Managing Security Devices
Prerequisites
You have logged in to the Huawei Qiankun console and have the device management permission of the device lifecycle management service.
Context
The security device management system is provided by Huawei Qiankun for MSPs to remotely monitor and manage security devices.
MSPs can quickly detect the running status and package deployment of managed security devices, implementing real-time remote monitoring and rapid emergency handling.
Procedure
- Choose in the upper right corner of the console. The Security Devices page is displayed.
Figure 1 Security device management page
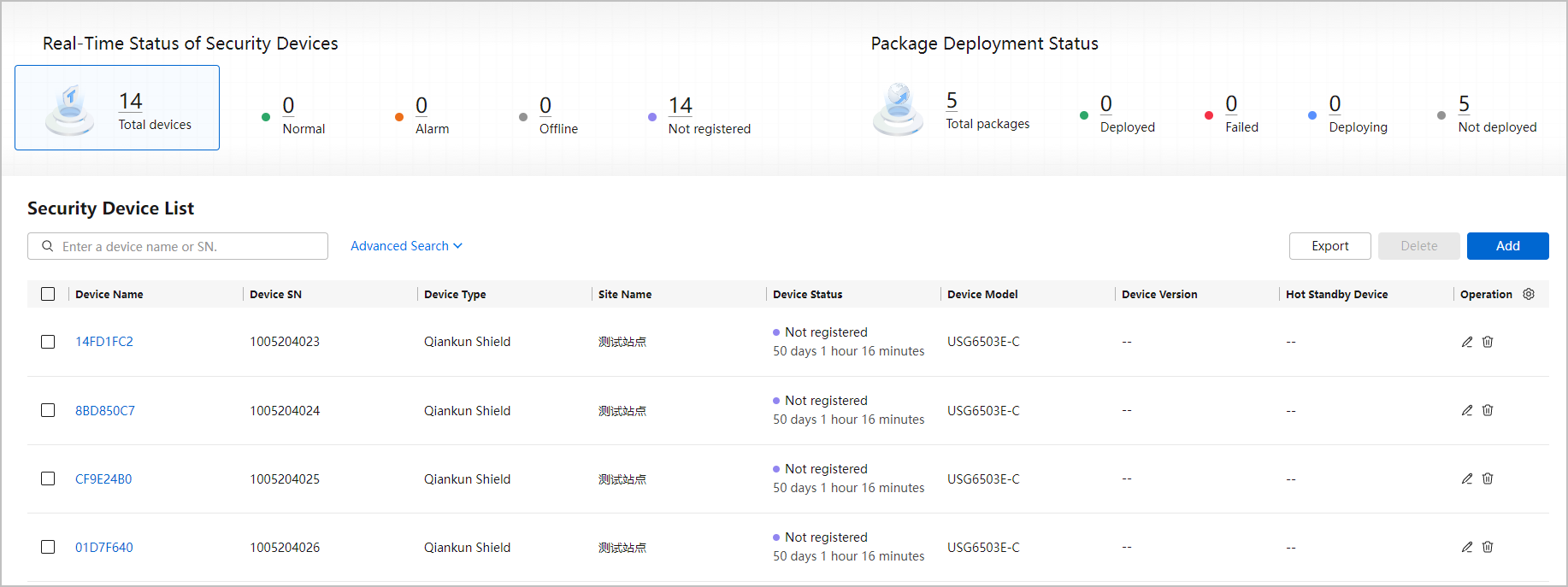
- The security device overview is displayed in the upper part of the page.
- Real-Time Status of Security Devices: displays the total number of security devices added by the current tenant and the distribution of devices in different states. Table 1 describes the device states.
Table 1 Description of device states Device State
Description
Possible Cause
Normal
A device is online.
N/A
Offline
A device is offline.
The network connectivity is abnormal or device configurations are lost.
Not registered
A device fails to go online.
The certificate expires, the network between the device and the Huawei Qiankun platform is disconnected, the device version or model is not supported, the registration service is not started, or IP address conflicts exist on the network.
A device is invalid.
No device version information is available.
Alarm
A device is online and generates alarms.
The device configuration fails to be delivered, the CPU or memory usage of the device is high, a non-standard optical module is used on the device, or a network storm occurs.

If a device is invalid, delete the device and add it again.
- Package Deployment Status: displays the deployment states of packages for all security devices, as described in Table 2.
Table 2 Description of package deployment states Package State
Description
Deployed
After a device goes online, the package is successfully activated and configurations are successfully delivered to the device.
Failed
After a device goes online, the package fails to be activated or configurations fail to be delivered to the device.
Deploying
After a device goes online, the package is being activated and configurations are being delivered.
Not deployed
The device is not online, the package is not activated, and configurations are not delivered.
- Real-Time Status of Security Devices: displays the total number of security devices added by the current tenant and the distribution of devices in different states. Table 1 describes the device states.
- The security device list is displayed in the lower part of the page. The device information includes the device name, device SN, home tenant, home site, bypass function status, and working mode.
- The security device overview is displayed in the upper part of the page.
- Add a security device.
Click Add, enter related information based on Table 3, and click OK.
Figure 2 Adding a security device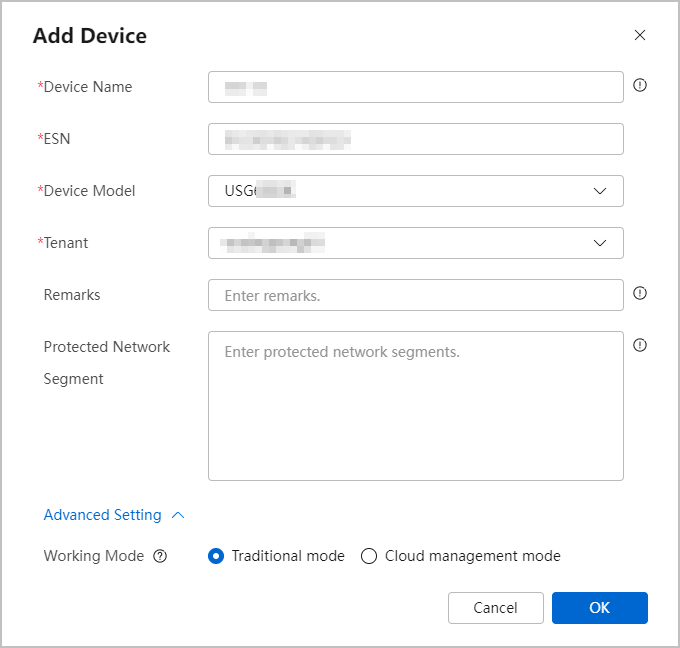
Table 3 Description of security device parameters Parameter
Description
Device Name
Name of a security device. The value can contain only letters, digits, and special characters (excluding spaces).
SN
Equipment serial number, which uniquely identifies a device.
Device Model
Currently, USG6603F-C and USG6000E series firewalls are supported.
Tenant
Managed tenant to which a managed security device belongs.
Protected Network Segment
Network segments to be protected. You can configure multiple protected network segments separated by carriage return characters. For example:
10.0.0.0/11
10.0.0.0-10.31.255.255
Working Mode
- Traditional mode (default): You need to log in to the device to complete network configurations.
- Cloud management mode: You can complete basic network configurations for the device on the console.
- Export the security device list.
Click Export to export the current security device list.

A maximum of 10,000 device data records can be exported. If the exported CSV file contains fields starting with special characters @ - + =, CSV injection risks may exist.
- View security device details.
Click a security device name. The Device Details page is displayed on the right, showing device information such as the device name, CPU and memory usage, interface outbound rate, and interface inbound rate.
Figure 3 Device Details page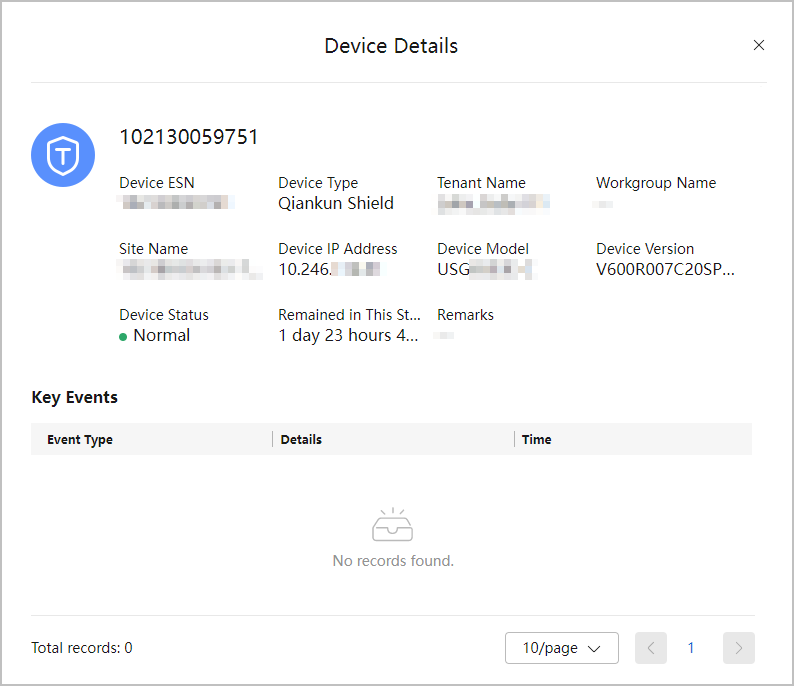
- Perform operations on security devices. You can search for, edit, and delete security devices, bind hot standby devices to them, and configure the bypass function. Table 4 describes these operations in detail.
Table 4 Operations that can be performed on security devices Operation
Description
Search
- Search by keyword: Enter a device name or SN in the search box, and click
 or press Enter.
or press Enter. - Advanced search: Click Advanced Search, and enter search criteria including the tenant name, device status, and device type.
Edit
Select a security device, click
 in the security device list, and modify the device name.
in the security device list, and modify the device name.Delete
Select a security device, and click
 in the Operation column or Delete to delete the security device. After a device is deleted, you cannot handle the events detected by it. Exercise caution when performing this operation.
in the Operation column or Delete to delete the security device. After a device is deleted, you cannot handle the events detected by it. Exercise caution when performing this operation.Remote login
Select a security device, click
 in the list, enter the management view, and log in to the device remotely.NOTE:
in the list, enter the management view, and log in to the device remotely.NOTE:Only devices whose statuses are Normal or Alarm support the remote login function.
- Search by keyword: Enter a device name or SN in the search box, and click
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





