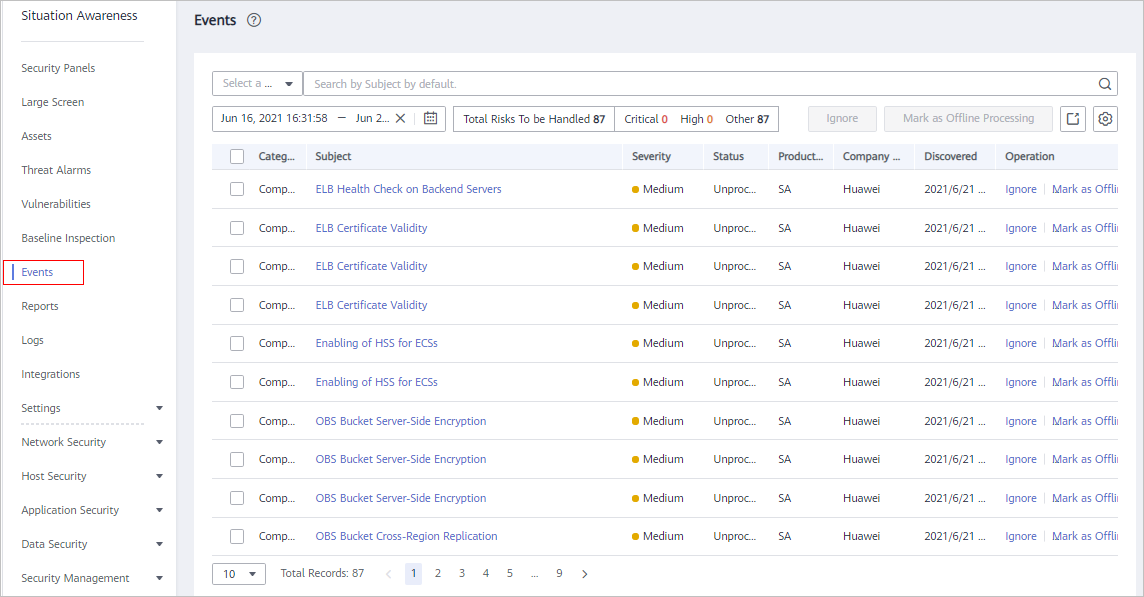
- Filter and view events.
- Select a filter, click
 , and view the event displayed.
, and view the event displayed. - If there are still a large number of events after filtering, add one or more filter criteria and/or select a time range to quickly search for events you want.
- To add one or more filter criteria, configure the corresponding categories in the filter box and then click
 .
. - To specify a time range, configure a time period in the time filter box and click OK.
- To add one or more filter criteria, configure the corresponding categories in the filter box and then click
- Select a filter, click
- View the event list.
In the displayed list, only the events matching the filter criteria are displayed, as well as their statistics.
- View the details of an event.
- Locate the row of the event you want to view, click the subject in the Subject column. The Details pane is displayed on the right.
Figure 2 Details
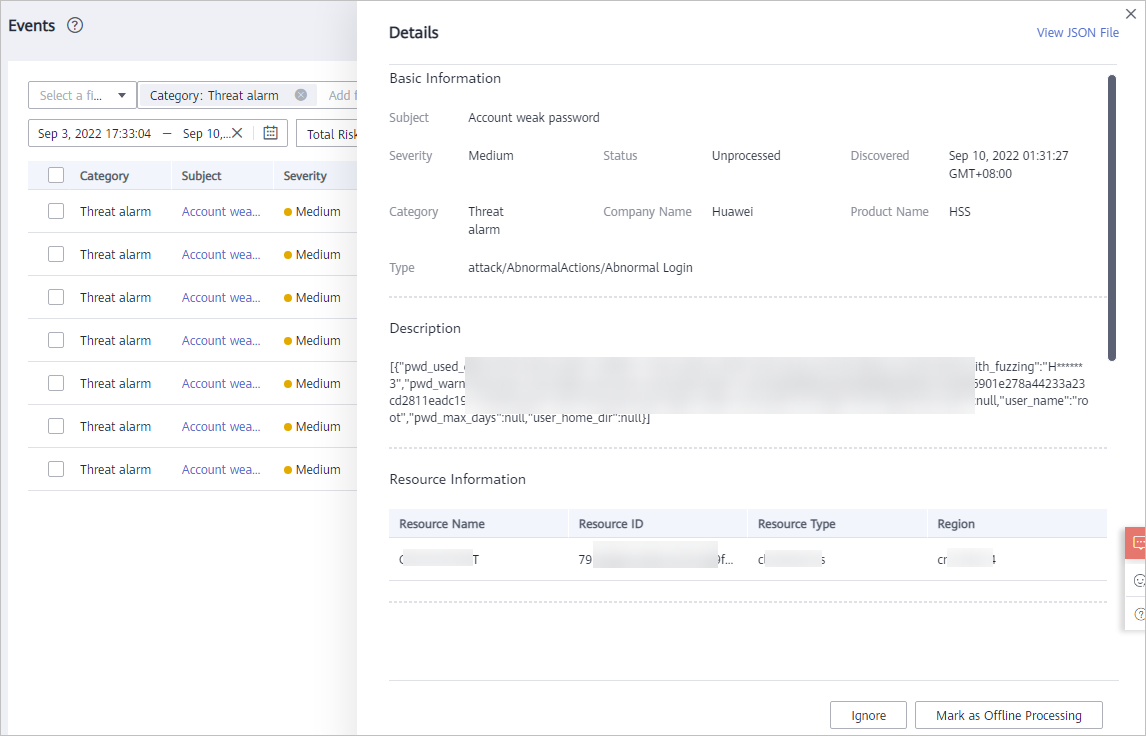
- On this pane, the Basic Information, Description, Resource Information, Attack Information, and Tenant Information are listed. For more details, see Table 1.
Table 1 Parameters on the event details page Parameter
Description
Basic Information
Basic information about an event, including the subject, severity, status, discovery time, category, company name, product name, and type.
Description
Brief description of an event.
Resource Information
Information about affected resources, including the resource name, resource ID, resource type, and the region where the affected resource locates.
Tenant Information
Information about affected users, including the tenant ID, project name, project ID, and region where the user account is registered.
Attack Source Information
Attack source information, including the IP address, port, and longitude from where an attack originates.
Attacked Resource Details
Information about the attacked resource, including the attacked IP address and port.
Check Results
Information about the associated detection results, including the associated resource name and result source.
Vulnerability Information
Vulnerability result information, including the vulnerability ID, CVSS score, CVSS version, and provider.
Affected Products
Vulnerability impact scope information, including affected resource versions and security product versions.
Compliance Information
Basic information about compliance check, including check items and check results.
Involved CVE
CVE ID of the vulnerability.
References:
Related reference links.
Repair/Handling Suggestion
Details of risk repair or handling suggestions.
- On the Details pane, Click View JSON File in the upper right corner to view the event details in a JSON file.
- Locate the row of the event you want to view, click the subject in the Subject column. The Details pane is displayed on the right.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





