Using Advanced Protection Policies to Restrict Abnormal Connections
If an origin server IP address frequently sends a high volume of abnormal connection packets within a short period, you can set up an advanced protection policy to blacklist the origin server IP address for a certain period. Access from it can be restored once the blacklist period ends.
Limitations and Constraints
The advanced protection function is still in the open beta test (OBT) phase. This function is supported only by Unlimited Protection Advanced Edition instances in some regions. You can submit a service ticket to enable this function.
Enabling Advanced Protection
- Log in to the AAD console.
- In the navigation pane on the left, choose . The Protection Policies page is displayed.
- Click Create Protection Policy.
- In the displayed dialog box, set the policy name, select an instance, and click OK.
Figure 1 Creating a policy

- In the row containing the target policy, click Set Protection Policy in the Operation column.
- In the Connection Protection area, click Set.
Figure 2 Advanced protection
- Click the Abnormal Connection Defense tab and set abnormal connection defense parameters.
Figure 3 Abnormal connection defense
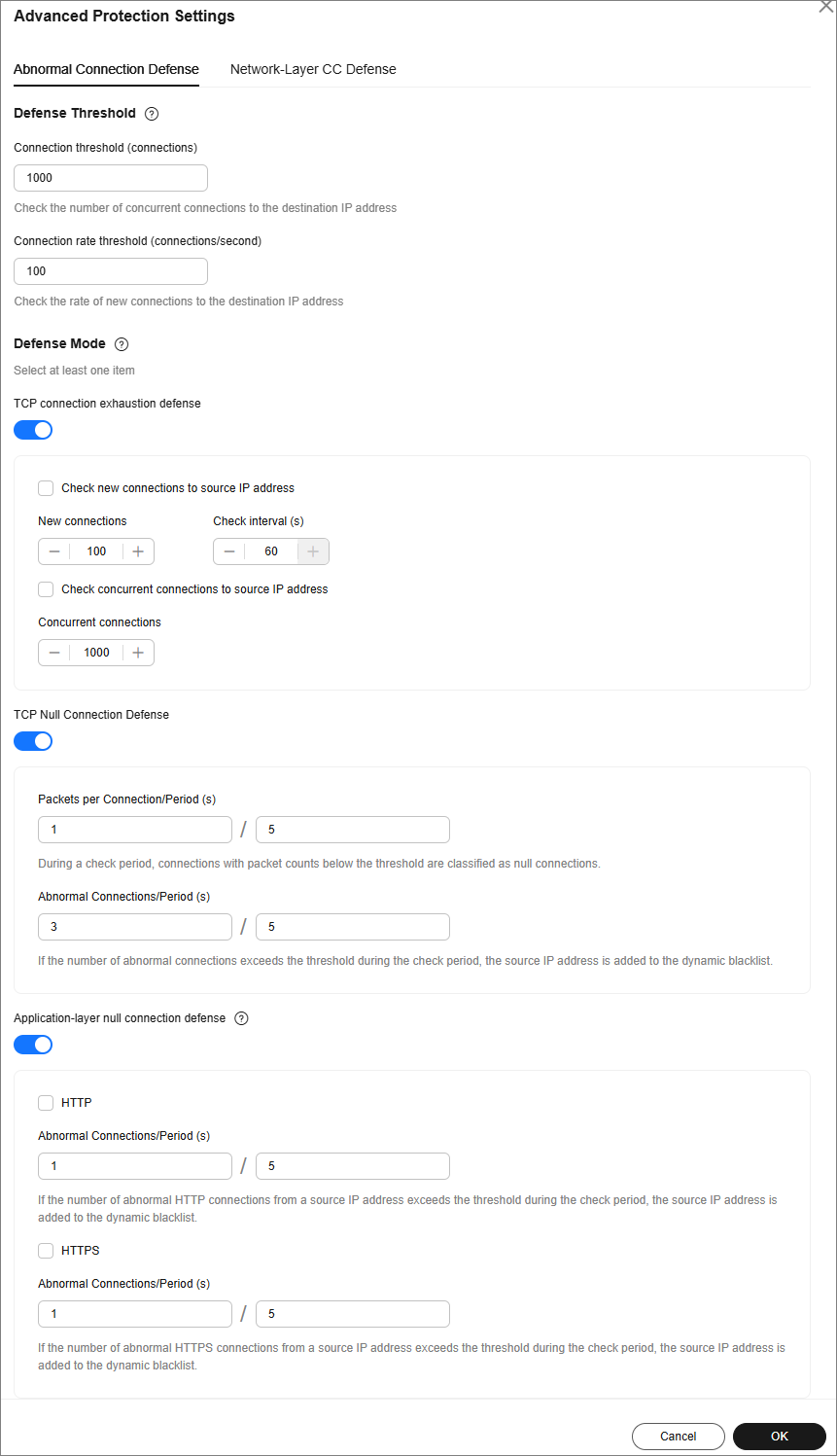
Table 1 Parameters for abnormal connection defense Type
Parameter
Description
Detection Threshold
Check the number of concurrent connections to the destination IP address.
When the number of the concurrent TCP connections of a destination IP address exceeds Connection threshold, defense against connection flood attacks is started. After the defense is started, the source IP address starts to be checked.
Check the rate of new connections to the destination IP address.
When the number of the new TCP connections per second of a destination IP address exceeds the Detection Threshold, defense against connection flood attacks is started. After the defense is started, the source IP address starts to be checked.
Defense Mode
TCP connection exhaustion defense
After TCP connection exhaustion defense is enabled, the following parameters can be set:
- Check new connections to source IP address: The system checks for new connections to the source IP address at regular intervals. If the number of new connections exceeds the specified threshold within the specified interval, the origin server's IP address is blocked until the block period ends.
- Check concurrent connections to source IP address: If the number of concurrent TCP connections from an IP address exceeds the specified threshold, the IP address is temporarily blocked. Access resumes once the block period ends.
TCP Null Connection Defense
After TCP Null Connection Attack Defense is enabled, the following parameters can be set:
- Packets per Connection/Period (s): If the packet transmission count falls below the specified threshold within a check period, the connection is classified as null or empty.
- Abnormal Connections/Period (s): If the number of abnormal connections falls below the specified threshold within a check period, the source IP address is added to a dynamic blacklist.
Application-layer null connection defense
After Application-layer null connection defense is enabled, you can set the following parameters:
- HTTP: The system monitors HTTP connections for each source IP address. If the number of connections exceeds the specified threshold, the system blocks access from that IP address by adding it to the blacklist. Access is automatically restored when the block period ends.
- HTTPS: The system monitors HTTPS connections for each source IP address. If the number of connections exceeds the specified threshold, the system blocks access from that IP address by adding it to the blacklist. Access is automatically restored when the block period ends.
- Click OK to save the settings.
- Click the Network-Layer CC Defense tab and set CC attack defense parameters.
Figure 4 Network-layer CC defense
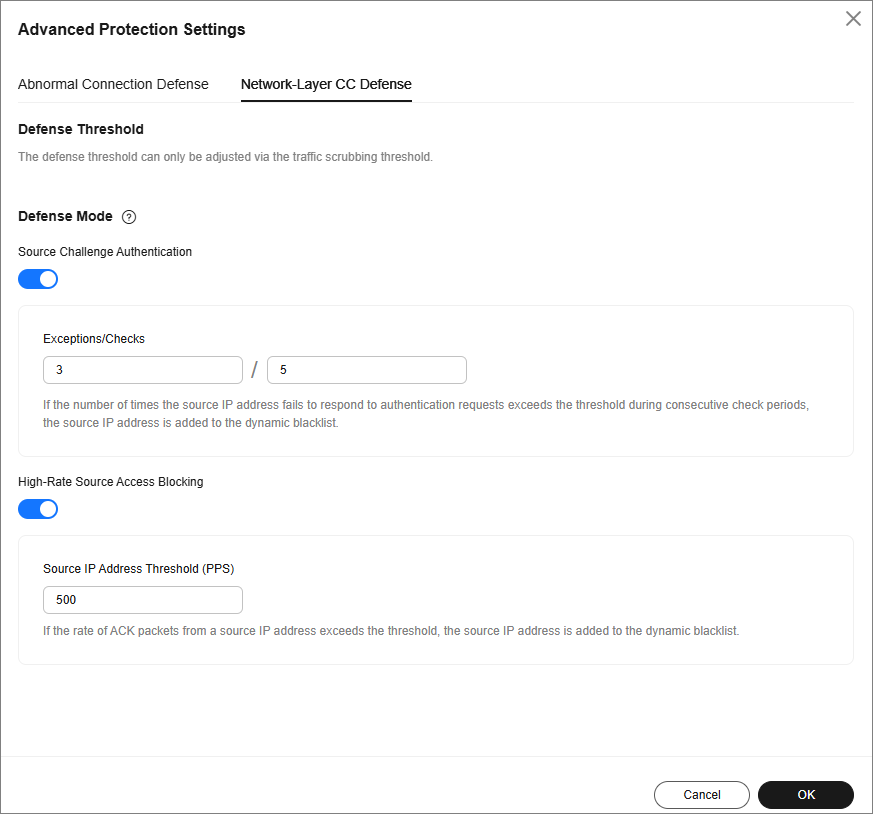
Table 2 Parameters for network-layer CC attack defense Type
Parameter
Description
Defense Threshold
-
The defense threshold can only be adjusted via the traffic scrubbing threshold. When connections to a destination IP address reach either one of the following thresholds, TCP connection defense is enabled.
Defense Mode
Source Challenge Authentication
If the source IP address fails to authenticate consecutively for a predetermined number of times across multiple check periods, exceeding the defined threshold, it will be dynamically blacklisted.
High-Rate Source Access Blocking
If the rate of ACK packets received from a source IP address surpasses the predetermined threshold, the source IP address is dynamically blacklisted.
Feedback
Was this page helpful?
Provide feedbackThank you very much for your feedback. We will continue working to improve the documentation.See the reply and handling status in My Cloud VOC.
For any further questions, feel free to contact us through the chatbot.
Chatbot





