Overall Network Architecture
The following figure shows the overall network architecture of Landing Zone. The network operations account functions as the network hub of the Landing Zone to centrally manage the border network ingress and egress and enable connections between VPCs across multiple accounts. Enterprise routers are deployed in the network operations account to interwork with VPCs of service accounts. This allows multiple accounts to communicate with the on-premises IDC through Direct Connect and VPN, and communicate with the Internet through the public NAT gateway. They can also communicate with accounts in other regions through Cloud Connect.
You can manage network resources in this account to reduce the management workloads and develop and implement unified network security policies. For example, you can deploy internet-oriented Advanced Anti-DDoS (AAD), CFW, and WAF services and configure specific security policies.
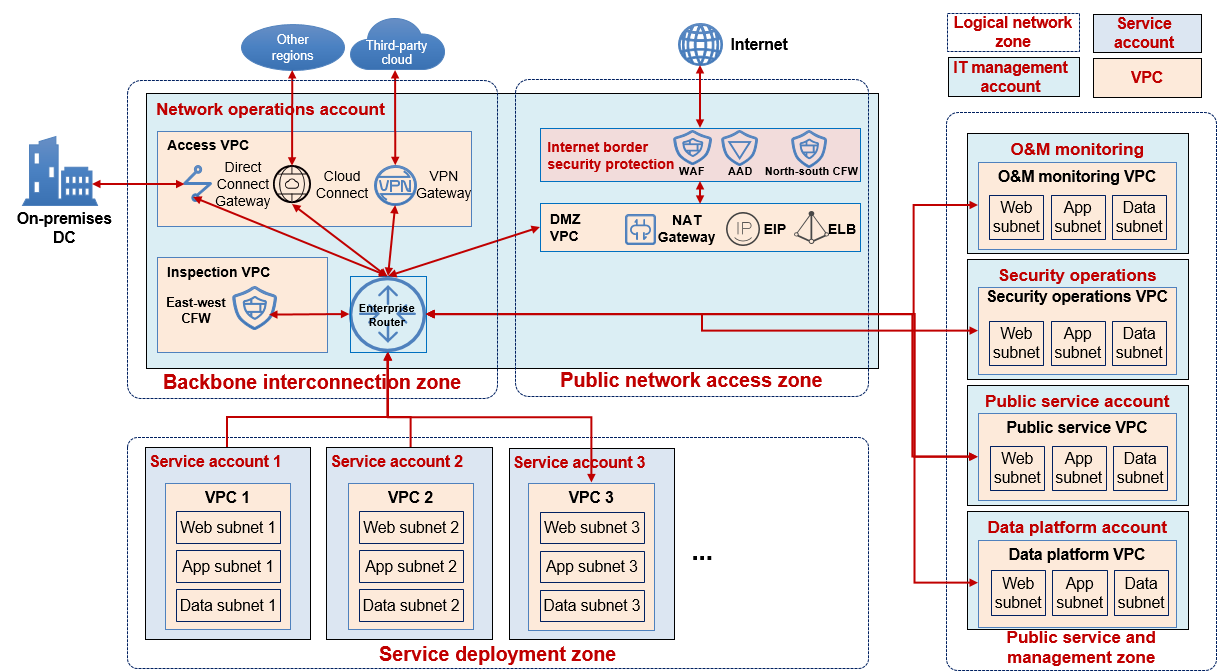
The Landing Zone network architecture consists of four logical network zones: backbone interconnection zone, public network access zone, service deployment zone, and public service and management zone.
Main Functions of the Backbone Interconnection Zone
- Centrally deploy enterprise routers to build network hubs for cloud and on-premises interconnection, multi-account and multi-VPC interconnection on the cloud, and cross-region interconnection on the cloud.
- Centrally deploy VPN or Direct Connect to interconnect the cloud with local data centers for all accounts.
- Centrally deploy Cloud Connect to interconnect with other regions on Huawei Cloud for all accounts.
- Centrally deploy VPN to interconnect with third-party clouds for all accounts.
Main Functions of the Public Network Access Zone
- Centrally set up demilitarized zones (DMZs) and deploy and maintain resources such as NAT Gateway, Elastic IP (EIP), proxy servers, and Elastic Load Balance (ELB) to provide Internet access capabilities for other accounts.
- Deploy security services such as WAF, CFW, and Anti-DDoS to protect Internet connection resources.
- Expose explicit IP addresses and ports, prohibit other ports, and terminate public networks.
Main Functions of the Service Deployment Zone
- Create VPCs and subnets and deploy cloud resources required by service systems.
- Divide VPCs for different operating environments, such as production, development, and test environments.
- Divide subnets for the layers of the application architecture, including web, application, and data subnets.
Main Functions of the Public Service and Management Zone
- Create VPCs and subnets and deploy cloud resources required by the public services and IT management systems. Public services include Active Directory (AD), Domain Name System (DNS), file systems, Object Storage Service (OBS) buckets, and data platforms. IT management systems include O&M and security management systems.
- Divide VPCs for different operating environments, such as production, development, and test environments.
- Divide subnets for the layers of the application architecture, including web, application, and data subnets.
The core of this network architecture is the network operations account, which serves as the network hub for connecting other accounts. Other accounts must communicate with each other through the enterprise router of this account. Huawei Cloud organizes the connectivity matrix between VPCs in each account according to the following assumptions and account responsibilities. With this matrix, you can then configure routing rules on the enterprise router to control communication between VPCs.
- The O&M monitoring account needs to maintain resources in third-party clouds and local DCs.
- The security operations account needs to obtain system patch packages from the public network.
- The data platform needs to obtain data from third-party clouds and local DCs.
- The DevOps account needs to download code from GitHub and deploy software artifacts to each service account.
- The public service account needs to connect to the local IDCs.
- The production, development, and test environments must be isolated from each other.
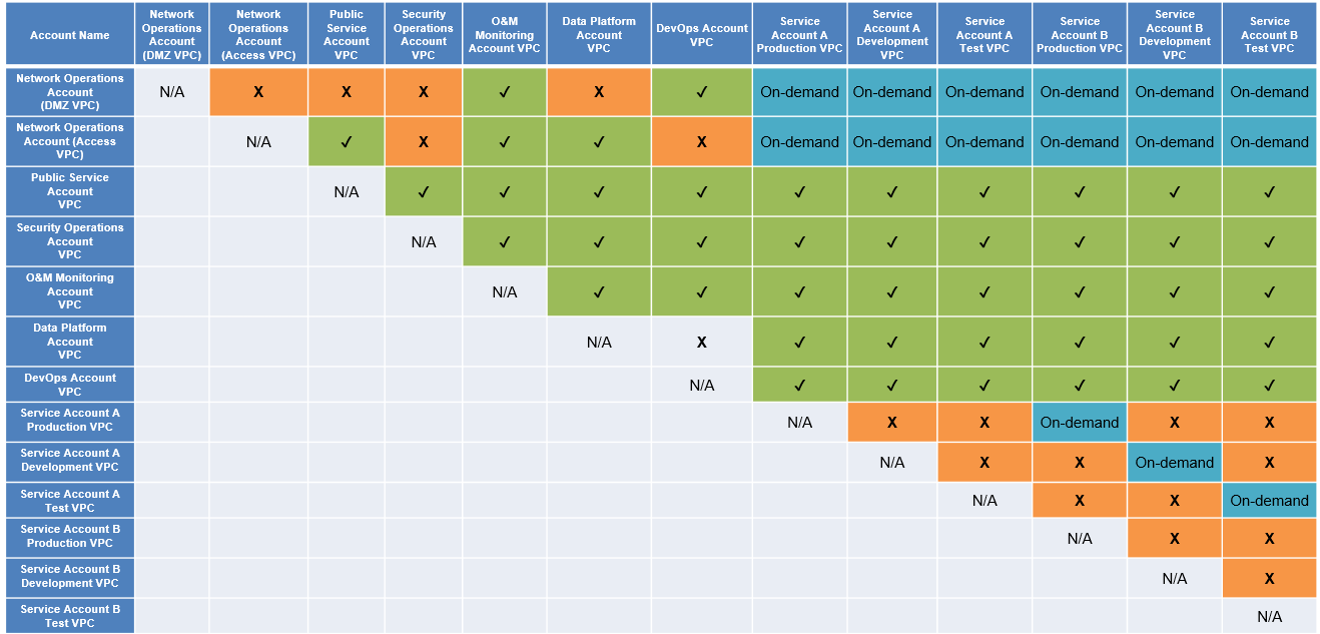
The logging account is used to centrally store audit logs and run logs through Huawei Cloud Cloud Trace Service (CTS), Log Tank Service (LTS), and OBS. These services do not have IP addresses for the tenant plane, so you do not need to interconnect this account with VPCs of other accounts. A sandbox account is used to test Huawei Cloud resources and control policies, including VPC functions and connectivity with other accounts. Therefore, you do not need to preconfigure the connection between this account and other accounts in enterprise router.
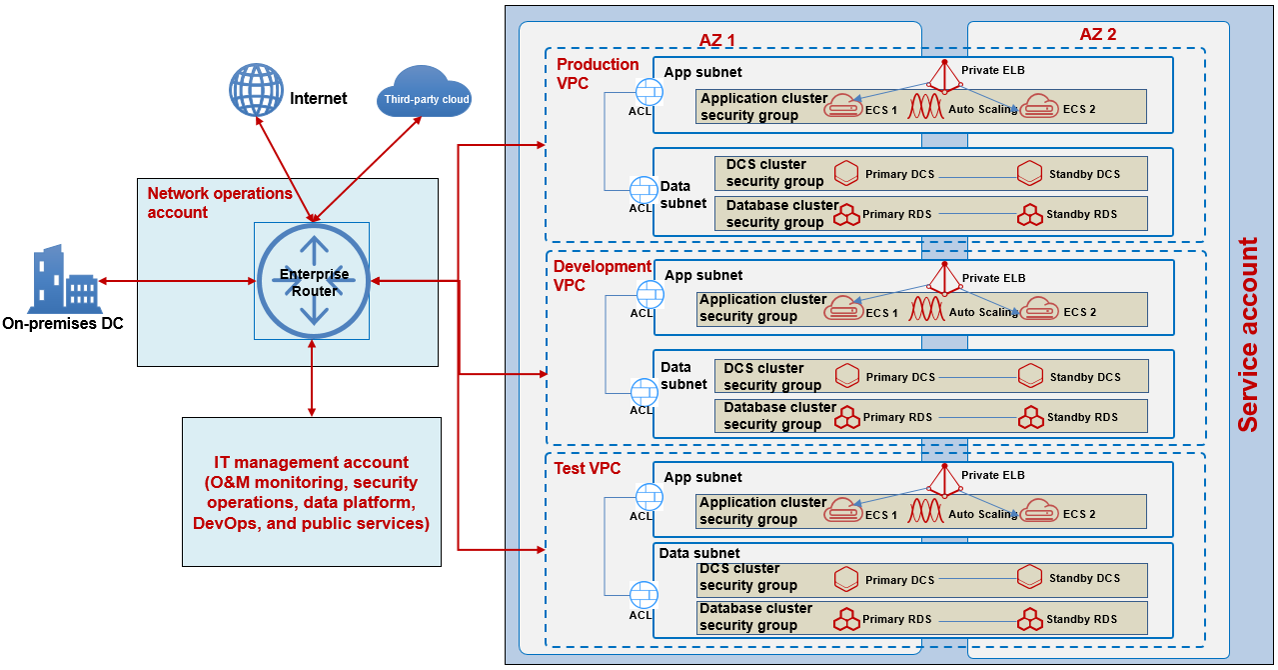
If a service system has an independent account and the production and non-production environments do not need to be strictly isolated, you are advised to create separate VPCs (production VPC, development VPC, and test VPC) for different operating environments of the service system. You need to deploy at least two subnets for each VPC: application subnet for the application layer and data subnet for the data layer. You can use network ACLs to control access between subnets. You can also add cloud servers and Relational Database Service (RDS) resources to security groups and configure security group rules for instance-level access control. You can deploy application server clusters across availability zones (AZs) to achieve high availability for applications, and use Huawei Cloud active/standby database clusters and cache clusters across AZs to achieve high availability for data use. The following figure shows an example.
If multiple service systems use the same member account, you are advised to create three independent VPCs which are isolated from each other in the account: production VPC, development VPC, and test VPC. These service systems are deployed in these VPCs and isolated by subnets. Each service system has an independent application subnet and data subnet. You can create ACLs for these subnets to control internal network traffic between different subnets, as shown in the following figure.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





