Permission Policy Configuration Examples
You can configure permission policies for different IAM users based on service requirements.
Example 1: Allowing an IAM User Who Is Not in Any Enterprise Projects to Have All Cloud Connection Permissions
An IAM user who is not in any enterprise projects wants to have all Cloud Connect permissions, for example, performing operations on Cloud Connect resources such as network instances, bandwidth packages, inter-region bandwidths, and routes, and operations such as cross-border permit application and cross-account authorization.
To grant the permissions to this IAM user, perform the following operations:
- Log in to the management console.
- On the homepage, hover over the username in the upper right corner and choose Identity and Access Management from the drop-down list.
Figure 1 Identity and Access Management
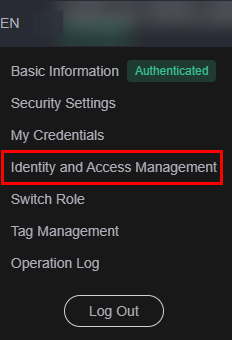
- In the navigation pane on the left, choose User Groups.
- In the upper right corner, click Create User Group.
Figure 2 Creating a user group
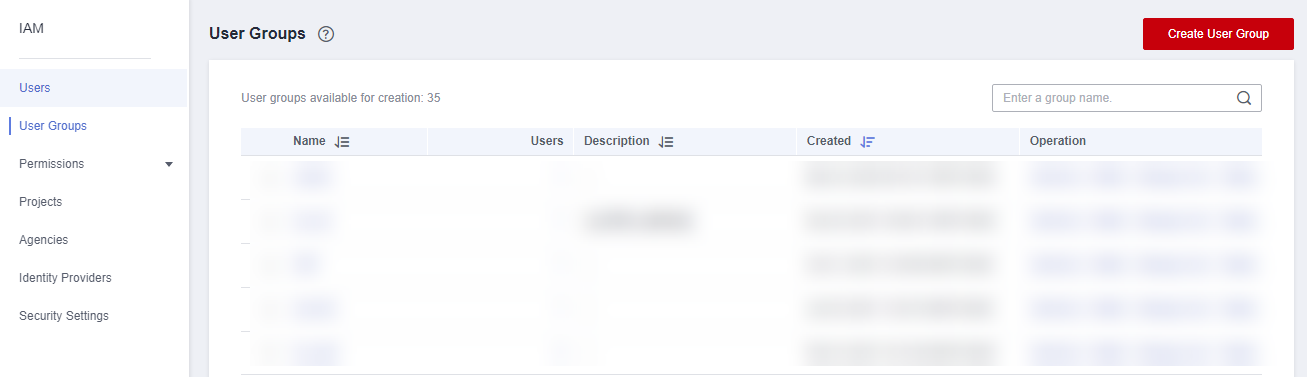
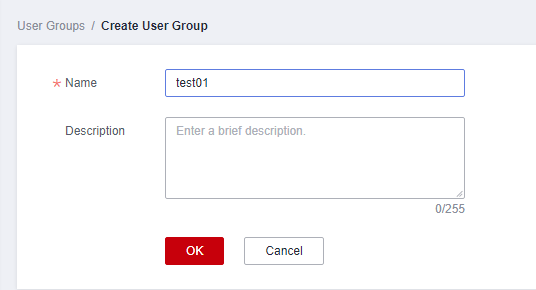
- Configure the parameters and click OK.
Figure 3 Configuring user group parameters
- Locate the created user group and click its name.
- Click By IAM Project on the right and then click Authorize.
Figure 4 Authorizing a user group
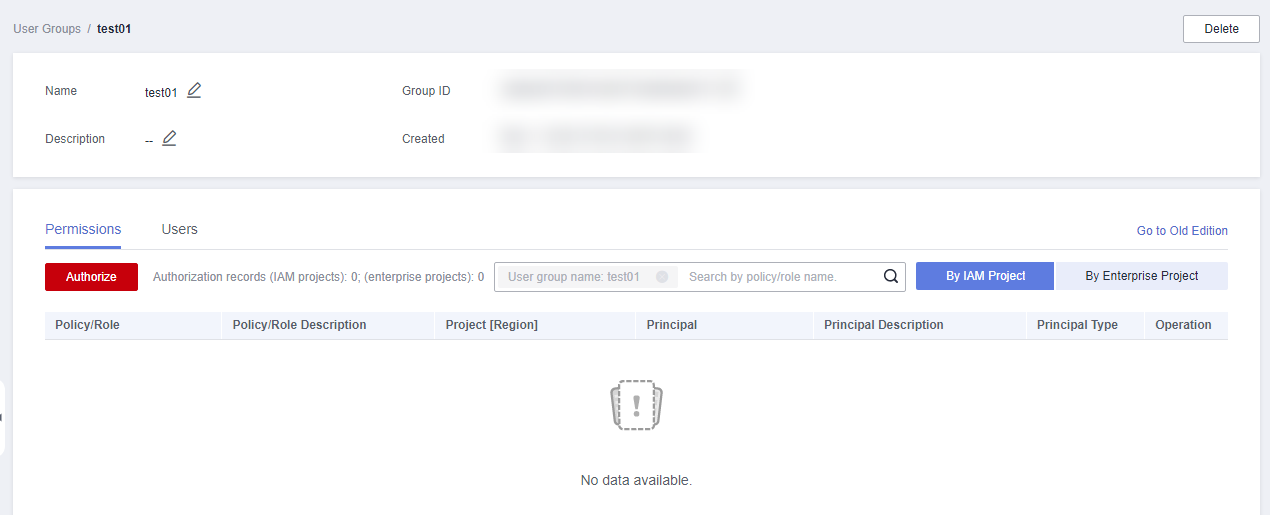
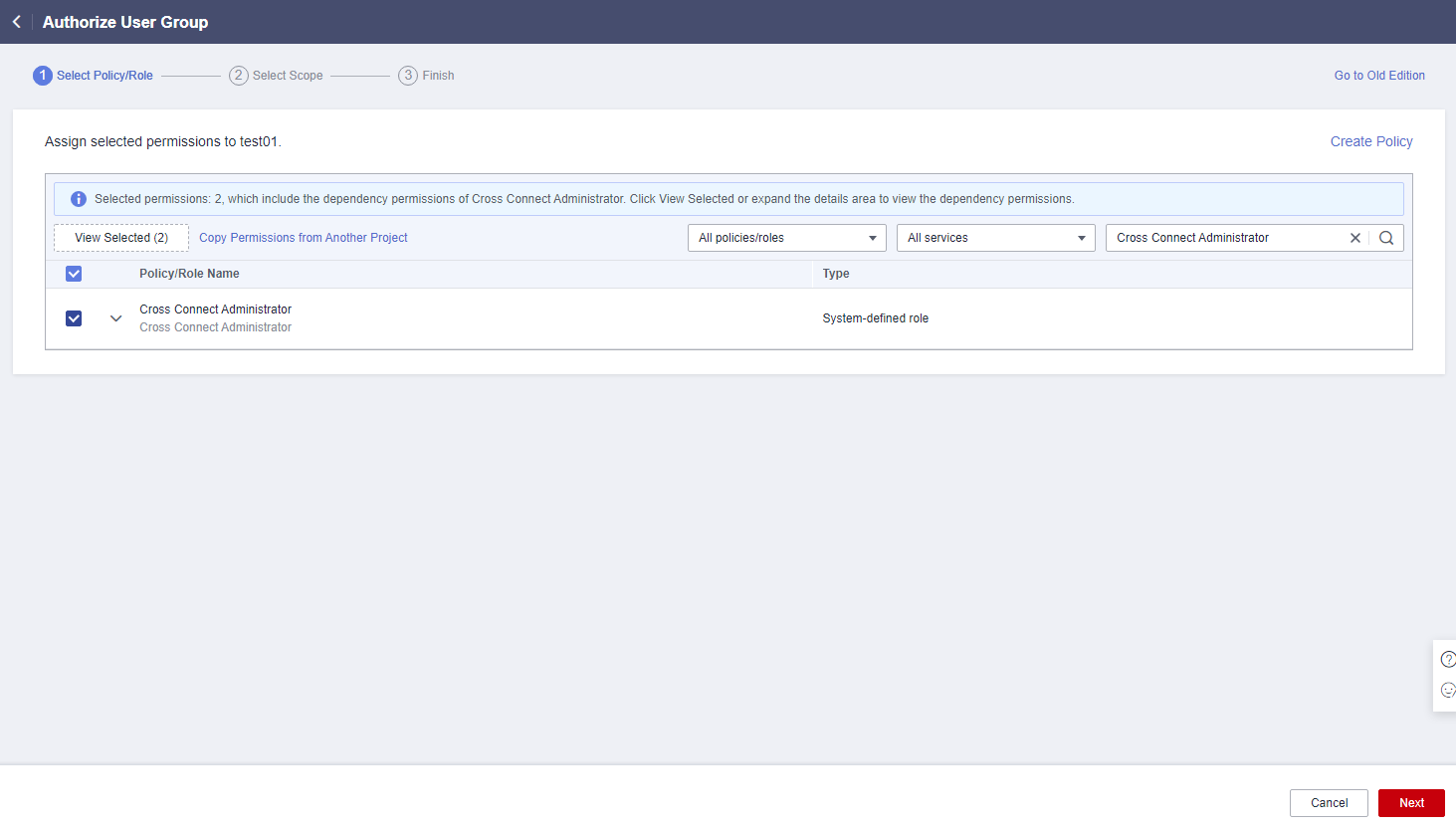
- Enter Cross Connect Administrator in the text box and click the search icon.
- In the search result, select Cross Connect Administrator and click Next.
Figure 5 Selecting a system-defined role
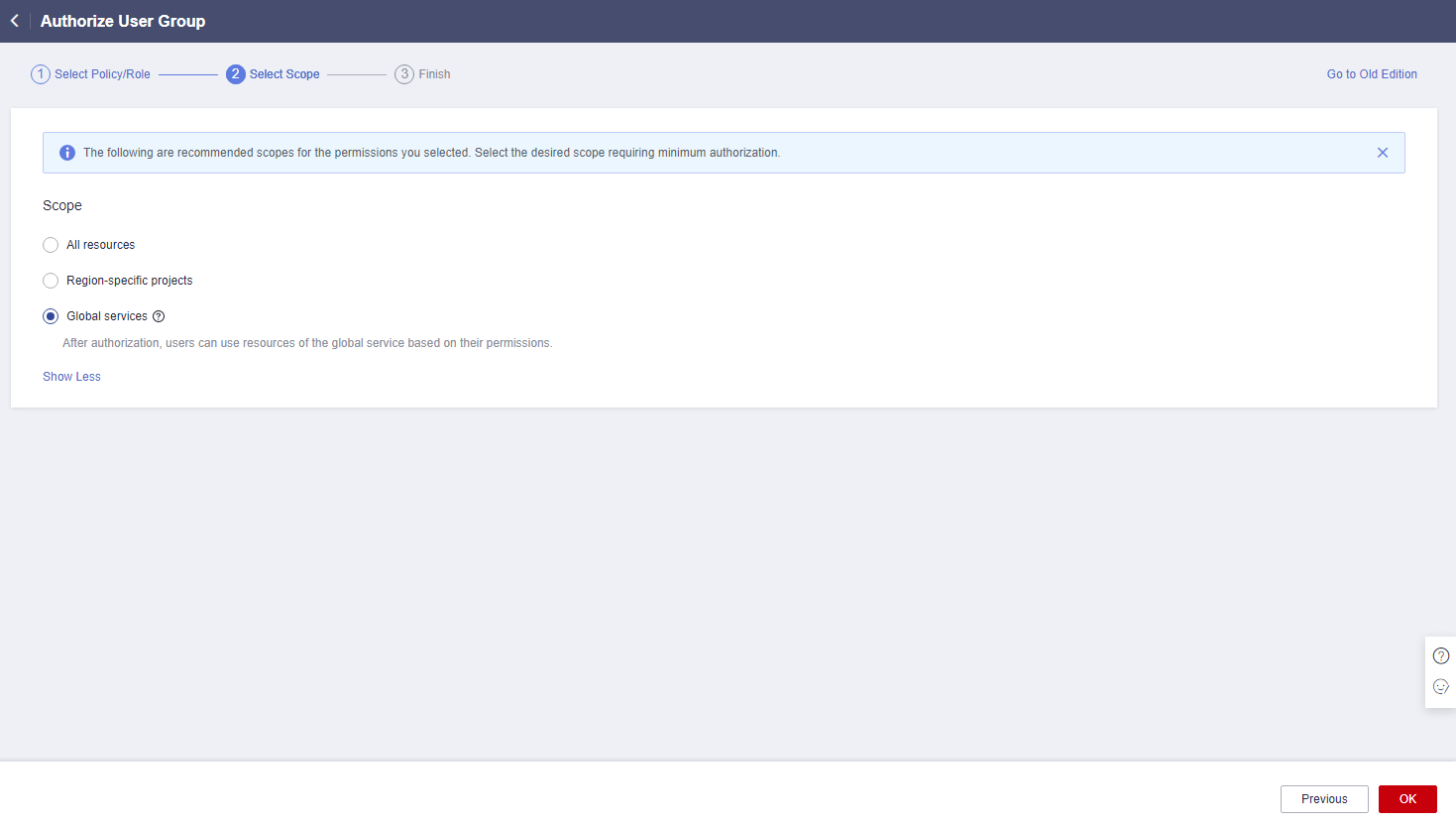
- Click Show More.
Figure 6 Scope

- Select Global services and click OK.
Figure 7 Global services
 If "Authorization successful" is displayed, the authorization is complete. The authorization will take effect about 15 to 30 minutes later.Figure 8 Authorization successful
If "Authorization successful" is displayed, the authorization is complete. The authorization will take effect about 15 to 30 minutes later.Figure 8 Authorization successful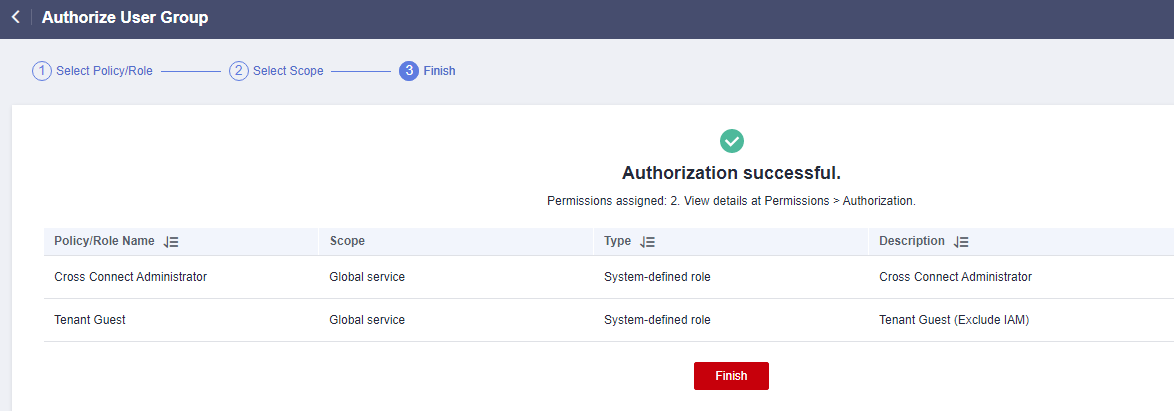
- Go back to the user group list, locate the created user group, and click Manage User in the Operation column.
Figure 9 Manage User
- Select the IAM user you want to add to the user group and click OK.
Example 2: Authorizing an IAM User to Use Cloud Connect in All Enterprise Projects
An IAM user needs to perform operations on Cloud Connect resources, such as network instances, bandwidth packages, inter-region bandwidths, and routes, in all enterprise projects. You can perform the operations below to grant the corresponding permissions to this IAM user.
To grant the permissions on cross-account authorization and cross-border permit application, perform the operations in Example 1: Allowing an IAM User Who Is Not in Any Enterprise Projects to Have All Cloud Connection Permissions.
- Log in to the management console.
- On the homepage, hover over the username in the upper right corner and choose Identity and Access Management from the drop-down list.
Figure 10 Identity and Access Management

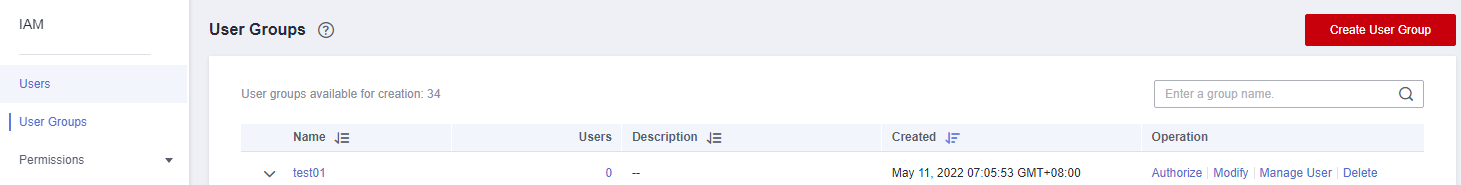
- In the navigation pane on the left, choose User Groups.
- In the upper right corner, click Create User Group.
Figure 11 Creating a user group
- Configure the parameters and click OK.
Figure 12 Configuring user group parameters

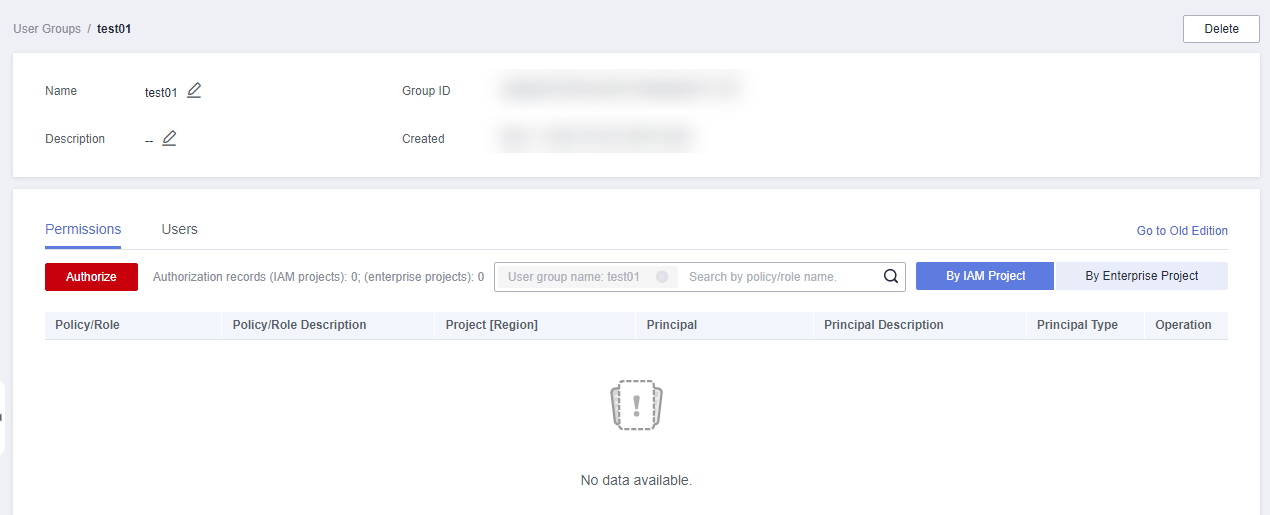
- Locate the created user group and click its name.
- Click By IAM Project on the right and then click Authorize.
Figure 13 Authorizing a user group
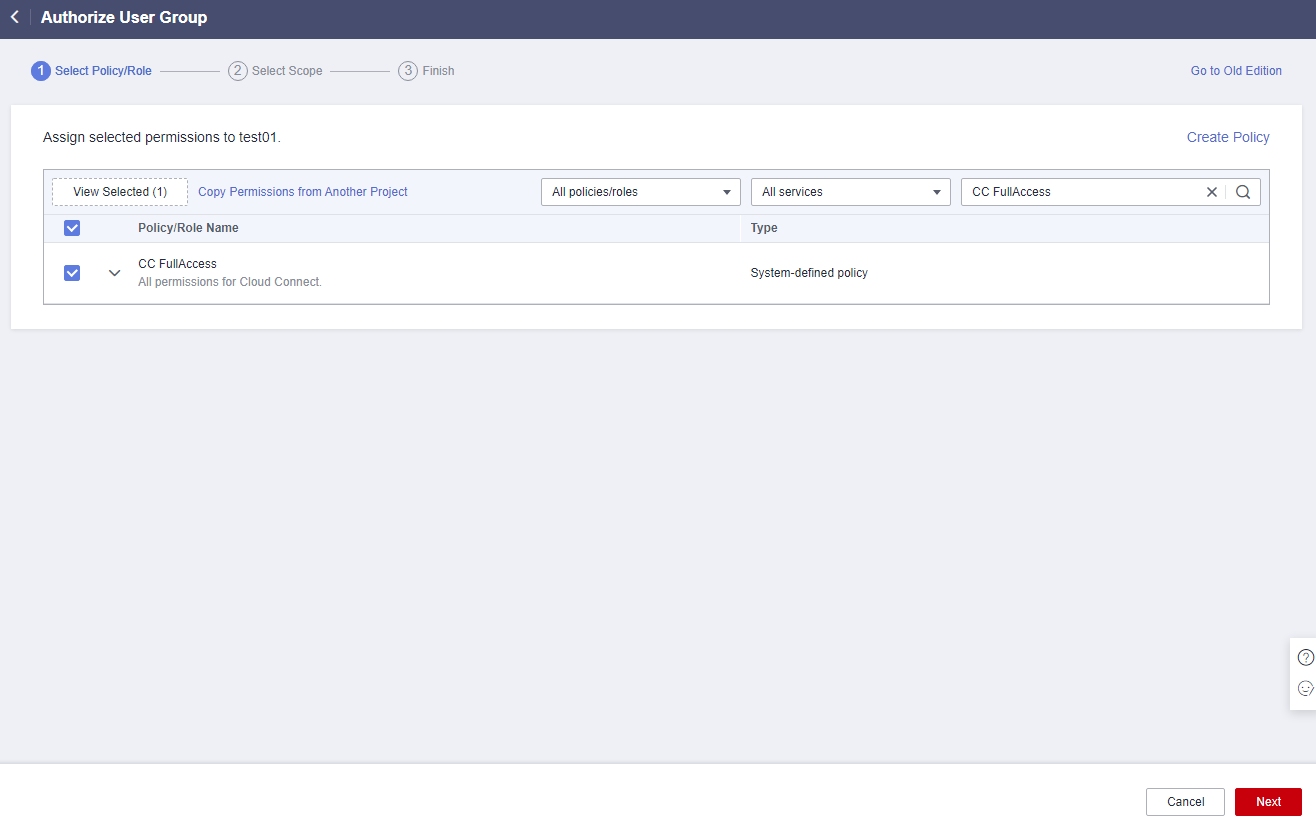
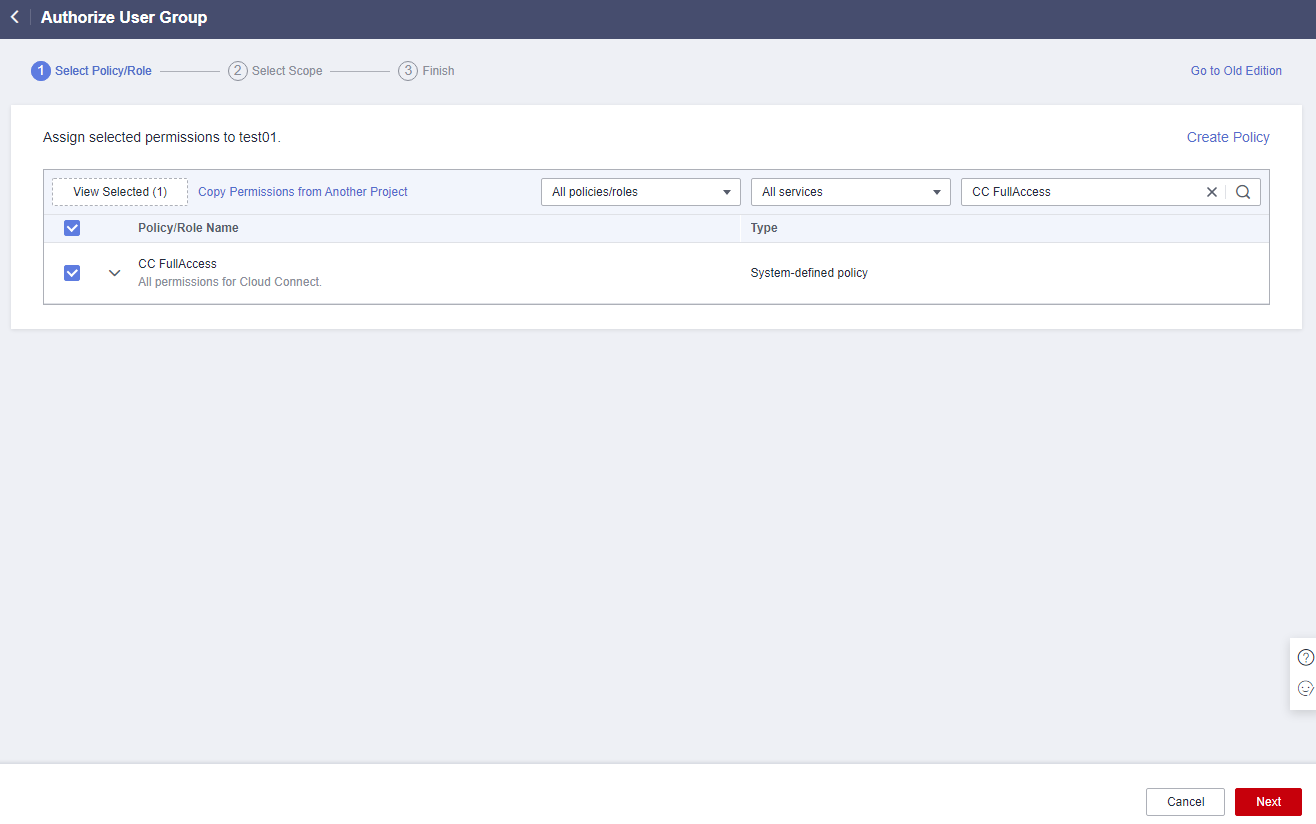
- Enter CC FullAccess in the text box and click the search icon.
- In the search result, select CC FullAccess and click Next.
Figure 14 Selecting a system-defined policy
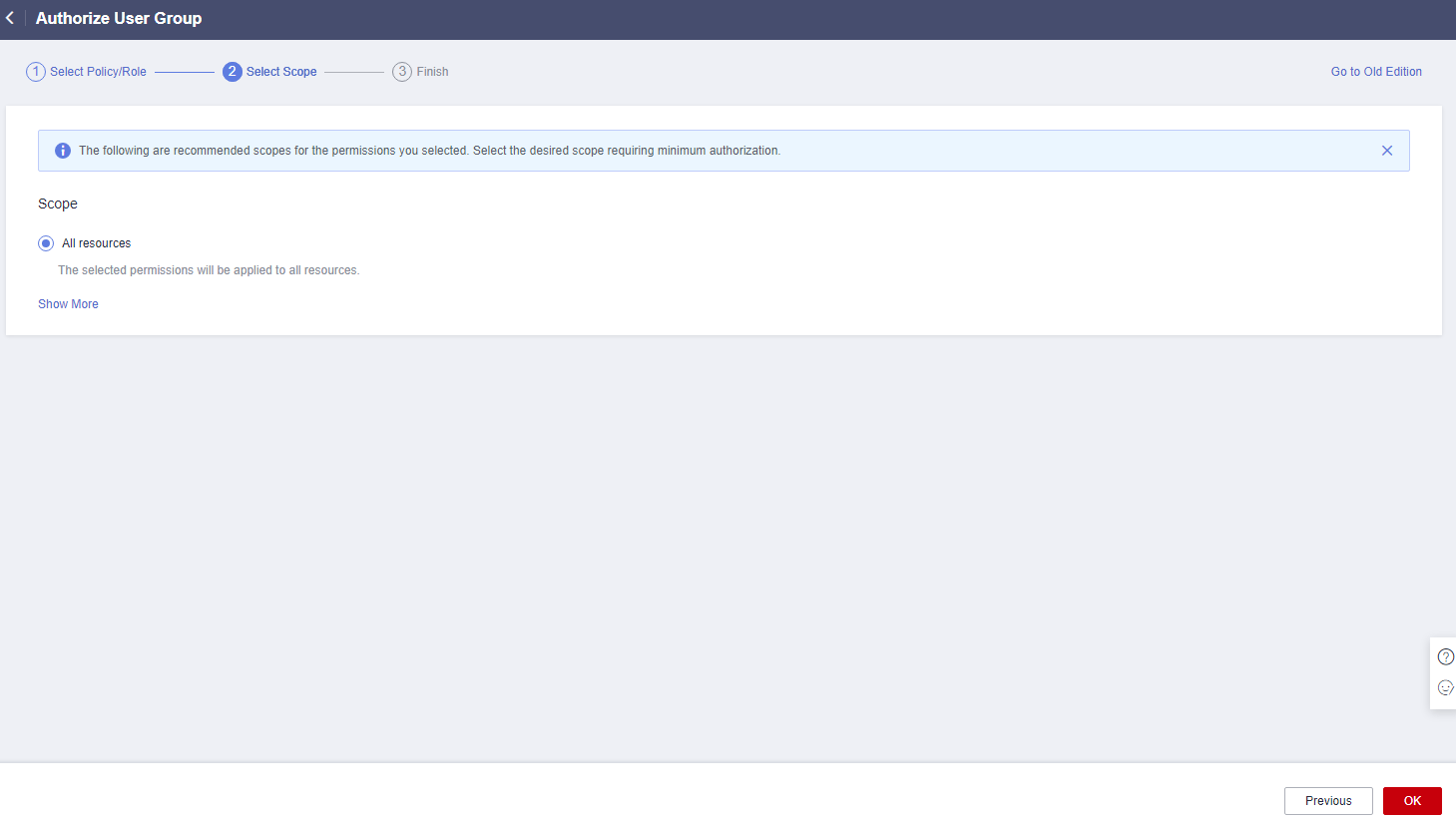
- Click Show More.
Figure 15 Scope
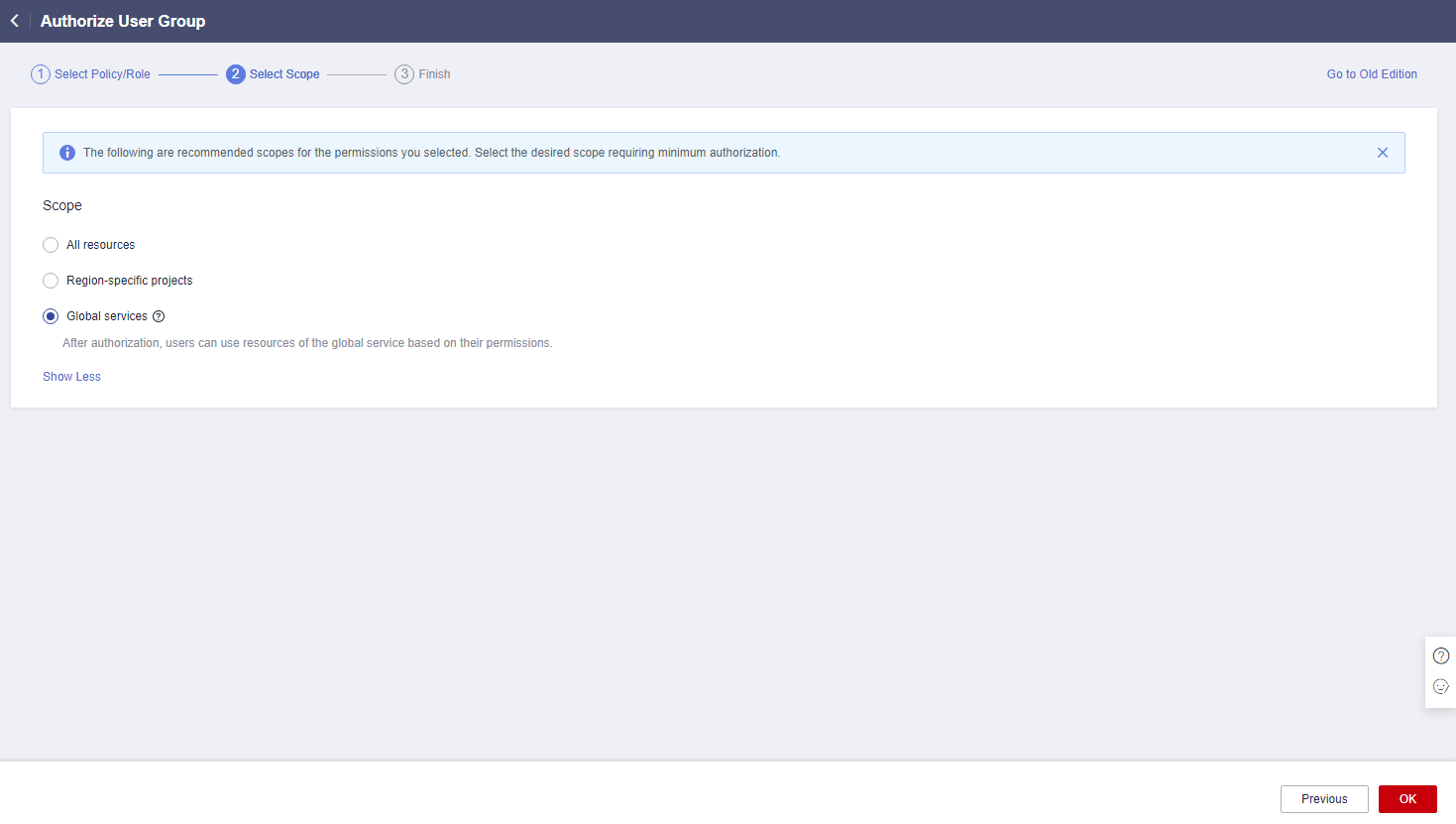
- Select Global services and click OK.
Figure 16 Global services
- Go back to the user group list, locate the created user group, and click Manage User in the Operation column.
Figure 17 Manage User
- Select the IAM user you want to add to the user group and click OK.
If the IAM user does not have VPC-related permissions, you can grant the CC Network Depend QueryAccess permissions for the user group that the IAM user belongs to and select All resources for Scope.
You can view the authorization in the Permissions tab.Figure 18 Permissions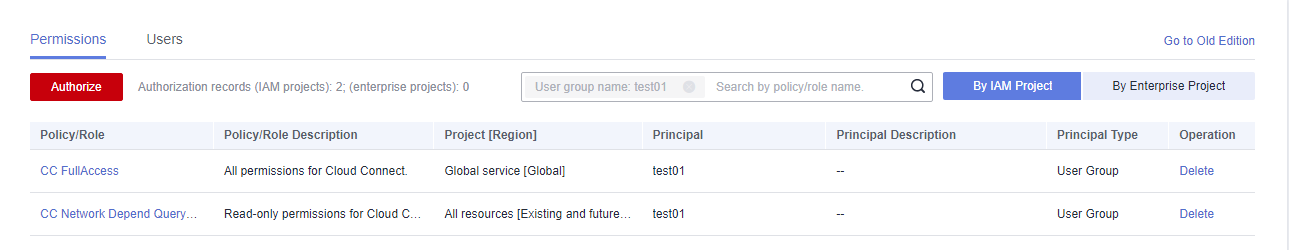
Example 3: Authorizing an IAM User to Use Cloud Connect in a Specific Enterprise Project
An IAM user needs to perform operations on Cloud Connect resources such as network instances, bandwidth packages, inter-region bandwidths, and routes, in specific enterprise projects. You can perform the operations below to grant the corresponding permissions to this IAM user.
To grant the permissions on cross-account authorization and cross-border permit application, perform the operations in Example 1: Allowing an IAM User Who Is Not in Any Enterprise Projects to Have All Cloud Connection Permissions.
- Log in to the management console.
- On the homepage, hover over the username in the upper right corner and choose Identity and Access Management from the drop-down list.
Figure 19 Identity and Access Management

- In the navigation pane on the left, choose User Groups.
- In the upper right corner, click Create User Group.
Figure 20 Creating a user group

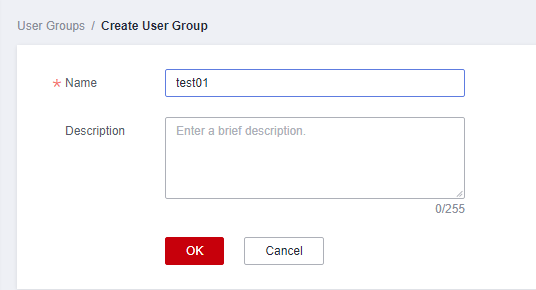
- Configure the parameters and click OK.
Figure 21 Configuring user group parameters
- Locate the created user group and click its name.
- Click By IAM Project on the right and then click Authorize.
Figure 22 Authorizing a user group
- Enter CC FullAccess in the text box and click the search icon.
- In the search result, select CC FullAccess and click Next.
Figure 23 Selecting a system-defined policy

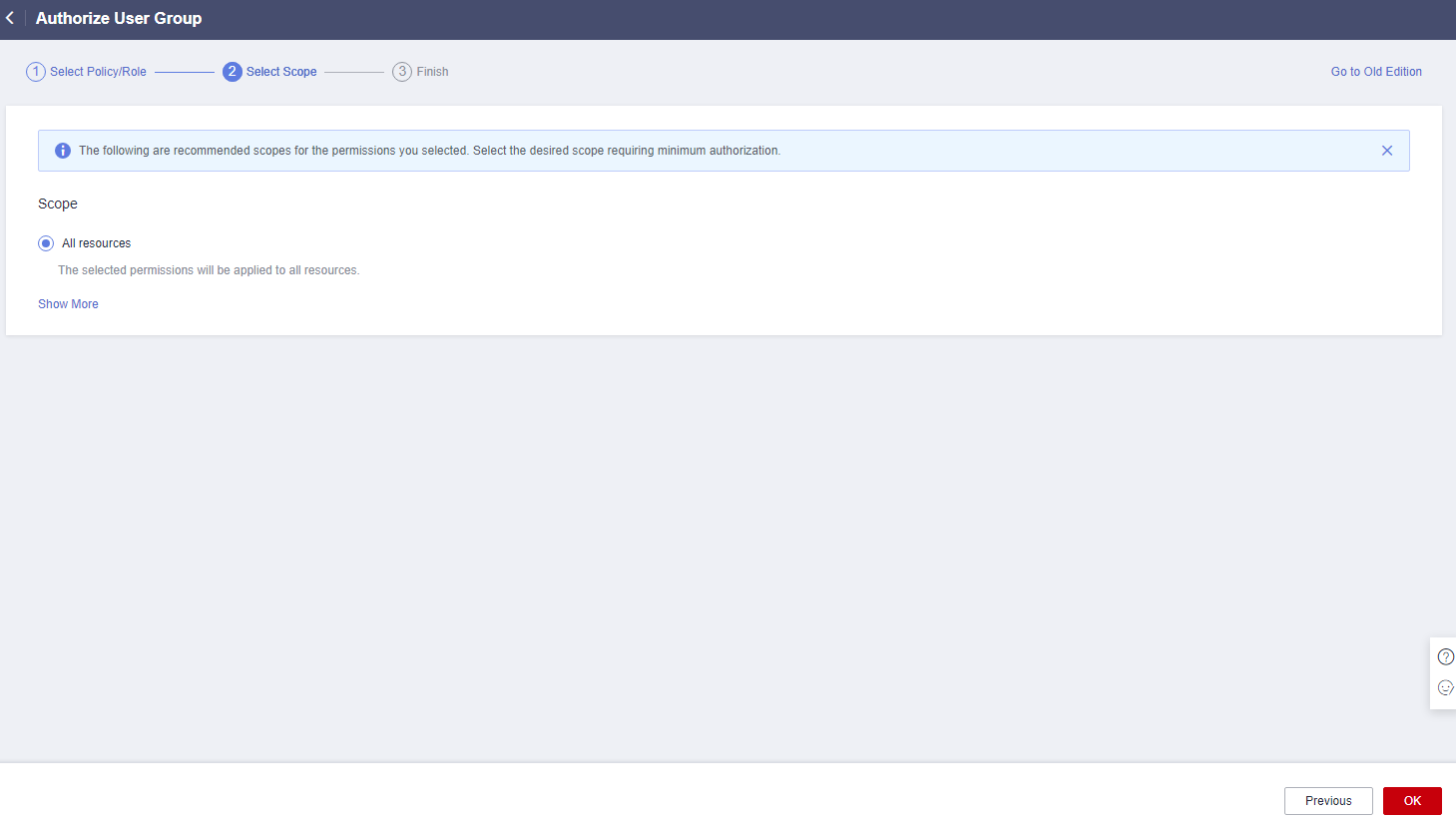
- Click Show More.
Figure 24 Scope
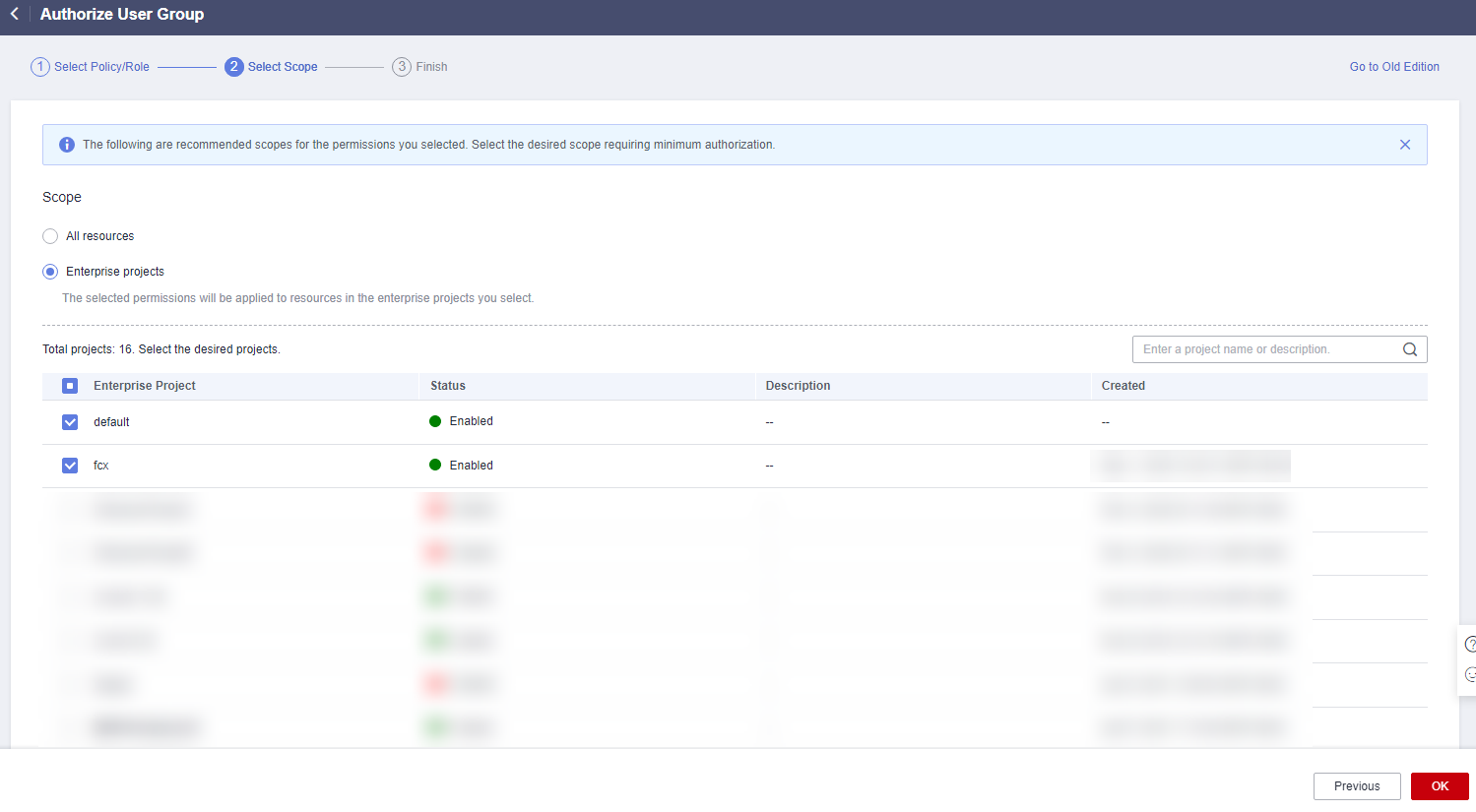
- Select Enterprise projects.
- Select an enterprise project and click OK.
Figure 25 Enterprise projects
- In the navigation pane on the left, choose Permissions > Policies/Roles.
Figure 26 Policies/Roles
- Click Create Custom Policy.
Figure 27 Creating a custom policy
- Configure the parameters based on Table 1.
Table 1 Custom policy parameters Parameter
Description
Policy Name
Specifies the name of the custom policy.
Policy View
- (Recommended) Visual editor
- JSON
Policy Content
- Select Allow.
- Cloud service: Cloud Connect
- Actions:
- ReadOnly: Select cc:networkInstances:get, cc:interRegionBandwidths:get, and cc:cloudConnectionRoutes:get.
- ReadWrite: Select the following:
cc:networkInstances:create
cc:interRegionBandwidths:update
cc:networkInstances:delete
cc:interRegionBandwidths:create
cc:interRegionBandwidths:delete
cc:networkInstances:update
- ListOnly: Select cc:cloudConnectionRoutes:list, cc:networkInstances:list, and cc:interRegionBandwidths:list.
- Configure other parameters and click OK.
- Repeat steps 3 to 7.
- Search for the created custom policy by name.
- Select the custom policy and click Next.
- Click Show More.
- Select Global services and click OK.
If the IAM user does not have VPC-related permissions, you can grant the CC Network Depend QueryAccess permissions for the user group that the IAM user belongs to and select All resources for Scope.
You can view the authorization in the Permissions tab.Figure 28 Authorization records in the IAM project view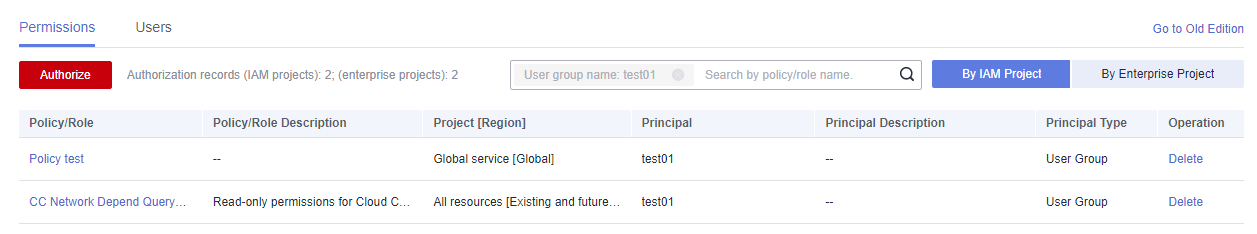 Figure 29 Authorization records in the enterprise project view
Figure 29 Authorization records in the enterprise project view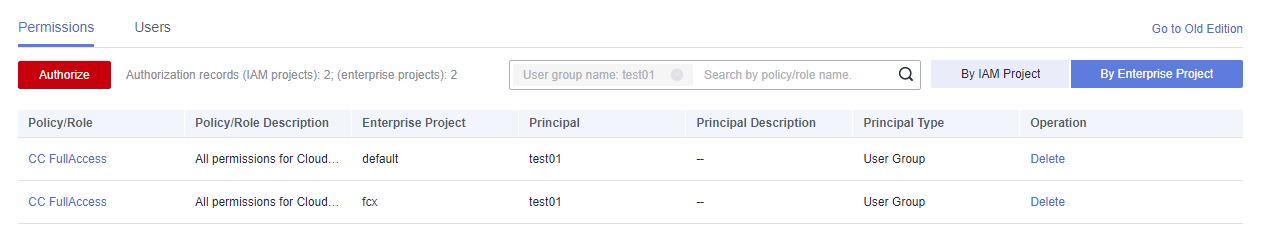
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





