Security Configuration
After protection is enabled, you can set security configurations, including common login locations, common login IP addresses, SSH login IP address whitelist, and the automatic isolation and killing of malicious programs.
- Log in to the management console.
- In the upper left corner of the page, select a region, click
 , and choose .
, and choose .
Configuring Common Login Locations
After you configure common login locations, HSS will generate alarms on the logins from other login locations. A server can be added to multiple login locations.
- On the Common Login Locations tab, click Add Common Login Location.
Figure 1 Adding a common login location
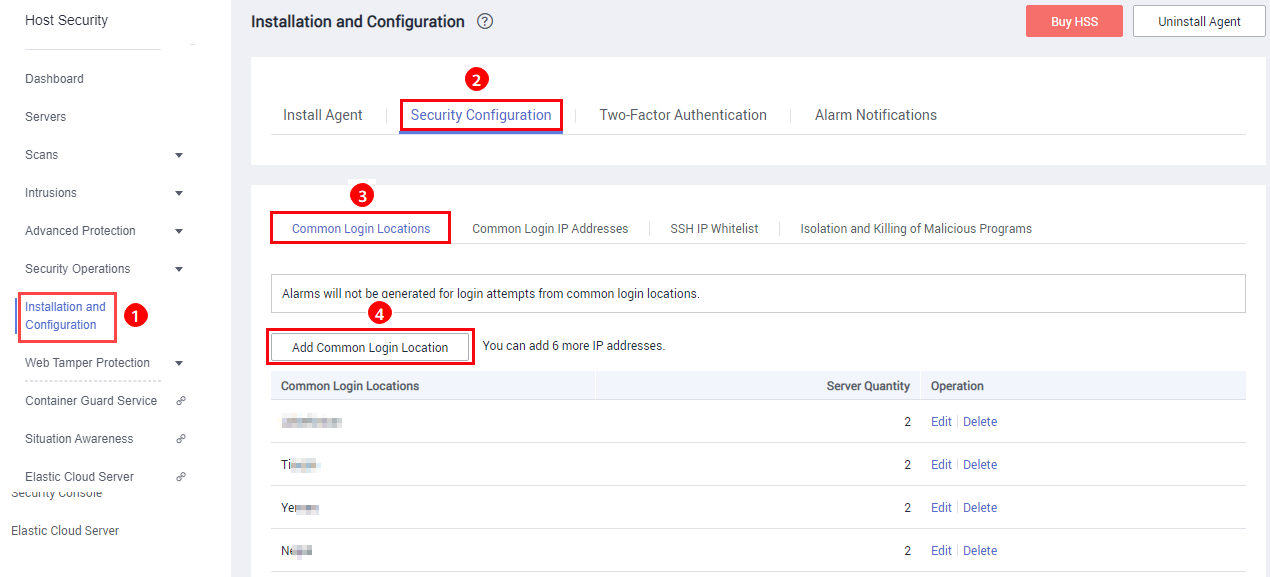
- In the displayed dialog box, set the location and servers.
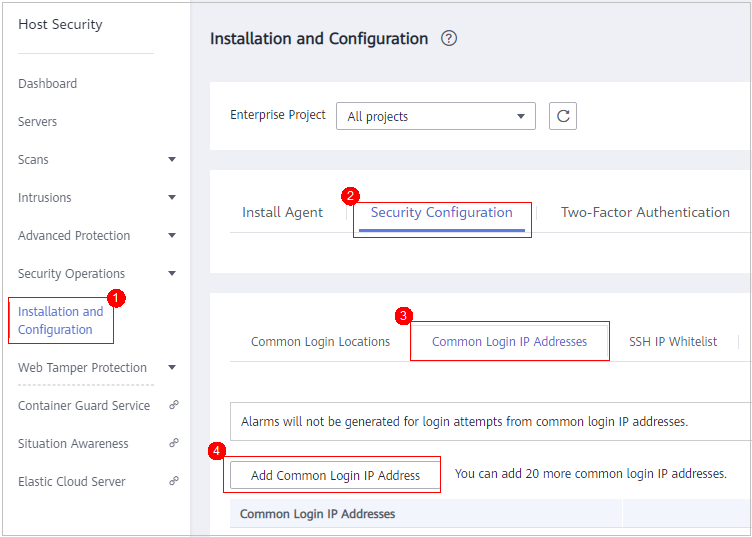
Configuring Common Login IP Addresses
After you configure common IP addresses, HSS will generate alarms on the logins from other IP addresses.
- On the Common Login IP Addresses tab, click Add Common Login IP Address.
Figure 2 Adding a common login IP address
- In the displayed dialog box, set the login IP address and servers.

A common login IP address must be a public IP address or IP address segment. Otherwise, you cannot remotely log in to the server in SSH mode.
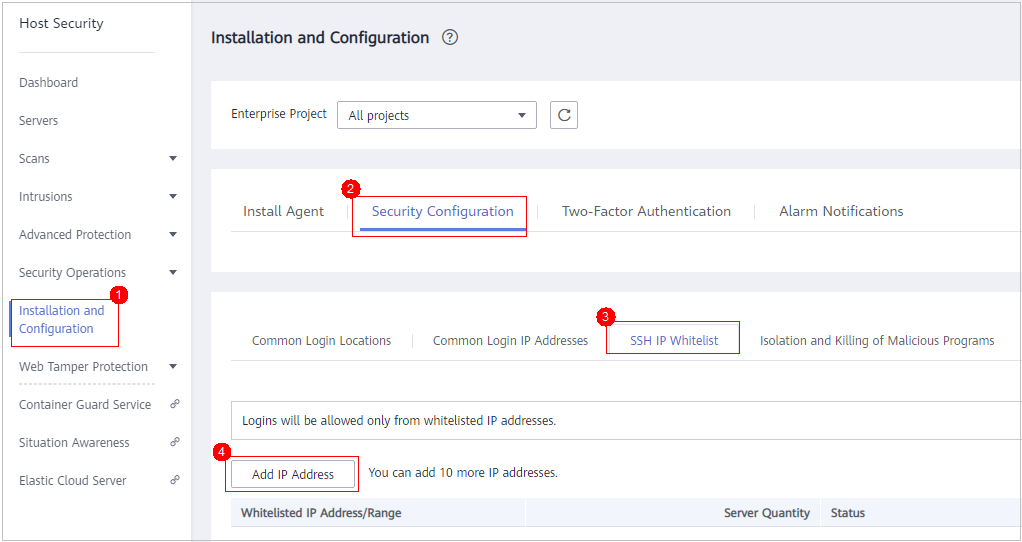
Configuring an SSH Login IP Address Whitelist
The SSH login whitelist controls SSH access to servers, effectively preventing account cracking.
After you configure an SSH login IP address whitelist, SSH logins will be allowed only from whitelisted IP addresses.
- Before enabling this function, ensure that all IP addresses that need to initiate SSH logins are added to the whitelist. Otherwise, you cannot remotely log in to your server using SSH.
If your service needs to access a server, but not necessarily via SSH, you do not need to add its IP address to the whitelist.
- Exercise caution when adding an IP address to the whitelist. This will make HSS no longer restrict access from this IP address to your servers.

The SSH IP address whitelist does not take effect for servers running Kunpeng EulerOS (EulerOS with ARM), or Centos 8.0 or later.
- On the SSH IP Whitelist tab, click Add IP Address.
Figure 3 Adding an SSH login IP address to whitelist
- In the Add IP Address dialog box, enter an IP address and select servers.

A whitelisted IP address must be a public IP address or IP address segment (IPv4 and IPv6 addresses are supported). Otherwise, you cannot remotely log in to the server in SSH mode.
Isolating and Killing Malicious Programs
HSS can automatically isolate and kill malicious programs, including web shells, Trojans, and worms. For more information, see Intrusion Detection > Malicious Programs in Functions and Features.

Automatic isolation and killing may cause false positives. You can choose Intrusions > Events to view isolated malicious programs. You can cancel the isolation or ignore misreported malicious programs. For details, see Checking and Handling Intrusion Events.

- When a program is isolated and killed, the process of the program is terminated immediately. To avoid impact on services, check the detection result, and cancel the isolation of or unignore misreported malicious programs (if any).
- If Isolate and Kill Malicious Programs is set to Disable on the Isolation and Killing of Malicious Programs tab, HSS will generate an alarm when it detects a malicious program.
To isolate and kill the malicious programs that triggered alarms, choose Intrusions > Events and click Malicious program (cloud scan).
Enabling 2FA
- 2FA requires users to provide verification codes before they log in. The codes will be sent to their mobile phones or email boxes.
- You have to choose an SMN topic for servers where 2FA is enabled. The topic specifies the recipients of login verification codes, and HSS will authenticate login users accordingly.
Prerequisites
- The enterprise, premium, or WTP edition of HSS has been enabled.
- You have created a message topic whose protocol is SMS or email.
- Server protection has been enabled.
- Linux servers require user passwords for login.
- To enable two-factor authentication, you need to disable the SELinux firewall.
- On a Windows server, 2FA may conflict with G01 and 360 Guard (server edition). You are advised to stop them.
- If 2FA is enabled, you cannot log in to the servers running a GUI Linux OS.
- If you have enabled 2FA on a Linux server, you cannot log in to it through CBH.
- If you have enabled 2FA on a server, you cannot log in to the server through CloudShell.
- You can add up to 10 mobile numbers and email addresses at a time. A topic can have up to 10,000 mobile numbers and email addresses.
Procedure
- On the Two-Factor Authentication tab, click Enable 2FA.
Figure 5 2FA

- In the displayed Enable 2FA dialog box, select an authentication mode.
- SMS/Email
You need to select an SMN topic for SMS and email verification.
- The drop-down list displays only notification topics that have been confirmed.
- If there is no topic, click View to create one. For details, see Creating a Topic.
- During authentication, all the mobile numbers and email addresses specified in the topic will receive a verification SMS or email. You can delete mobile numbers and email addresses that do not need to receive verification messages.
Figure 6 SMS/Email
- Verification code
Figure 7 Verification code

- SMS/Email
- Click OK. After 2FA is enabled, it takes about 5 minutes for the configuration to take effect.

When you log in to a remote Windows server from another Windows server where 2FA is enabled, you need to manually add credentials on the latter. Otherwise, the login will fail.
To add credentials, choose Start > Control Panel, and click User Accounts. Click Manage your credentials and then click Add a Windows credential. Add the username and password of the remote server that you want to access.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot








