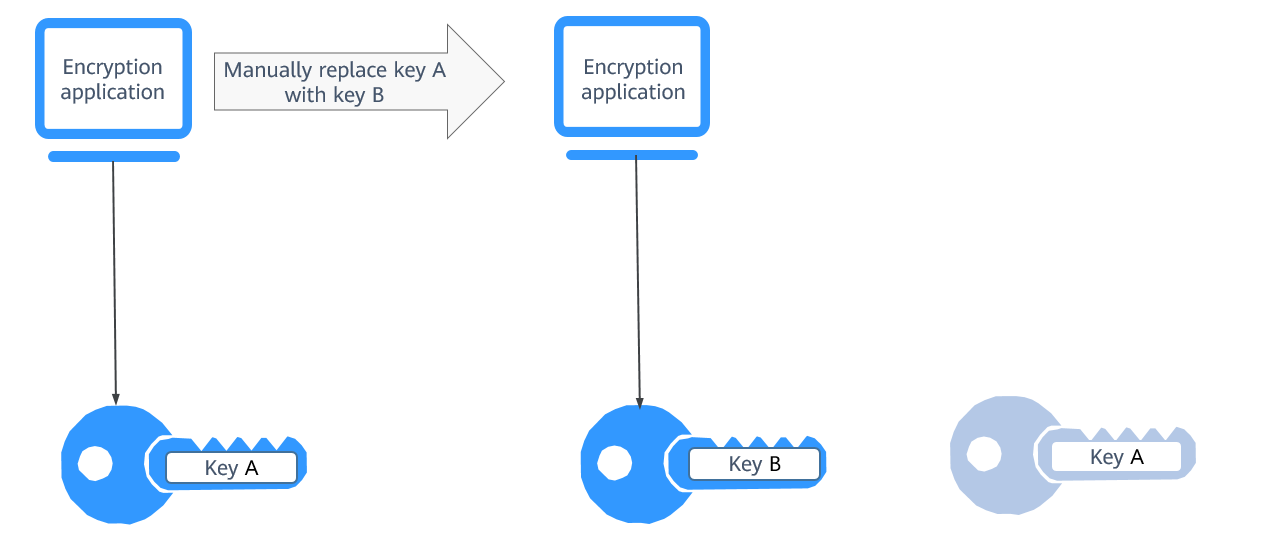
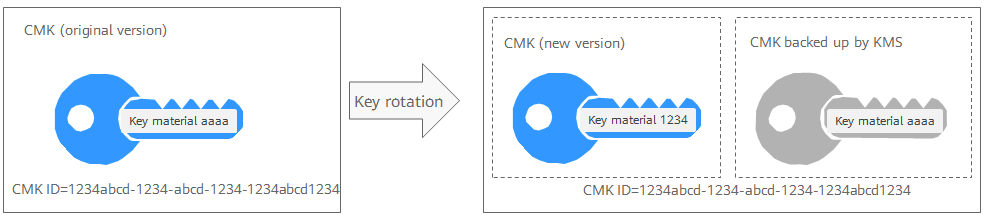
Enabling Key Rotation
KMS allows you to periodically rotate keys to enhance security for keys and service data. This section describes how keys are rotated in KMS and how to configure key rotation.
By default, automatic key rotation is disabled for a custom key. Every time you enable key rotation, KMS automatically rotates custom keys based on the rotation period you set. Once key rotation is enabled, certain fees will be charged. For details, see How Is Rotation Charged for a CMK?.
Constraints
- A disabled custom key is never rotated, even if rotation is enabled for it.
KMS resumes rotation when this custom key is enabled. If you enable this custom key after one rotation period has passed, KMS will rotate it within 24 hours.
- Only CMKs can be rotated.
- Only symmetric keys can be rotated.
- Key rotation is supported only for enabled keys with KMS-generated key materials.
- Enabling key rotation may incur additional fees. For details, see Billing Description.
Enabling Key Rotation
- Log in to the DEW console.
- Click
 in the upper left corner and select a region or project.
in the upper left corner and select a region or project.
- Click the custom key name to access its details page.
- Click the Rotation Policy tab. The rotation switch is displayed.
- Click
 to enable key rotation.
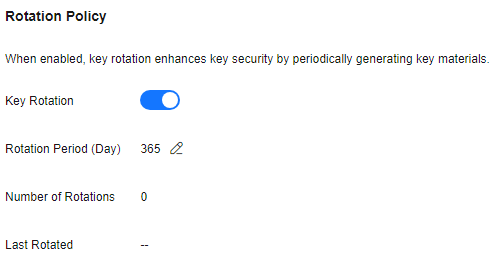
to enable key rotation. - Configure the rotation period and click OK, as shown in Figure 3. For more information, see Table 2.
Table 2 Key rotation parameters Parameter
Description
Key rotation
Rotation switch. The default status is
 .
. : disabled
: disabled : enabled
: enabledAfter rotation is enabled, the key will be rotated based on your set period.
NOTE:A disabled custom key is never rotated, even if rotation is enabled for it.
KMS resumes rotation when this custom key is enabled. If you enable this custom key after one rotation period has passed, KMS will rotate it within 24 hours.
Rotation Period (day)
Rotation period (day). The value is an integer ranging from 30 to 365. The default value is 365.
Configure the period based on how often a custom key is used. If it is frequently used, configure a short period. Otherwise, set a long one.
- Check rotation details, as shown in the following figure.
Figure 4 Key rotation details
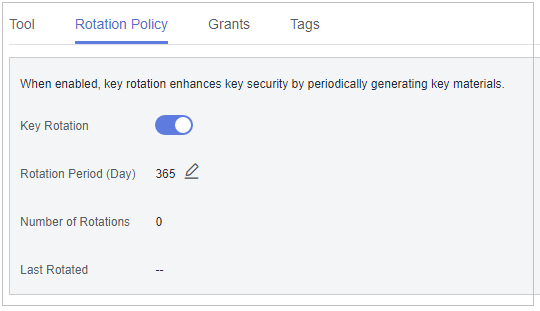
You can click
 to change the rotation period. After the period is changed, KMS rotates the key by the new period.
to change the rotation period. After the period is changed, KMS rotates the key by the new period.
Disabling Key Rotation
- Click the custom key name to access its details page.
- Click the Rotation Policy tab.
- Click
 to disable key rotation.
to disable key rotation. - In the displayed confirmation dialog box, click OK.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot