Rotating Secret Version
If the secrets are not updated for a long time, the key information protected by the secrets, such as important passwords, tokens, certificates, SSH keys, and API keys, may be disclosed. Periodic secret rotation can enhance the security of the protected plaintext information. This section describes how to enable secret rotation.
Constraints
- The secret must be a rotated secret.
- The minimum rotation period is 4 hours.
- The secret account must be an existing database account.
Manual Rotation
- Log in to the DEW console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose .
- Click a secret name to access its details page.
- In the Version area, click Rotate Now.
- In the displayed dialog box, enter ROTATE, and click OK.
- Wait until a message is displayed in the upper right corner, indicating the rotation starts now.
- After the version is rotated, the latest secret version is in SYSCURRENT state.
Automatic Rotation
- Log in to the DEW console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project. - In the navigation pane on the left, choose .
- Click a secret name to access its details page.
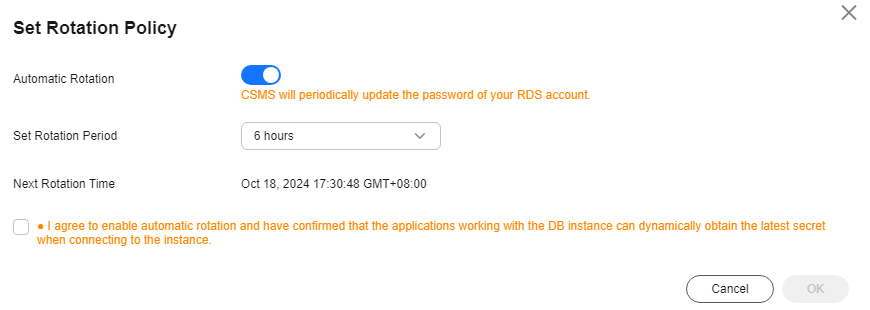
- Click Set Rotation Policy in the upper right corner. In the displayed dialog box, enable Automatic Rotation, as shown in Figure 1.
- Set an automatic rotation period, select the risk warning, and click OK. A message indicating the rotation policy is set successfully is displayed in the upper right corner.
- After automatic rotation is enabled, if the secret version fails to be rotated, you can view the number of rotation failures in the current version area. You can click the number of rotation failures to view the rotation failure records.
- If the rotation fails for three consecutive times, the automatic rotation button of the secret is disabled.
- Rotation failure records cannot be manually deleted. They are stored for one month and will be automatically deleted after one month.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot