Using IAM Identity Policies to Grant Access to Global Accelerator
System-defined permissions in Identity Policy-based Authorization provided by Identity and Access Management (IAM) let you control access to Global Accelerator. With IAM, you can:
- Create IAM users or user groups for personnel based on your enterprise's organizational structure. Each IAM user has their own identity credentials for accessing Global Accelerator resources.
- Grant users only the permissions required to perform a given task based on their job responsibilities.
- Delegate another HUAWEI ID or cloud service to perform professional and efficient O&M on your Global Accelerator resources.
If your HUAWEI ID meets your permissions requirements, you can skip this section.
Figure 1 shows the process flow of identity policy-based authorization.
Prerequisites
Before granting permissions, learn about system-defined permissions in Identity Policy-based Authorization. To grant permissions for other services, learn about all system-defined policies/roles supported by IAM.
Process Flow
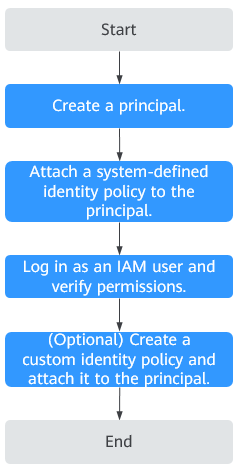
- On the IAM console, create an IAM user or create a user group.
- Attach a system-defined identity policy (GAReadOnlyPolicy as an example) to the user or user group.
- Log in as the IAM user and verify permissions.
In the authorized region, perform the following operations:
- Click
 on the upper left corner to display Service List and choose Networking > Global Accelerator. Click Buy Global Accelerator in the upper right corner. If the global accelerator cannot be created, the GAReadOnlyPolicy policy is in effect.
on the upper left corner to display Service List and choose Networking > Global Accelerator. Click Buy Global Accelerator in the upper right corner. If the global accelerator cannot be created, the GAReadOnlyPolicy policy is in effect. - Choose another service from Service List. The system prompts you that you have insufficient permissions to access the service, the GAReadOnlyPolicy policy is in effect.
- Click
Example Custom Identity Policies
You can create custom identity policies to supplement system-defined identity policies. For the actions supported for custom identity policies, see "Identity Policy-Based Authorization" in the Global Accelerator API Reference.
To create a custom policy, choose either visual editor or JSON.
- Visual editor: Select cloud services, actions, resources, and request conditions. You do not need to have knowledge of the policy syntax.
- JSON: Create a JSON policy or edit an existing one.
For details, see Creating a Custom Identity Policy and Attaching It to a Principal.
When creating a custom policy, use the Resource element to specify the resources the policy applies to and use the Condition element (service-specific condition keys) to control when the policy is in effect. For the supported resource types and condition keys, see "Identity Policy-based Authorization" in the Global Accelerator API Reference. The following lists examples of custom identity policies for Global Accelerator.
- Example 1: Grant the permission to create and update a global accelerator.
{ "Version": "5.0", "Statement": [ { "Effect": "Allow", "Action": [ "ga:accelerator:create", "ga:accelerator:update" ] } ] } - Example 2: Create a custom identity policy that contains multiple actions.
A custom identity policy can contain the actions of one or more services.
Example identity policy containing multiple actions:
{ "Version": "5.0", "Statement": [ { "Effect": "Allow", "Action": [ "ga:accelerator:create", "ga:accelerator:update", "ga:listener:create" ] }, { "Effect": "Deny", "Action": [ "ga:accelerator:delete", "ga:listener:delete" ] }, { "Effect": "Allow", "Action": [ "eip:publicIps:create", "eip:publicIps:update" ] } ] }
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





