Relationship Between IAM Identities and Operators
Huawei Cloud IAM provides the following types of identities: IAM users, IAM agencies, cloud service agencies, IAM Identity Center users, and federated users.
The operator information reported to CTS audit logs varies depending on the operators identity. The following describes the format specifications of the username (user.name field) and identity ID (principal_id field) of different operators:
|
Operator Identity |
Identity Type (type) |
Operator Name Format (user.name) |
Identity ID Format (principal_id) |
|---|---|---|---|
|
IAM user |
User |
<user-name> |
<user-id> |
|
IAM agency |
AssumedAgency |
<domain-name>/<agency-name> |
<agency-id>:<agency-session-name> |
|
Cloud service agency |
AssumedAgency |
<domain-name>/<agency-name> |
<agency-id>:<agency-session-name> |
|
IAM Identity Center |
AssumedAgency |
<domain-name>/<agency-name> |
<agency-id>:<agency-session-name> |
|
Federated user |
ExternalUser |
<idp_id>/<user-session-name> |
<idp_id>:<user-session-name> |
The Operator column of the trace list displays usernames of operators.
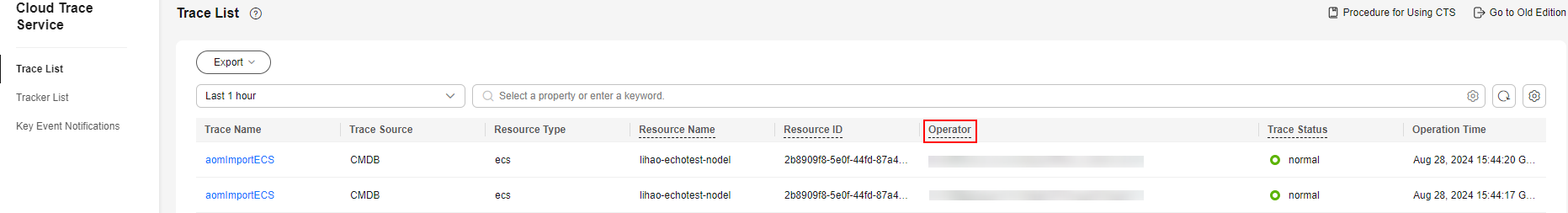
This section provides examples of operator information in the trace list when different user identities are used to perform operations on resources.
IAM User
If the operator is an IAM user, the user field in the audit log is as follows:
{
"access_key_id": "HSTAZ***YE2GA",
"account_id": "7e0d78c85***d0b9b7cba",
"user_name": "IAMUserA",
"domain": {
"name": "IAMDomainB",
"id": "7e0d78c85***d0b9b7cba"
},
"name": "IAMUserA",
"principal_is_root_user": "true",
"id": "f36972ced***d619f1214",
"principal_urn": "iam::7e0d78c85***d0b9b7cba:user:IAMUserA",
"type": "User",
"principal_id": "f36972ced***d619f1214"
}
The user field records the information about the operator, which is IAMUserA (value of the name field) in this example. Note the following fields.
|
Field |
Description |
|---|---|
|
user_name |
Username of the operator. To obtain it, hover over the username in the upper right corner of the console, select My Credentials from the drop-down menu, and locate the name on the right of IAM Username. In this example, it is IAMUserA. |
|
name |
|
|
id |
User ID of the operator. To obtain it, hover over the username in the upper right corner of the console, select My Credentials from the drop-down menu, and locate the name on the right of IAM User ID. In this example, it is f36972ced***d619f1214. |
|
principal_id |
Identity ID of the operator. The format is user-id. In this example, the value is f36972ced***d619f1214. |
|
principal_urn |
URN of the operator. The format is iam::<account-id>:user:<user-name>. In this example, the value is iam::7e0d78c85***d0b9b7cba:user:IAMUserA. |
|
domain.name |
Account name of the operator. To obtain it, hover over the username in the upper right corner of the console, select My Credentials from the drop-down menu, and locate the name on the right of Account Name. In this example, it is IAMUserB. |
|
domain.id |
Account ID of the operator. To obtain it, hover over the username in the upper right corner of the console, select My Credentials from the drop-down menu, and locate the name on the right of Account ID. In this example, it is 7e0d78c85***d0b9b7cba. |
|
account_id |
IAM Agency
If the operator is an IAM agency, the user field in the audit log is as follows:
{
"access_key_id": "HSTAB***6DEEB",
"invoked_by": [
"service.console"
],
"account_id": "302893da***5a7453e5733",
"domain": {
"name": "hc_beta_***",
"id": "302893da***5a7453e5733"
},
"name": "hc_beta_***/agencyname",
"session_context": {
"attributes": {
"created_at": "1724744585642",
"mfa_authenticated": "false"
},
"assumed_by": {
"principal_id": "3cd5b27548***a58b5801d9d"
}
},
"principal_urn": "sts::302893da***5a7453e5733:assumed-agency:agencyname/null",
"type": "AssumedAgency",
"principal_id": "40c79f4571***8bc54784b61:null"
}
The user field records the information about the operator, which is hc_beta_***/agencyname (value of the name field) in this example. Note the following fields.
|
Field |
Description |
|---|---|
|
name |
Username of the operator. The format is <domain-name>/<agency-name>. |
|
principal_id |
Identity ID of the operator. The format is <agency-id>:<agency-session-name>. In this example, the value is 40c79f4571***8bc54784b61:null. |
|
principal_urn |
URN of the operator. For an IAM agency, the format is sts::<account-id>:assumed-agency:<agency-name>/<agency-session-name>. In this example, the value is sts::302893da***5a7453e5733:assumed-agency:agencyname/null. |
|
session_context.assumed_by.principal_id |
ID of the delegated account in IAM. For details, see Switching Roles (by a Delegated Party). |
Cloud Service Agency
If the operator is a cloud service agency, the user field in the audit log is as follows:
{
"access_key_id": "HSTAR***LG6FC",
"account_id": "302893da***53e5733",
"domain": {
"name": "hc_beta_***",
"id": "302893da***53e5733"
},
"name": "hc_beta_***/ServiceLinkedAgencyForCloudTraceService",
"session_context": {
"attributes": {
"created_at": "1724744380046",
"mfa_authenticated": "false"
},
"assumed_by": {
"service_principal": "service.CTS"
}
},
"principal_urn": "sts::302893da***53e5733:assumed-agency:ServiceLinkedAgencyForCloudTraceService/302893da***53e5733",
"type": "AssumedAgency",
"principal_id": "4bc820d3***b786c83:302893da***53e5733"
}
The user field records the information about the operator, which is hc_beta_***/ServiceLinkedAgencyForCloudTraceService (value of the name field) in this example. Note the following fields.
|
Field |
Description |
|---|---|
|
name |
Username of the operator. The format is <domain-name>/<agency-name>. In this example, it is hc_beta_***/ServiceLinkedAgencyForCloudTraceService. |
|
principal_id |
Identity ID of the operator. The format is <agency-id>:<agency-session-name>. In this example, the value is 4bc820d3***b786c83:302893da***53e5733. |
|
principal_urn |
URN of the operator. The format is sts::<account-id>:assumed-agency:<agency-name>/<agency-session-name>. In this example, the value is sts::302893da***53e5733:assumed-agency:ServiceLinkedAgencyForCloudTraceService/302893da***53e5733. |
|
session_context.assumed_by.service_principal |
Name of the delegated cloud service. The format is service.<service-name>. |
IAM Identity Center User
If the operator is a user created in IAM Identity Center, the user field in the audit log is as follows:
{
"access_key_id": "HSTA9***CKG7E",
"invoked_by": [
"service.console"
],
"account_id": "302893da***53e5733",
"domain": {
"name": "hc_beta_***",
"id": "302893da***53e5733"
},
"name": "hc_beta_***/SysReservedV3_evs-FullAccess-***",
"session_context": {
"attributes": {
"created_at": "1724744395079",
"mfa_authenticated": "false"
},
"assumed_by": {
"service_principal": "service.IdentityCenter"
}
},
"principal_urn": "sts::302893da***53e5733:assumed-agency:SysReservedV3_evs-FullAccess-***/IdentityCenterUsername",
"type": "AssumedAgency",
"principal_id": "dbc60d8***ef5fd807:***"
}
The user field records the information about the operator, which is hc_beta_***/SysReservedV3_evs-FullAccess-*** (value of the name field) in this example. Note the following fields.
|
Field |
Description |
|---|---|
|
name |
Username of the operator. For a service-linked agency, the format is <domain-name>/<agency-name>. In this example, the value is hc_beta_***/SysReservedV3_evs-FullAccess-***. |
|
principal_id |
Identity ID of the operator. The format is <agency-id>:<agency-session-name>. In this example, the value is dbc60d8***ef5fd807:***. |
|
principal_urn |
URN of the operator. The format is sts::<account-id>:assumed-agency:<agency-name>/<agency-session-name>. In this example, the value is sts::302893da***53e5733:assumed-agency:SysReservedV3_evs-FullAccess-***/IdentityCenterUsername. |
|
session_context.assumed_by.service_principal |
Name of the entrusted cloud service. The value is fixed at service.IdentityCenter. |
Federated User
If the operator is a federated user, the user field in the audit log is as follows:
{
"access_key_id": "HSTAX***3IBZB",
"account_id": "797c8fc3c***2dc6bf70bd",
"domain": {
"name": "***",
"id": "797c8fc3c***2dc6bf70bd"
},
"name": "provider_name/UserA",
"session_context": {
"federation_data": {
"identity_provider": "provider_name",
"protocol": "SAML",
"group_Ids": [
"fedf7a460***46451be85"
]
}
},
"principal_urn": "sts::797c8fc3c***2dc6bf70bd:external-user:provider_name/UserA",
"type": "ExternalUser",
"principal_id": "provider_name:UserA"
}
The user field records the information about the operator, which is provider_name/UserA (value of the name field) in this example. Note the following fields.
|
Field |
Description |
|---|---|
|
name |
Username of the operator. The format is <idp_id>/<user-session-name>. In this example, the value is provider_name/UserA. |
|
principal_id |
Identity ID of the operator. The format is <idp_id>:<user-session-name>. In this example, the value is provider_name:UserA. |
|
principal_urn |
URN of the operator. The format is sts::<account-id>:external-user:<idp_id>/<user-session-name>. In this example, the value is sts::797c8fc3c***2dc6bf70bd:external-user:provider_name/UserA. |

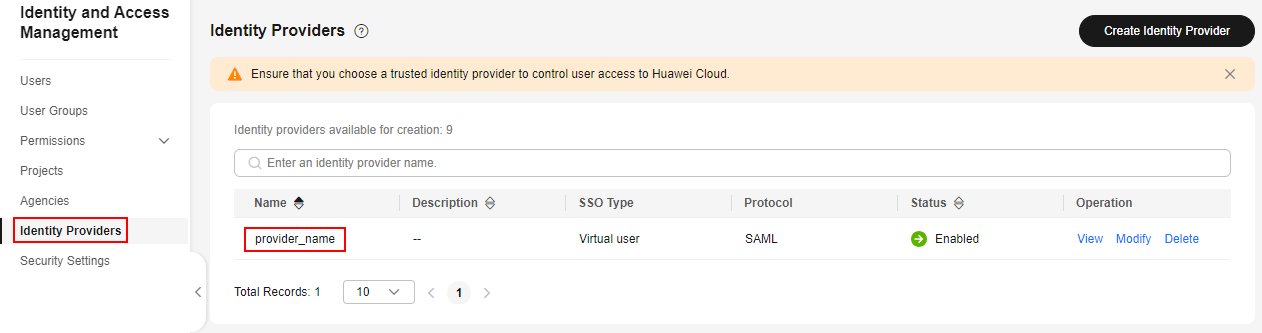
idp_id indicates the name of the IAM identity provider. To obtain its value, log in to the IAM console and view the identity provider name on the Identity Providers page.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





