Overview
- Independent cryptographic resources: You can use exclusive resources, such as HSMs and KMS, to ensure the independence and security of encryption operations.
- Customized cryptographic policies: You can customize cryptographic algorithms, key management policies, and access control policies as required.
- Data isolation: Ensure that your data is completely separated from the data of other users through physical or logical isolation to prevent data leakage.
Restrictions
- Dedicated HSM instances must be used together with VPC. After a Dedicated HSM instance is created, you need to configure its VPC, security group, and NIC on the management console before using it.
- To manage Dedicated HSM instances, you need to deploy the Dedicated HSM management tool in the same VPC as the instances.
Supported Cryptography Algorithms
You can use international common cryptographic algorithms to meet various user requirements.
|
Category |
Common Cryptographic Algorithm |
|---|---|
|
Symmetric cryptographic algorithm |
AES |
|
Asymmetric cryptographic algorithm |
RSA, DSA, ECDSA, DH, and ECDH |
|
Digest algorithm |
SHA1, SHA256, and SHA384 |
Supported HSMs
|
HSM Type |
Function |
Scenario |
|---|---|---|
|
Cloud HSM |
|
Basic password calculations in applications of a wide range of industries, such as identity authentication, data protection, SSL keys, and computation offloading. |
|
Financial HSM |
|
Cryptographic calculation in financial systems, such as card issuing systems and point of sale (POS) systems |
|
Signature verification server |
|
Signature usage in Certificate Authority (CA) systems, certificate verification, encrypted transmission of a large amount of data, and identity authentication |
Operation Guide
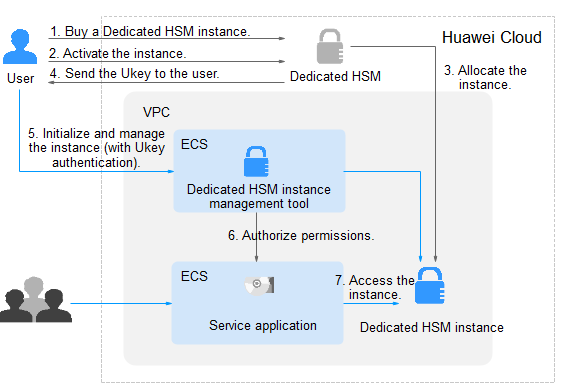
To use Dedicated HSM on the cloud, you can create Dedicated HSM instances through the management console. After a Dedicated HSM instance is created, you will receive the UKey sent by Dedicated HSM. You need to use the UKey to initialize and control the instance. You can use the management tool to authorize service applications the permission to access Dedicated HSM instances. Figure 1 illustrates the operation flow.
Table 3 describes the operation guide.
|
No. |
Procedure |
Description |
Operated By |
|---|---|---|---|
|
1 |
Create a Dedicated HSM instance. |
Create an instance on the Dedicated HSM management console. Huawei Cloud security team will evaluate your use scenarios to ensure that the instance meets your service requirements. Then you can pay for the ordered instance. |
User |
|
2 |
Activate a Dedicated HSM instance. |
After an instance is purchased, you need to configure the instance on the management console. You need to select the VPC where the instance belongs and the function type of the instance. For details, see Activating a Dedicated HSM Instance. |
User |
|
3 |
Allocate a Dedicated HSM instance. |
A security expert will contact you through the contact information you provided and determine whether the instance ordered meets your service requirements. The instance will be allocated after the expert reviews and confirms your order. |
Dedicated HSM security expert |
|
4 |
Obtain the UKey, initialization documents, and software. |
|
Dedicated HSM security expert |
|
5 |
Initialize and manage instances (involving UKey authentication). |
For details, see Initializing a Dedicated HSM Instance. |
User |
|
6 |
Install the security agent and granting access permissions. |
Install and initialize the security agent on service application nodes. For details, see Installing the Security Agent and Granting Access Permissions. |
User |
|
7 |
Access the instance. |
Service applications access the Dedicated HSM instances through APIs or SDK. |
User |
Dedicated HSM and CPCS
Dedicated HSM and CPCS are both used for encryption and security assurance. However, their functions, applications, and management methods differ. For details, see Table 4.
|
Service |
Dedicated HSM |
CPCS |
|---|---|---|
|
Function |
|
|
|
Application |
|
|
|
Management method |
|
|
|
Connection |
|
|
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot