Overview
Security Group
A security group is a collection of access control rules for cloud resources, such as cloud servers, containers, and databases, that have the same security protection requirements and that are mutually trusted. After a security group is created, you can configure access rules that will apply to all cloud resources added to this security group.
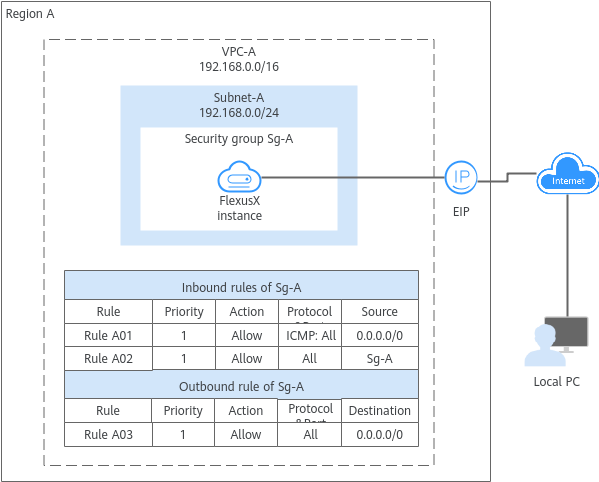
- Security group Sg-A has a custom inbound rule to allow ICMP traffic to the instance from your PC over all ports. However, the security group does not contain a rule to allow external access to the instance over the SSH port 22 or RDP port 3389. As a result, you cannot remotely log in to the FlexusX instance from your PC.
- If the FlexusX instance needs to access the Internet through an EIP, the outbound rule of Sg-A must allow all traffic from the FlexusX instance to the Internet.
For more information about security groups, see Security Group and Security Group Rule Overview.
A security group works only when the network communication is normal. If two FlexusX instances are in the same security group but in different VPCs, the instances cannot communicate with each other. To enable communications between the two instances, connect the two VPCs first. For details, see Connecting VPCs.
Security Group Rules
After a security group is created, you can add rules to it. A rule applies either to inbound traffic (ingress) or outbound traffic (egress). Any FlexusX instances added to the security group are protected by the rules of that group. For details about more configuration examples, see Security Group Examples.
|
Parameter |
Description |
|---|---|
|
Priority |
The value range is from 1 to 100. A smaller value indicates a higher priority. Security group rules are matched first by priority and then by action. Deny rules take precedence over allow rules. |
|
Action |
The action can be Allow or Deny. If the protocol, port, source or destination of the traffic matches a security group rule, traffic will be allowed or denied. |
|
Type |
IPv4 or IPv6. |
|
Protocol & Port |
Network protocol type and port range.
|
|
Source/Destination |
Source address of traffic in the inbound direction or destination address of traffic in the outbound direction. The source or destination can be an IP address, security group, or IP address group.
|
You can create a custom security group or use the default one provided by the system. The default security group allows all outbound traffic and denies inbound traffic. FlexusX instances in a security group can communicate with each other without adding any rules.
|
Direction |
Action |
Type |
Protocol & Port |
Source/Destination |
Description |
|---|---|---|---|---|---|
|
Inbound |
Allow |
IPv4 |
All |
Source: default security group (default) |
Allows instances in the security group to communicate with each other over IPv4 protocols. |
|
Inbound |
Allow |
IPv6 |
All |
Allows instances in the security group to communicate with each other over IPv6 protocols. |
|
|
Outbound |
Allow |
IPv4 |
All |
Destination: 0.0.0.0/0 |
Allows access from instances in the security group to any IPv4 address over any port. |
|
Outbound |
Allow |
IPv6 |
All |
Destination: ::/0 |
Allows access from instances in the security group to any IPv6 address over any port. |
Security Group Constraints
- By default, you can create up to 100 security groups in your cloud account.
- By default, you can add up to 50 rules to a security group.
- For better network performance, you are advised to associate no more than five security groups with a FlexusX instance or supplementary network interface.
- You can add up to 20 instances to a security group at a time.
- You can add up to 1,000 instances to a security group.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot